Learn. Do. Teach.
The Agilicus blog follows our learning and observations.
We learn something.
We then do that thing.
We then teach about how we did it.
All Blog Posts
Below is the historical list of all blog posts, all categories, sorted by time newest first.
-
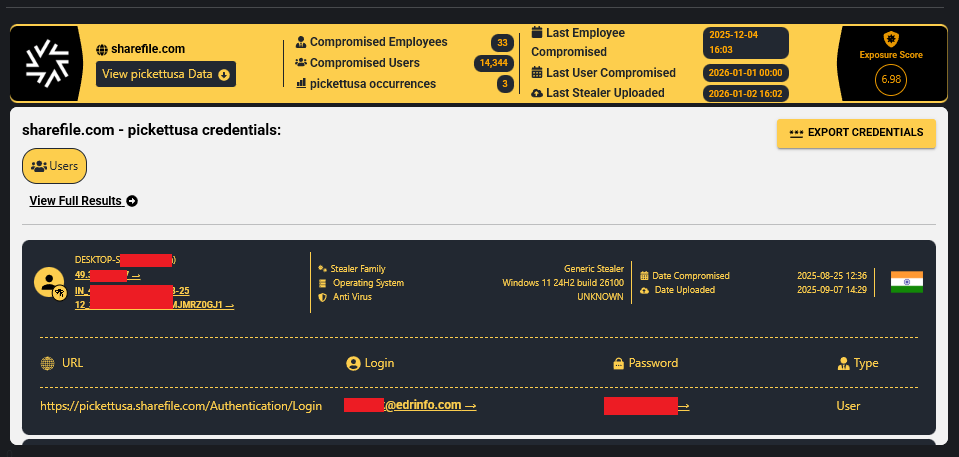
Pwned Plans and Porous Perimeters
A breach at Pickett & Associates exposes critical infrastructure blueprints, proving that engineering firms are the new attack vector. Learn why ‘boring’ data is a military target and why MFA is non-negotiable.
-

Porous Perimeters and Pro-Russian Pwning: The La Poste Lesson
Pro-Russia hacktivists like Z-Pentest are moving from annoying DDoS attacks to dangerous OT compromises in France and Denmark. Don Bowman explains why your air gap is a lie and how to actually secure critical infrastructure.
-

Ransomware Reservoirs: Another Leak in the Critical Infrastructure Dam
Romanian water infrastructure just lost 1,000 systems to ransomware. While authorities claim operations are safe, the shift to manual radio comms proves our critical infrastructure defences are failing. It is time to ditch the air gap myth for real Zero Trust security.
-

The Fragility of Interdependence: Securing the Industrial Mesh
The £1.9bn JLR breach exposed supply chain fragility. Download the Agilicus whitepaper to learn how Zero Trust secures the industrial mesh against cyber threats.
-
2026 Pwned by Progress: The Year Your Air Gap Finally Evaporates
It is 2026 and your new OT hardware demands an internet connection. Discover why this kills the air gap, breaks your firewall, and why Identity-Aware Proxies are the only path to safety.
-

Same Old Shenanigans: The MITRE 2025 Top 25 List
MITRE has released the 2025 CWE Top 25 list, and it is a stark reminder that software is still porous. We analyse the rise of authorization failures and the return of buffer overflows.
-

When Skynet Meets the Assembly Line CISA’s New Playbook
Navigating the new guidance on mixing artificial intelligence with industrial control systems without blowing anything up It feels like just yesterday we were worried about connecting a PLC to the skynet.
-

Digital Disenfranchisement: Stop Treating Your Frontline Like Second-Class Citizens
Are your bus drivers and contractors stuck using paper because IT can’t secure their devices? It’s time to stop the ‘Digital Disenfranchisement’ and use Zero Trust to safely connect everyone, everywhere.
-

SEC Shockwaves: Manufacturing Misery and the Materiality Mandate
The SEC’s new 4-day disclosure rule is a wake-up call for manufacturing. Is your OT network ready to report a material breach, or are you staring into a black box of legacy tech?
-

Subprime Software: The Hidden Risks in Your Supply Chain
The Apache Tika CVE-2025-66516 is a perfect 10 for risk and a wake-up call for the industry. Like the 2008 financial crisis, toxic assets are hidden deep in your software stack. Learn why your security appliances might be your biggest weakness and how Zero Trust limits the blast radius.
-

Russian Roulette: Gambling with Critical Infrastructure and VNC
CISA warns of Pro-Russia hacktivists targeting VNC in critical infrastructure. We argue these are state-sponsored threats and explains why your firewall isn’t enough to stop them.
-
Quartered and Drawn: The SANS 2025 Reality Check
22% of operational technology environments were breached last year. 40% resulted in total operational shutdowns. We aren’t talking about website glitches; we’re talking about stopping pumps. I broke down the SANS 2025 report to explain why the odds are against you, and how to prepare
-

The Distributed Dilemma: Securing Renewable Energy in the Middle of Nowhere
Renewable energy sites are remote, distributed, and hard to secure. From Starlink struggles to contractor chaos, learn why Zero Trust is the only way to protect the modern grid.
-

The 4-Day Warning: New SEC Cyber Rules Hit the Factory Floor
Consequently, trying to scope an attack in a sprawling operatioanl tech network is like trying to find a needle in a haystack, except the haystack is currently on fire, and you are not allowed to use water because it might short-circuit the only machine that is still running.
-

The SEC Clock Is Ticking for Manufacturing
New SEC rules require public companies to disclose material cybersecurity incidents within four days. For manufacturers relying on complex industrial control systems, this timeline presents a massive challenge in visibility and reporting.
-

Cleaning Up the Mess: How One Disgruntled Contractor Trashed a Network (And How to Stop It)
An ex-contractor’s revenge cost a firm $862K. This cybersecurity story reveals a critical flaw in vendor access and how to prevent it.
-
Agilicus Ready for the Quantum Leap: Securing Today’s Gear from Tomorrow’s Threats
It’s a tale as old as time: we build a better lock, and someone, somewhere, starts building a better lock-pick. In the digital world, we’re on the cusp of a […]
-

Ditch the Digital Ostrich: How Zero Trust is Saving Municipalities (and Their Wallets) from Cyber Chaos
Facing rising cyber insurance costs? For municipalities, risky VPNs are a major hurdle. Learn how Zero Trust secures systems and lowers insurance risk.
-

Stop Saying “It’s the Customer’s Choice” – It’s Costing You Money
As a system integrator, do you say remote access is “the customer’s choice”? This common refrain, while well-intentioned, is an outdated view that’s costing you money. It’s time to shift from a cost-plus model to a more profitable, secure, and scalable managed service offering for your clients.
-

Your Air Gap is a Lie, and Other Inconvenient Truths About Industry 4.0
For years, the security model for water systems has been the air gap—a mythical wall where everything inside is trusted and everything outside is not. The problem? That air gap already has a bunch of holes in it, and Industry 4.0 is making more.
-
You Have a Login, But You Shall Not Pass: The Magic of Fine-Grained Authorisation
Authentication gets you in the door, but fine-grained authorisation decides which rooms you can enter. This principle ensures users access only the specific resources they need, making your systems more secure by rendering everything else invisible to them.
-
Houston, We Have Two Internets… and That’s a Problem?
You got a backup internet connection for your industrial plant, but now you have a new problem. How do you actually use it? Its different Internet Protocol address and lack of inbound support create a headache. Before you get tangled in a complex solution, there’s a simpler way to achieve seamless, active-active failover.
-
From Tunnels to (Zero) Trust: The Evolution of Industrial Remote Access
How do you grant secure remote access to your plant floor? While VPNs and jump boxes are common, they introduce serious security risks and operational headaches. We explore the four key methods, from traditional tunnels to modern Zero Trust, and reveal why an identity-aware approach is faster, simpler, and fundamentally more secure.
-

Who Moved My Air Gap? The Slow Boiling Future of Industrial Security
For decades, industrial security relied on the “air gap.” But like a frog in slowly boiling water, we’ve missed the gradual erosion of this protection. Today, that gap is more like Swiss cheese, full of holes for vendor access and cloud connectivity. It’s time to adapt to this new reality.
-

AI-Powered Cyber Threats: Protecting Your Critical Infrastructure
AI amplifies cyber risks for critical infrastructure, making attackers more effective. CISA’s FY23 report shows 80% of successful attacks exploit identity weaknesses like valid accounts and spearphishing. AI isn’t creating new vulnerabilities, but leveraging existing ones. Implementing Zero Trust and universal Single Sign-On significantly reduces these risks, making organizations a harder target.
-
The Paradox of Trust: Navigating Certificate Revocation in Air-Gapped Networks
The peculiar and particular problem of certificate revocation in semi or fully air-gapped networks—a challenge that pits the need for security against the very isolation designed to create it.
-

AI: The New Frontier for Cybercriminals Targeting Critical Infrastructure
AI: You don’t need to outrun the bear (the most sophisticated attacker in the world); you just need to outrun your neighbour. Let’s make sure you’re not the slowest hiker in the woods.
-

Apache Tomcat: Stealthy Risk Vector
Apache Tomcat. It is an everywhere middleware. And, quelle surprise, the time from disclosure to use is a day. Like log4j it will be with us for some time, so, time for some defence in depth.
-

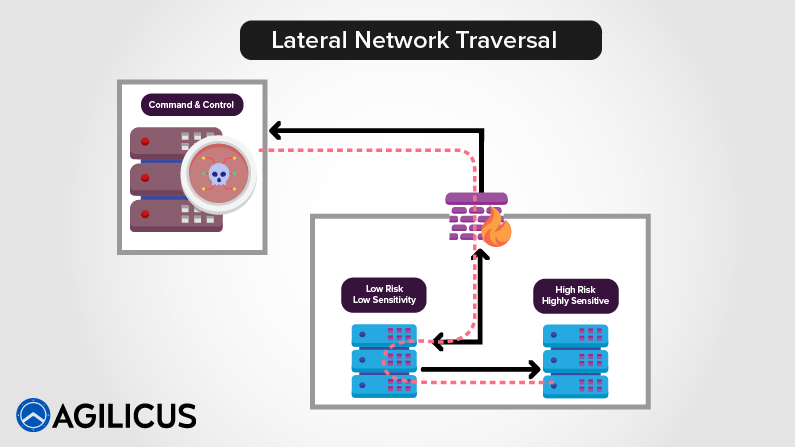
Many Headed Hydra Medusa Meets Critical Infrastructure
Medusa ransomware infected more than 300 entities in critical infrastructure. Living off the land avoids detection, facilitates lateral traversal.
-

It’s Been 0-Days Since The Last Municipal Cyber Security Attack
Asymmetric warfare: Big governments attack little governments. Attackers need to be right once, defenders need to be right 24x7x365. Municipalities continue to be a target.
-

CN APT Use VPN CVE for ICS in OT: Acronym Much?
Asymmetric Cost Espionage: A Chinese Advanced Persistent Thread actor used CVE-2024-24919 (a vulnerability in Checkpoint VPN) to gain ongoing access into operational technology networks.
-
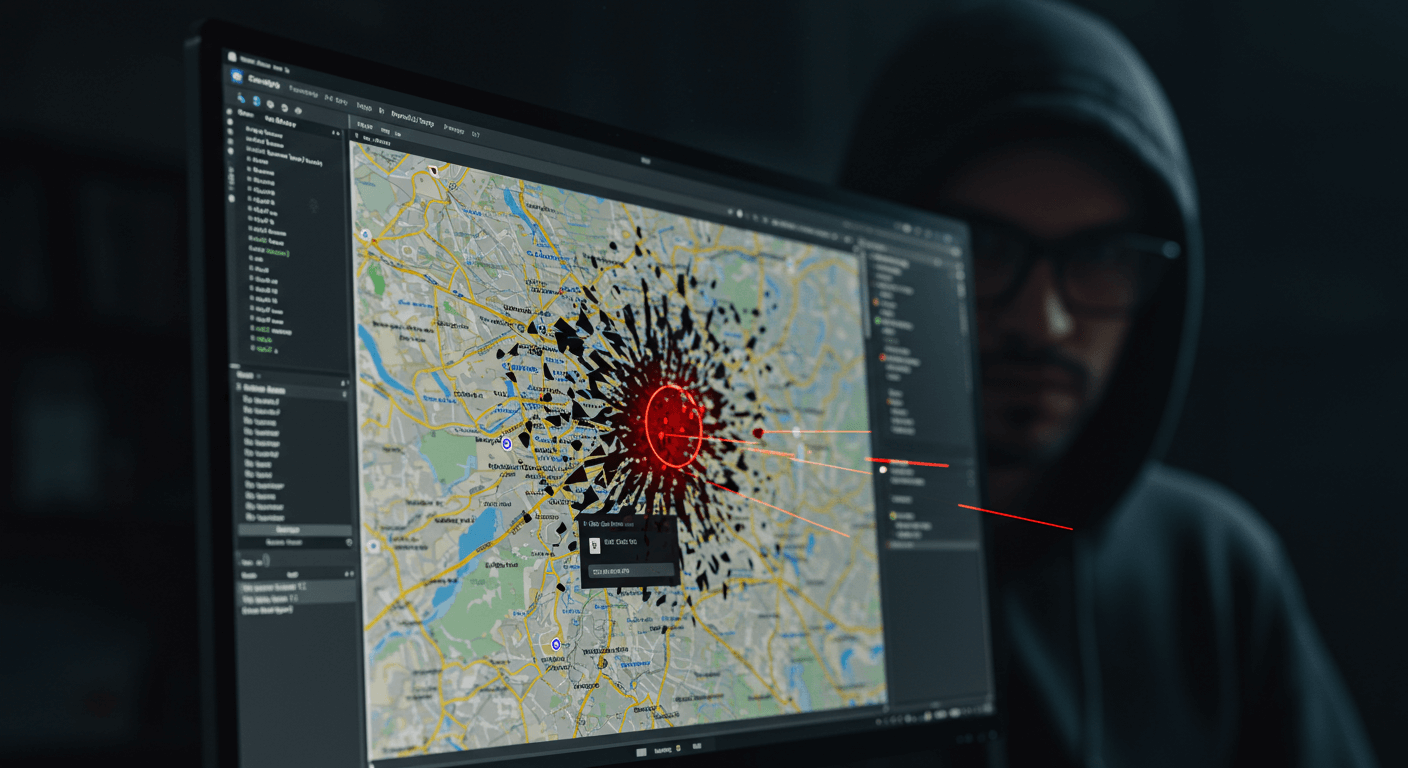
CityWorks CVE Breaches IIS
CityWorks breach leads to lateral traversal through IIS and onwards into your network. Protect it with Agilicus AnyX while you work on upgrading.
-

Come see us at the 2025 Texas Water Conference in the Innovation Lounge
Agilicus will once again be exhibiting at Texas Water 2025, taking place March 18-21 in Houston, Texas at the George R. Brown Convention Center. Texas Water is the joint annual […]
-

FTC To GoDaddy: Heal Thyself
FTC orders GoDaddy to improve security, marking an expansion in supply chain hardening tactics of government regulators.
-

Krooked Kriminals Krack Krispy Kreme
Krispy Kreme materially impacted by cyber security issue, files SEC-8K disclosure.
-

Advice Avalanche: Practical Steps for Wastewater Treatment Plants
Put the Avalanche of Advice Into Action: Wastewater plants face escalating cyber threats. Prioritise strong user identities with single sign-on and multi-factor authentication, abandon the outdated “air gap” concept, and embrace a practical zero-trust approach.
-

CityNews The Mike Farwell Show Interview
This morning I was interviewed on the Mike Farwell Show (CityNews). You can check the interview here @ 54:50.
-

SolarWinds Gives Federal Agencies Labour Day Present
SolarWinds Web Help Desk CVE-2024-28986 (rated 9.8 our of 10) is now included in CISA’s Known Exploited Vulnerabilities (KEV) Catalog, indicating its active use in cyber attacks, giving affected agencies until September 5, 2024 to fix the flaw under Binding Operational Directive 22-01. How fun.
-

Operate Your Plant Virtually with Agilicus AnyX
The demand for remote plant operation is increasing. It’s easier than ever to manage, monitor, and control plant operations remotely.
-
10 Billion Reasons Shared Passwords Are Bad: RockYou2024
Shared password bad. 10 billion passwords leaked. Your team installed some shadow IT remote access solution with a shared password.
-
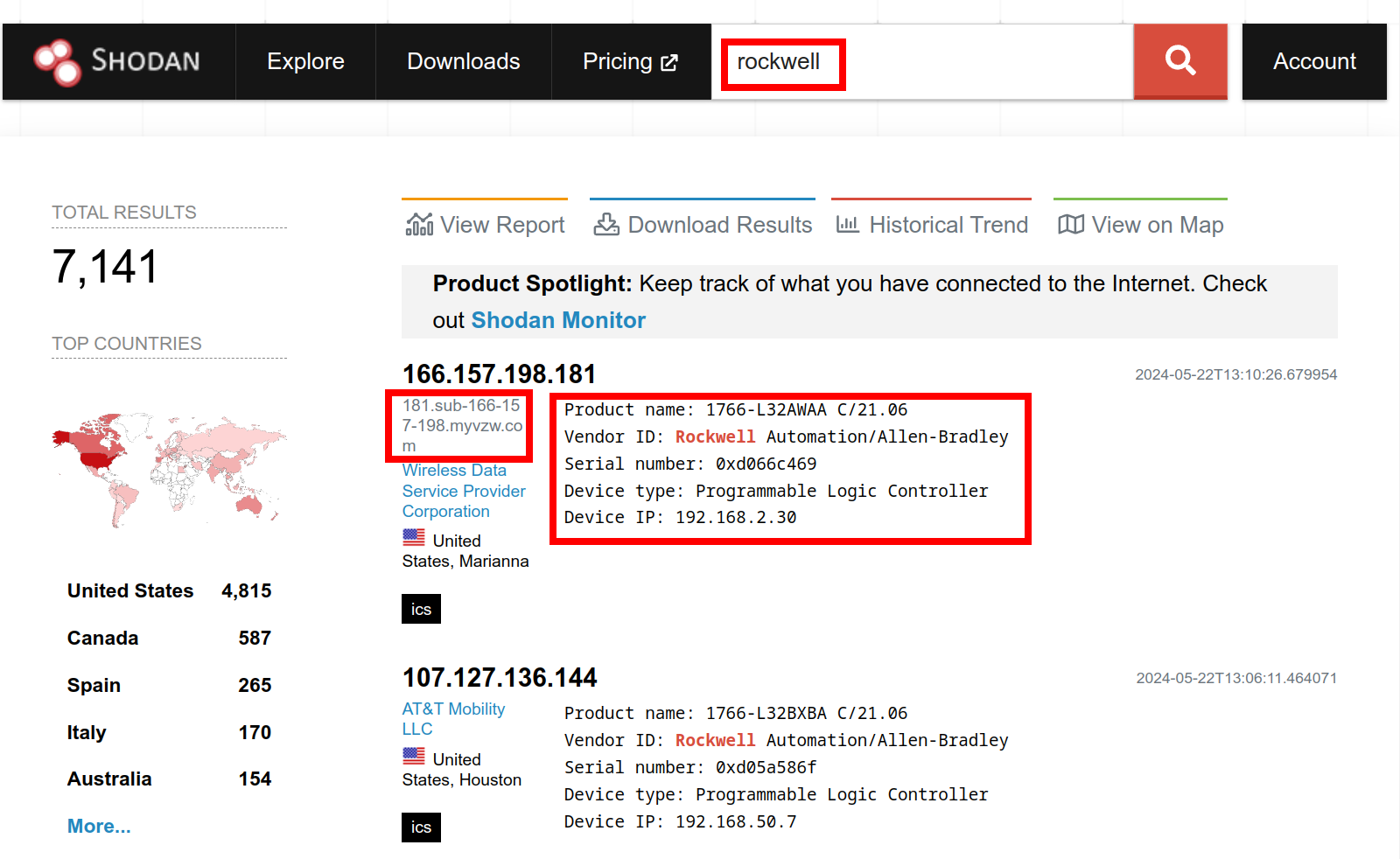
Get Thee From BGP Rockwell: Ethernet/IP Is not Internet
You wouldn’t download a PLC, would you? Rockwell Automation alert on public access to PLC, and a Shodan search to fact check it.
-

Fast, Simple, Secure: Implement CISA et al HMI (practically) recommends Agilicus AnyX
CISA, CSEC et al issue guidance on protecting VNC HMI in Operational Technology. Aligned with Agilicus AnyX.
-

Windows Update Breaks VPN, Good Riddance #zerotrust
Microsoft Windows Update Breaks VPN for Windows 10 and 11. 3rd party VPN’s have known exploited vulnerabilities. Let’s talk about VPN alternatives!
-

Industrial Supply Chain Matryoshka Risk
Last weeks hyper-critical NGFW vulnerability is this weeks embedded operational technology challenge due to nested risk and supply chain.
-
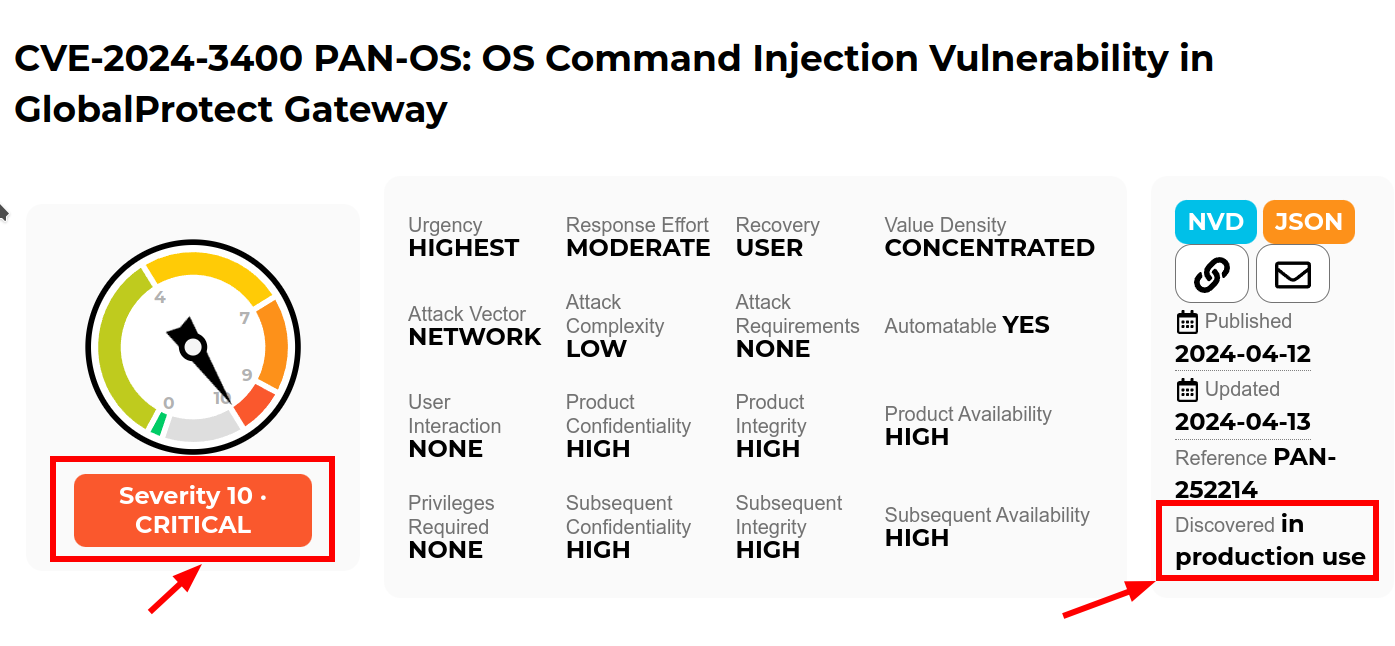
Quis custodiet ipsos custodes: When Good Firewalls Go Bad
Recently Palo Alto announced a 10.0 CVE in the Global Protect feature of their PAN-OS firewall. “Unauthenticated attacker [can] execute arbitrary code with root privileges on the firewall”. Well, that is not good. But, how “not good” is it? It’s terrifyingly bad ungood in fact.
-

CISA: 8 Top Cyber Actions for Securing Water Systems
CISA this week issued a Fact Sheet 8 Top Cyber Actions for Securing Water Systems giving a set of “do it now” practical actions for securing water and wastewater systems. Let’s talk about ‘Exposure’ to the Public-Facing Internet
-
Three Strategies To Help: Cisco ASA AnyConnect and WebVPN added to CISA Known Exploits
Cisco ASA AnyConnect and WebVPN added to CISA Known Exploits. Do you have one running on autopilot in your plant somewhere? Maybe between the IT and OT network? Maybe running the DMZ?
-

Multiple Connections Inbound Access Challenge
Multiple Internet connections can create inbound connectivity issues for remote industrial connectivity. The Multiple Connections Inbound Access Challenge.
-

Ground Hog Day: Fortinet VPN Edition
Another day, another VPN letting the world in to snoop around and fondle your crown jewels: Fortinet edition.
-

Dutch Defence Detail Dastardly Dirty Deed
The Netherlands ministry of defence just published the cliff-hanger document TLP:CLEAR MIVD AIVD Advisory COATHANGER regarding a remote access attack of their Fortinet FortiGate VPN by “a state-sponsored actor from the People’s Republic of China”. CVE-2022-42475 was the weakness. One thing that is unusual about the report is the direct attribution: this is rare.
-

Howto: Open Source Intelligence and your Digital Footprint
Let me show you a very simple means of Open Source Intelligence (OSINT) on yourself. If I can do this, anyone can do this, and if anyone can do this, someone bad can do this.
-

US sanctions Iranian officials for cyber-attacks on water plants
A group named Cyber Av3ngers affiliated with the IRGC targetting, modifying the HMI of publuc water systems. Today the individuals are sanctioned under anti-terrorism executive order.
-

VPNs in Industrial Environments: Old Yeller
VPNs in Industrial Environments: Old Yeller. It was a faithful friend for years, and now its time to shoot it before it bites you.
-

Begone Ivanti Industrial VPN Sayeth CISA
ED 24-01 directs agencies to instantly remove Ivanti Industrial VPN from industrial operations. Defence In Depth, Zero Trust give you more time to react.
-

Inbound HMI: Cyber Army of Russia Targeting US water facilities
Cyber Army of Russia Targeting US water facilities. Zero Trust Cybersecurity for VNC to prevent.
-

From Smoke Stacks to Smartscapes: Evolving Industrial Operations in the Digital Age
Smoke Stacks to Smartscapes. Past, Present, Future, the evolution in-place of the industrial control system, and the airgrap that once protected it.
-

Off-Grid Agricultural Cyber Physical Systems
The “John Deere Business Model” of taking something traditional and making it subscription. Starlink and its complex remote access needs due to CGNAT. And, cybersecurity, notably Cyber Physical Systems with their scary downsides of being able to move and cause damage.
-
Hard Industrial Cybersecurity is hardly secure, nuclear waste edition
One thing all industrial control installations have in common, they straddle the complexity of modern information technology with the dangers of operational technology and its inherent control of things which can go bump and boom. Hard Industrial Cybersecurity
-
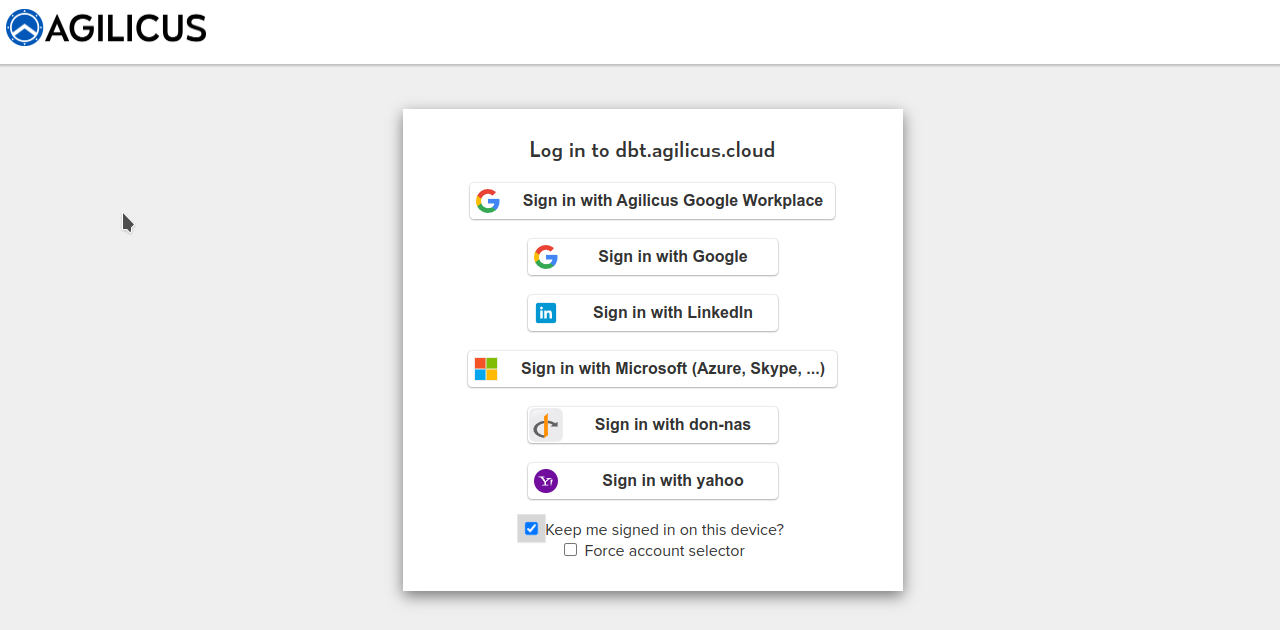
Your Logo: Theming Agilicus AnyX
Agilicus AnyX supports personalising the sign-in and usage environment to match your corporate brand. This is more than just asthethic: a consistent look and feel helps train users to reduce the likelihood of a successful spear-phishing attack.
-
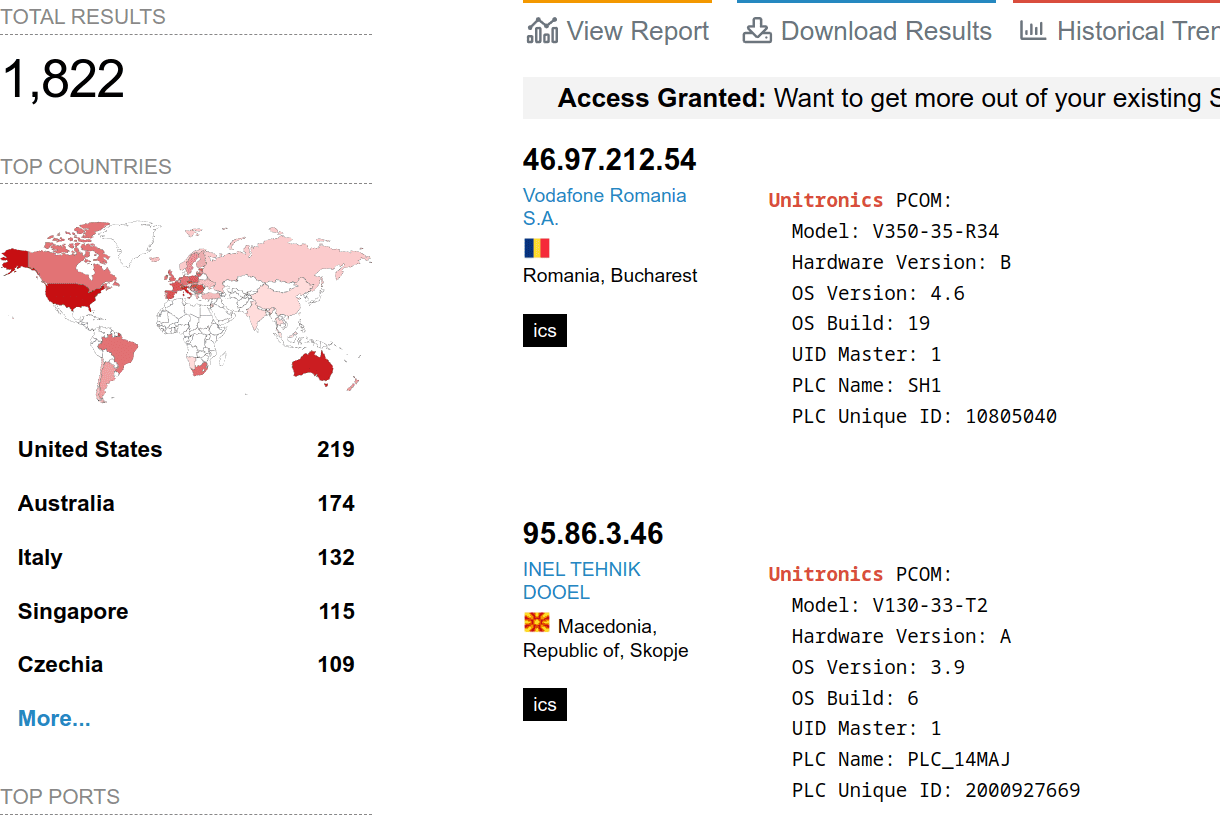
Avoid Exploitation of Unitronics PLCs used in Public Water Systems
Exploitation of Unitronics PLCs used in Public Water Systems for political purposes. Recommendations.
-

Attainable Municipal Zero Trust
Attainable Municipal Zero Trust: Key insights from recent Zero Trust implementations by Municipalities. Why, How, What ROI, Lead use cases.
-

Using Zero Trust to Enable Secure Remote Access to SCADA for Water Systems
This blog post explores the challenges of securing remote access to SCADA systems and how Zero Trust can act as a solution.
-

Zero Trust vs. VPN: A Comprehensive Comparison for Secure Remote Access
In this blog post, we’ll dive into the Zero Trust vs. VPN security model differences and why the former is ultimately the far superior choice for secure, seamless remote access.
-

SSH for Remote Access: Every User, Every Device, Every Application
In this blog post, we’ll delve into the challenges of enabling SSH for remote access and how you can do so without compromising security through Zero Trust.
-
Simplifying Secure Access: Enabling Rockwell Automation Remote PLC Access Without a VPN
In this post, we’ll explore the limitations of VPNs and delve into how to enable Rockwell Automation remote PLC access.
-
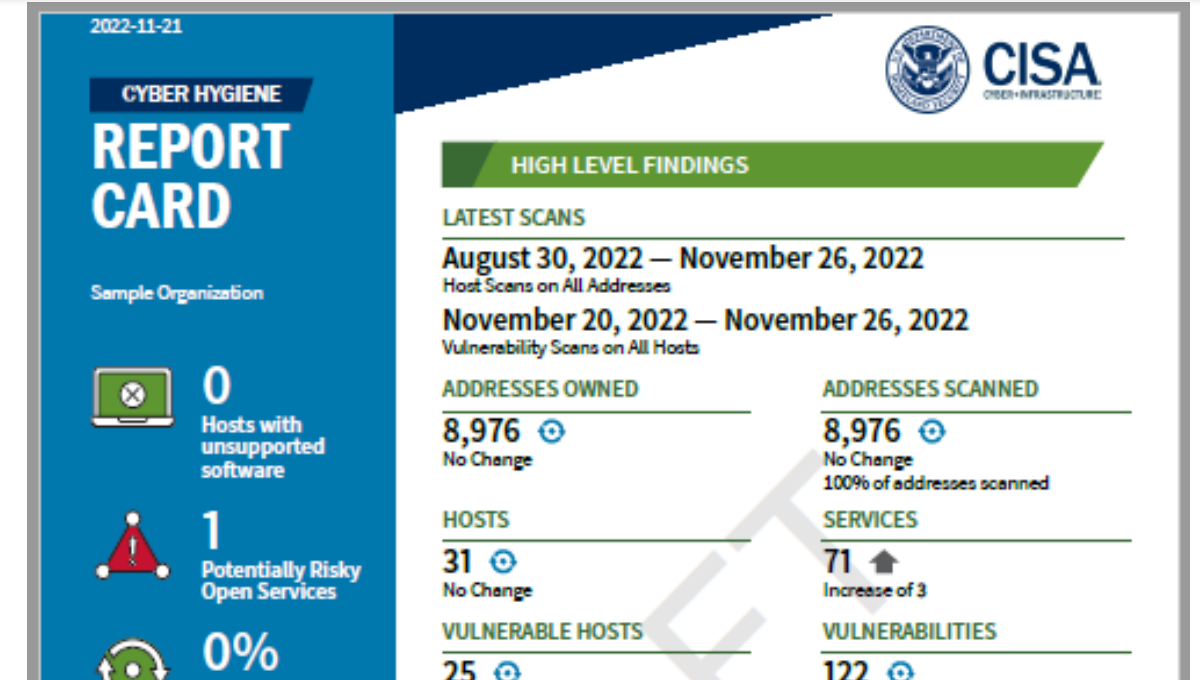
CISA Cyber Scan Water
CISA has announced a free (as in beer) service to scan water systems for vulnerabilities. Agilicus has used this scan for a year, receiving weekly reports.
-

Terminator Becomes National Standard
I’ll be back. Iconic line foreshadows rise of cyber-physical-systems. Terminator trifecta of physical machines, artificial intelligence, cyber-security awry.
-
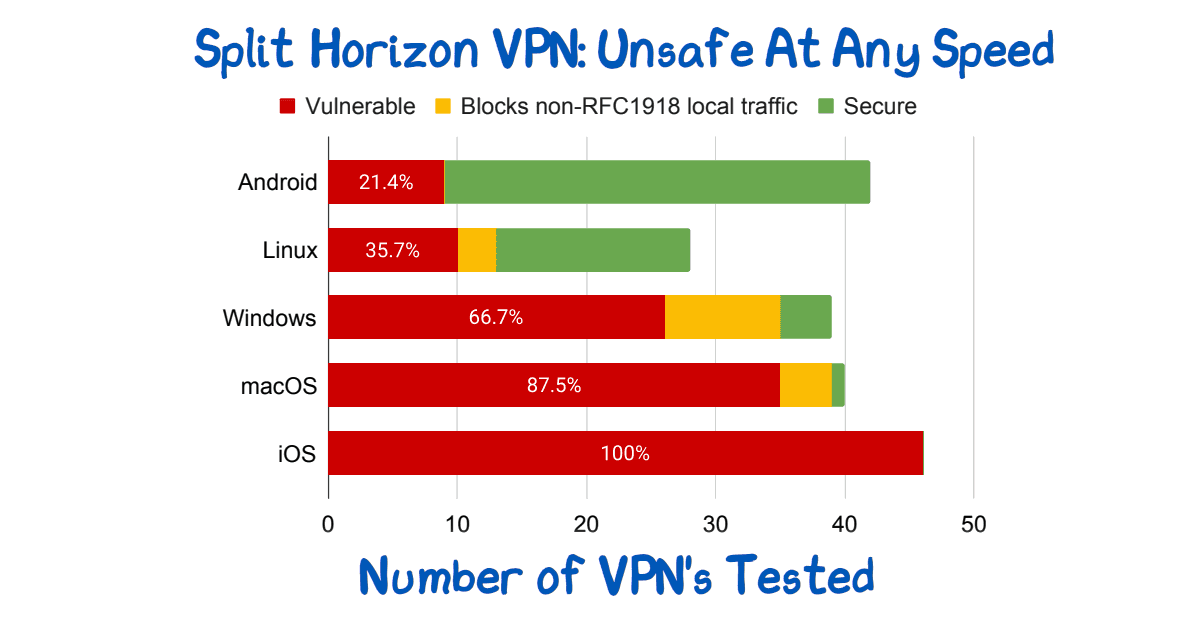
Split Horizon VPN: Unsafe At Any Speed
Split Horizon VPN’s are used to avoid breaking video conferencing. They are unsafe. See paper for route injection issues.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-
Bring Your Own Device in Agilicus AnyX
We’ll help you understand the benefits of BYOD and the robust, secure support Agilicus AnyX offers so you are equipped with everything you need to allow it.
-
Auto-Creating Users in Agilicus AnyX
Agilicus AnyX allows for auto-creating users that simplifies the process and enhances efficiency. We’ll help you understand the benefits & use cases.
-

Using Groups for Assigning Role-Based Permissions
We’ll help you understand the benefits of assigning role-based permissions using groups in Agilicus AnyX and the advantages of this approach.
-

Diagnosing User Issues with Audits
We’ll help you explore the importance of audits in diagnosing user issues and how using them in Agilicus AnyX empowers admins to resolve problems efficiently.
-
VNC and RDP in Agilicus AnyX: Which is Right for Me?
You have two different choices for how to enable a Desktop resource for your users: VNC and RDP. We’ll help you determine which one is right for you.
-

The Security Risks of Using VPNs in Water and Wastewater Facilities
What are the risks of using VPNs in water and wastewater facilities? We’ll help you answer that question and understand what to do instead.
-

The Security Risks of Using Shared Credentials in Water and Wastewater Facilities
There are many security risks of using shared credentials in water and wastewater facilities. Here’s why you should eliminate them and how to do it.
-
Best Practices for Connectors
You may have questions about how to install or configure Connectors in Agilicus AnyX. We’ll share best practices so you can decide what works best for you.
-
Best Practices for Multi-Factor Authentication
Multi-Factor Authentication is the strongest protection against the common cyber attacks. These best practices will help you implement it in Agilicus AnyX.
-

Give All Users a Unified Single Sign-On Experience
What do we mean when we talk about ‘all users’ or providing a unified experience? And what are the best practices around that? We’ll help you understand both.
-
Zero Trust Troika: The Who, The What, The How
Perimeter security approaches are no longer effective. A Zero Trust Network Architecture is a powerful, modern way to protect your network from cyber attacks.
-

Strengthen Your Industrial Network Cybersecurity with Vendor Access Management
Securing your third-party vendors can help reduce the cyber risk to your control systems and improve overall industrial network cybersecurity.
-
Agilicus Loves Let’s Encrypt™
Agilicus builds the best Zero Trust technology. It’s built on the best encryption, and the best certificate authority, Let’s Encrypt. Our business would not be possible without their good work.
-

EPA Cybersecurity Recommendations: Unpacking the Impact on Public Water Systems
This article will help you understand the new EPA cybersecurity recommendations, why they matter for public water systems, and the recommended solution.
-

Ready to Strengthen Canada’s Cybersecurity Ecosystem: Agilicus Qualifies to Sell Directly to the Government of Canada
Agilicus has successfully qualified to sell its innovative Zero Trust solution directly to the Government of Canada. This will help us bolster Canada’s cybersecurity ecosystem and help agencies defend against cyber attacks.
-

Understanding the CISA Zero Trust Maturity Model: A Framework to Improve Your Security Posture
This article will give you an overview of the CISA Zero Trust Maturity Model, the changes made in Version 2.0, and how it can benefit your organization.
-

The Zero Trust Roadmap: Understanding NIST 800-207 and How to Align With It
This article will give you an overview of NIST 800-207 and the different ways your organization can implement Zero Trust to meet the guidelines.
-
Best Practices In Vendor Privileged Access Management
Vendor privileged access management best practices: Access control, strong, unified authentication, fine-audit, secure access.
-

Identity Provider Versus Single-Sign-On
Single-Sign-On and Identity Providers are often treated as the same. But, the IdP facilitates the SSO. You can have multiple IdP if desired.
-

Who Are You? Prove It! Identity Versus Authentication
Identity vs Authentication. Who are you. Prove it. Related but different concepts. Ensure your IdP does not give identity when it realy means authentication.
-
GoDaddy Got Got: Multi-Year Breach
A multi-year attack involving 1.2M customers, hosting, DNS. What could the miscreants have achieved? DKIM? SSL? Domain verification?
-

Helping Organisations Qualify and Obtain Cyber Insurance – Ridge Canada Cyber Solutions and Agilicus Partner
“We are thrilled to partner with Ridge Canada to help SMBs who are scrambling to implement security controls, including multi-factor authentication and privileged access management for their cyber insurance”
-
Another Day, Another Exploit – Protecting Against the ProxyNotShell Exchange Server Zero-Day Vulnerability
Learn how zero trust protects against the new Microsoft Exchange Server zero-day exploit affecting Outlook Web Access (OWA), ProxyNotShell. With Agilicus, you’ll block lateral traversal and prevent unauthorised traffic from arriving at your resources while ensuring they are still accessible to legitimate users.
-

Well Timed or Coincidental, Cue the Phishing Attacks as 2.5M Students Affected by Data Breach
Days after announcing student loan forgiveness in the United States, 2.5 million student borrowers had their personal information exposed in a data breach and are at an increased risk of being targeted in a phishing attack.
-

Protecting Against the OWASP Top 10 Web Application Vulnerabilities
The OWASP Top 10 is a standard awareness document that outlines the most critical web application security risks and vulnerabilities. Learn how Agilicus AnyX is designed to eliminate an attacker’s visibility into the potential OWASP Top 10 web application vulnerabilities.
-
Agilicus and Operational Technology
Zero Trust Network Architecture can effectively meet the growing demand for enhanced cyber security in industrial and operational technology.
-

Industrial Air Gap – A Tale Of 2 Users
Industrial devices are hard to secure. Commonly done only via direct local access. Teams, however, wish remote access to improve efficiency. A solution to this battle is Zero Trust.
-
570 News Agilicus Interview
Interviewed on 570 News Tech Spotlight. listen to the interview here, I talk through some of the simple risks and how we help. And a bear joke.
-

Agilicus Awarded Government of Canada Contract
We are pleased to announce that Agilicus has been awarded a Government of Canada Contract with Shared Services Canada (SSC). The feedback and interaction we receive from such a marquis customer on our Any X Zero Trust platform is very valuable to us, and great validation of our ideas and technology.
-
Chewy Centre Protected By A Sponge
The M&M is not a good network design: chewy centre, hard shell. Recent cisco router vulnerabilities discussed for defense in depth.
-

Agilicus Recognised as a Top 100 Tech Company to Watch in 2022
We are incredibly excited to announce that Agilicus has been included in the FoundersBeta Top 100 Tech Companies to Follow in 2022. Every year FoundersBeta compiles their list of the […]
-

Top 5 Cybersecurity Resolutions to Cross off Your List in 2022
Cybercriminals had a record year, the cost of a breach reached new highs in 2021. With clear cybersecurity goals, businesses avoid becoming a news headline.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-
NIST sp 800-63B: How Well Do I Know You?
Zero-Trust Network Architecture has 3 steps: Authenticate (Who), Authorise(What), Access(How). 3 Levels of strength of the who are defined in NIST sp 800-63B. Does the goldilocks principle apply to you? Read on!
-

Log4Shell – Not Even the Smart Thermostat is Safe
Ignoring systems that may be deemed ‘unimportant’ in comparison to your revenue-generating technology stack will leave your organization open to compromise from the Log4Shell vulnerability.
-

A Little Consequences Go A Long Way: Return Of The Bear Joke
Two hikers see a bear. One bends over to tie shoes. Other says, you can’t out run a bear. First says, just need to outrun you. Pause laughter
-

Fake It Till You Make It: Canadian Bank Multi-Factor Authentication Edition
A big 5 Canadian bank has a fake multi-factor authentication sytem, allowing anyone to fall back to password. Why? How is this acceptable?
-
The Economic Cost Of Not Having Multi-Factor: MSP Lawsuit Edition
Managed Service Provider Breached. Customer pays out. Who is at fault? Lawsuit to determine. Multi-factor authentication to prevent.
-

Agilicus In The News: Kitchener cybersecurity firm makes remote work access simple, secure
The Record published an article today on Agilicus. It covers the back-story on what we have set out to accomplish
-
Tech Spotlight: An Impromptu Interview
Interview w/ CityNews 570. Hear the origin story of Usenet in my life, and the plan to buy Doritos. And don’t call me old, I’m experienced!
-

Cyber-Security For Thee But Not For Me
How some public sector entities have great cyber-awareness training, but exempt the elected and senior staff. From Great To Good in one step.
-

Minimum Viable Secure Product
A simple set of controls for a Minimum Viable Secure Product. Open source for us all to use. Implement, ask in RFP, common baseline to follow
-

Telnet In Canada: Why?
Telnet. 40 years old, not fit for purpose. Alive and well in Canada. No amount of mitigation or multi-factor authentication makes it OK.
-

Multi-Factor Authentication And The Supply Chain
A high(ish) profile nodejs library is compromised. No multi-factor authentication used by developer. The ripples are far and wide. Including you!
-
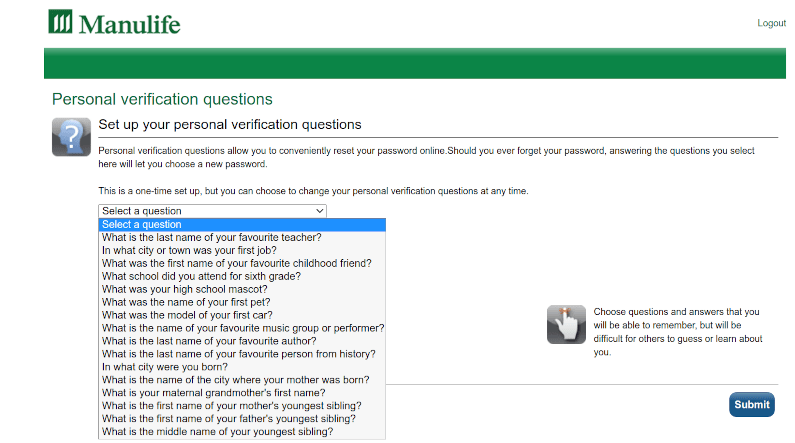
The Personal Verification Question: Password’s Dumb Cousin
The personal verification question. The dumb, slow cousin of the password. Stored in plaintext, findable in social media. Not multi-factor auth
-
Syniverse Hack, Multi-Factor Authentication, Who Cares? You Should!
This article discusses SMS as a second factor for multi-factor authentication in context with the Syniverse hack.
-

I AM. I HAVE. I KNOW. Multi-Factor Authentication
I AM. I HAVE. I KNOW. The trifecta of simple and secure. Why does it improve security so much? Because the factors are not correlated. Use at least 2.
-

Agilicus Named CIX Top 20 ‘Canada’s Most Innovative Companies’
Agilicus, a leader in Zero Trust Network Access, solutions is named one of Canada’s most innovative technology companies by CIX Top 20 Early annual award.
-
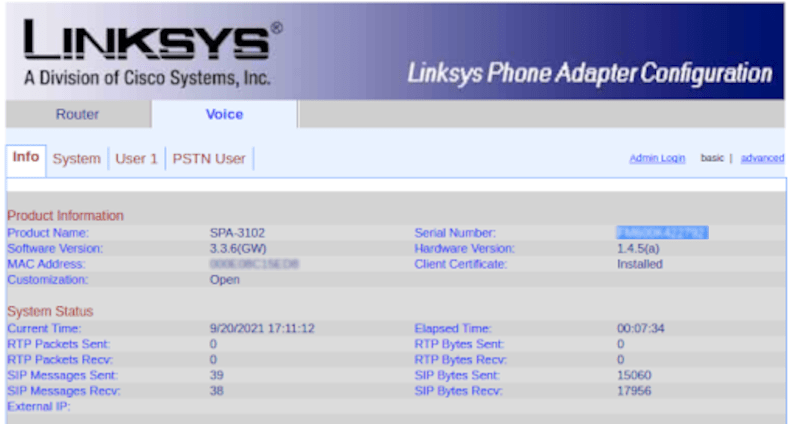
Zero-Trust Remote Access to Fix VoIP DDoS
Reconfigure a VoIP PSTN gateway remotely via Zero Trust with Multi-Factor Authentication and single-sign-on to avoid a DDoS.
-
Add multi-factor authentication to old applications
Your cyber insurance is up for review. IGet all applications authenticated with multi-factor, simply, quickly, compliantly.
-

Authentication, Authorisation, and API Keys
e encouraged to create API keys by many SaaS tools, and, these present real authorisation challenges.
-
Mind the gap between the web app and the desktop
We want a web app. We have a desktop. Use zero-trust to make any desktop available to any device without a VPN.
-

A ’round tuit’ to get your internal web apps available
You have an internal tool. Grafana, Prometheus, …. You get an alert, its via Slack, Chat, etc. You click. The link goes nowhere. You curse. We fix!
-
The Pipeline Ransomware Came Via The VPN
A criminal group takes over a nations energy via a VPN. Its time to treat the VPN as a risk, not a security solution. Zero Trust is better.
-
SSH To Server. No IP? No Problem!
SSH to the server fleet. No Public IP? No problem. No VPN. No firewall changes. End-to-end encryption. Any user.
-

Keep The Share, Ditch The Ransomware With Zero Trust
Keep The Share. Ditch The Ransomware. Simple Zero-Trust allows any user, any device, any share, no VPN, no ransomware. Simple single sign-on.
-

Zero Day Zero Trust Is Your Defense in Depth
Zero Trust. The principle of limiting access to user resource pairs. It is part of a good defense in depth strategy. It is also a key defense to Zero Day.
-

3 Simple Steps To Reduce Ransomware Risk
These three simple steps will dramatically reduce your ransomware risk. Achievable, understandable, reasonable.
-

SCADA, Zero-Trust, Content-Security-Policy
A Florida water treatment plant breached. People nearly poisoned. SCADA exposed via Windows & TeamViewer. How did it happen, how do we prevent systematically?
-
Re-Using your Multi-Factor Authentication To Prove Humanity
Spam. The cat and mouse game of advertisers seeking to reach more people for less cost, and, people seeking to spend more to not be reached. The current state of the art in proving “I am not a spam-sending robot” is the captcha. Do you love the captcha? Me neither. Do you sometimes fail it? Me too!
-

Quis, quid, cur, quomodo, ubi, quando, quibus auxiliis
Grade 10 English, the W5 (Who, What, Why, When, Where, How). A common framework to frame something. Apply it to the problem domain of Zero Trust Networking.
-
Security Report Chain: The vulnerability reports we receive
Security.txt and policy are enabling inbound reports, but the reports are not all equal quality. Should I pay for incorrect ones?
-

The strong password, the breach, and the multi-factor save
A strong password breached. Multi-factor authentication saved the day. So many passwords to check. Why can each site not use OpenID Connect single identity?
-
Identity Sprawl And Shadow IT
Empowered people make pragmatic decisions to improve productivity. This can create Shadow IT, and, Identity sprawl. Fix via Identity Aware WAF
-

Better Than Nothing Bonding With Remote Access: Starlink + 2xDSL Backup
Deploy OpenWRT on a Mikrotik to achieve SpaceX Starlink + bonded DSL backup, with Zero-Trust Network Access inbound from any user, any network, any device.
-

Core Web Vitals WordPress Improve Recaptcha Performance
Core Web Vitals Wordpress performance is important for user experience, for search optimisation. Learn how to improve wordpress and recaptcha CWV.
-

Speedup WordPress By Dequeue Unused Scripts
Speedup wordpress by dequeing unused scripts and css. The Events Calendar is used as an example. Faster load, less parse, better core web vitals.
-
Quis custodiet ipsos custodes: The Email Scanner Was The Threat
An email security threat scanner, looking for phishiing links, itself becomes the attack vector, from within. Unsubscribed from pardot the beginning.
-
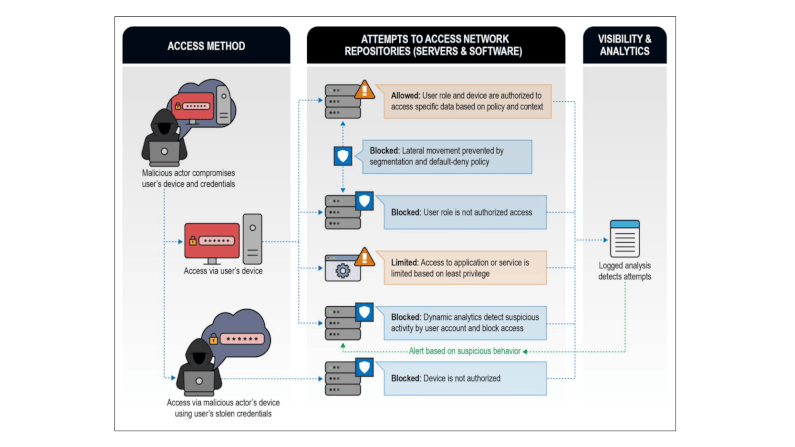
Embracing Zero Trust Security Model: NSA Guidance
Embracing Zero Trust: Assume that a breach has (or will occur), use defense in depth, fine grained authorisation and audit, everywhere, always.
-
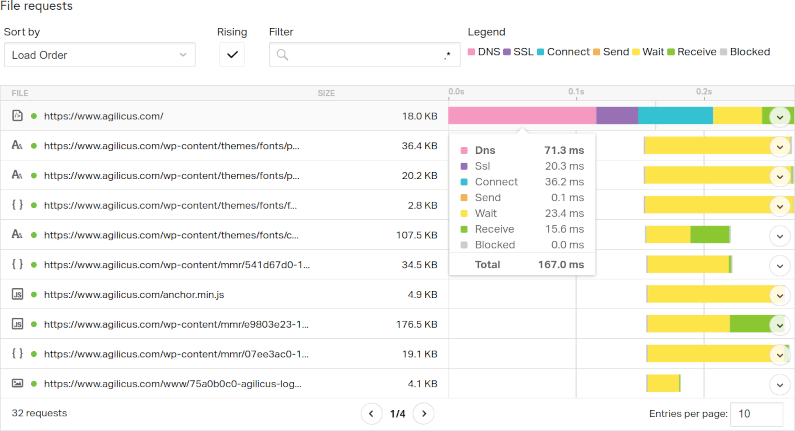
Its Always DNS: Latency In Web Load Time
Latency, specifically DNS Latency, is a big factor in web page load time. Don’t over-focus on bandwidth, examine prefetch and latency to improve.
-
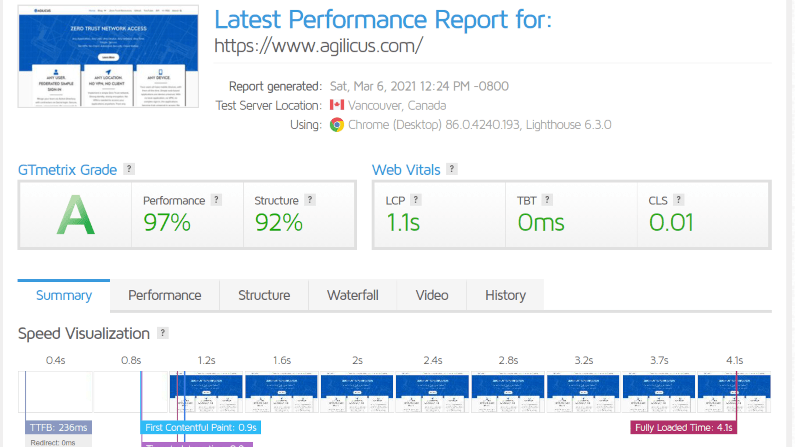
The Quest For Web Site Performance Perfection
Web site performance. Search engines favour sped. Milliseconds matter. Performance is as important as the content, as important as the appearance.
-
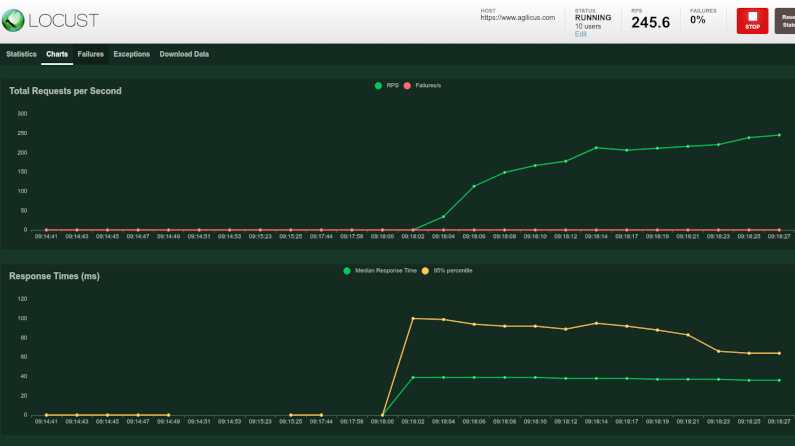
Latency And Load Testing Your Web Site With Locust and Istio
Your web site uses new technology. Shake it down by using your Sitemap for Latency and load testing with locust and istio.
-
Remote QuickBooks Share Access Without The VPN
Access your QuickBooks from anywhere, as any user, without a VPN. Live. No export. No ransomware.
-
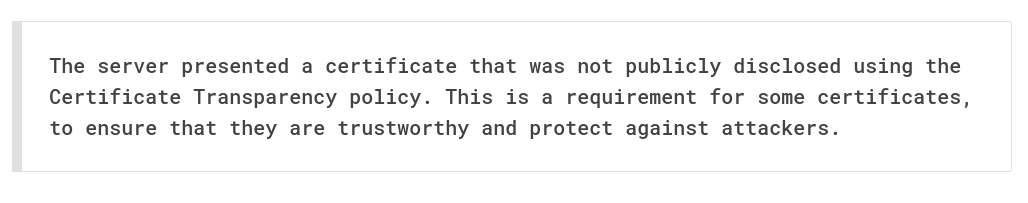
Time and Encryption are Inter-related: Certificate Transparency
Time and Encryption. Certificates have a not-before and not-after. If your time is wrong, you can be tricked. Learn how the certificate transparency helps you.
-
Zero Trust Secure SCADA Could Make Your Water Safe To Drink
A water treatment plant was breached, looking to poison people. How did the hacker get in, and how would zero-trust secure scada?
-
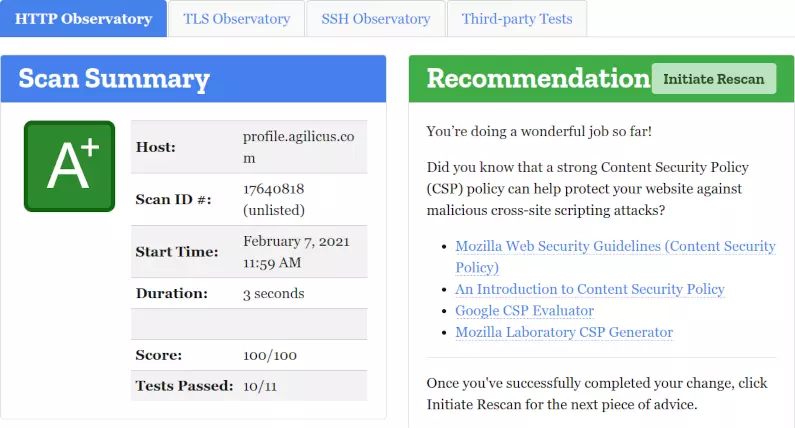
Angular Content-Security-Policy Complex Nonce: Google Tag Manager
Content-Security-Policy protects our application, but challenging with external scripts like Google Tag Manager. We show in Angular Single Page Application.
-
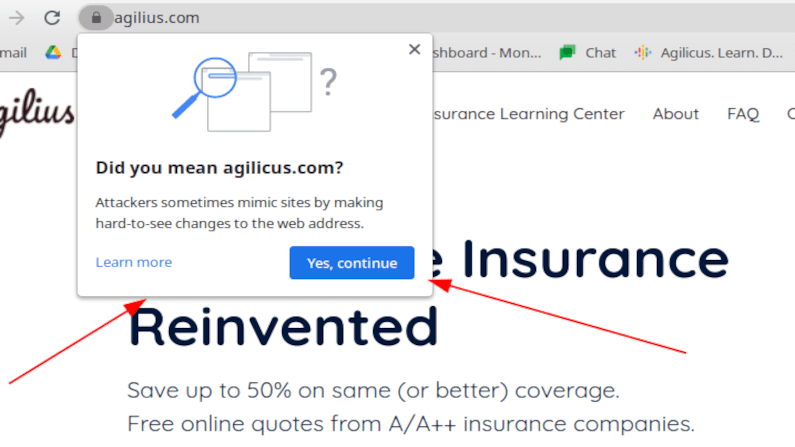
Doppelganger Domain Detection
Doppelganger domains are used to spear-phish you. They look similar to ones you use normally. See this new warning in Chrome.
-

OAuth 2.0 Security Best Current Practice
OAuth 2.0 is deceptively simple: create client id, client secret, set a few environment variables, and watch the black magic take effect. Learn about the best current security practices.
-

Securely Updating Software: The Update Framework
Secure automatic software delivery without the risk of tampering. The Update Framework in action.
-

Embrace Failures: find the start times of Kubernetes pods
Cloud Native: embracing failures. Assume Strength in Numbers. Don’t spend large time on a single infinitely reliable thing, assume each component will fail.
-
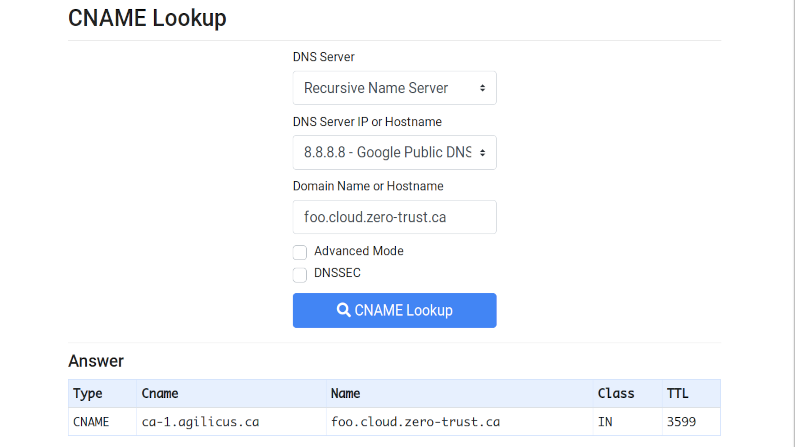
Internet Redirect & Alias: The CNAME
CNAME. Invented in 1987, used in today’s SaaS. See how your domain can be shared with your partners.
-
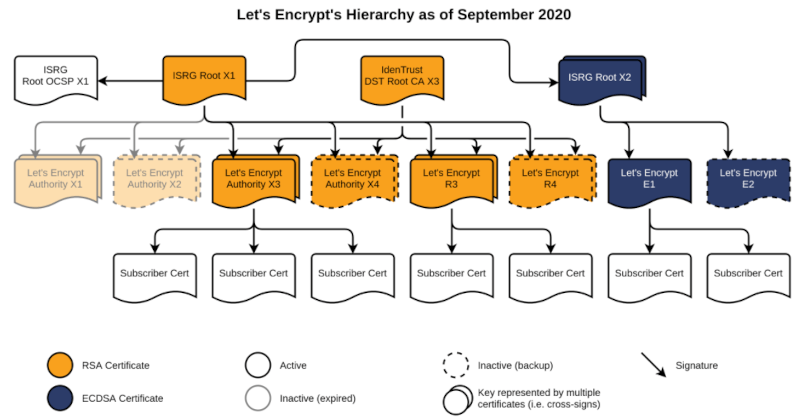
Let’s Encrypt X3 to R3 and Certificate Transparency Logs
Certificate Transparency Logs in SSL can be a useful diagnostic tool as well as a security forensic.
-
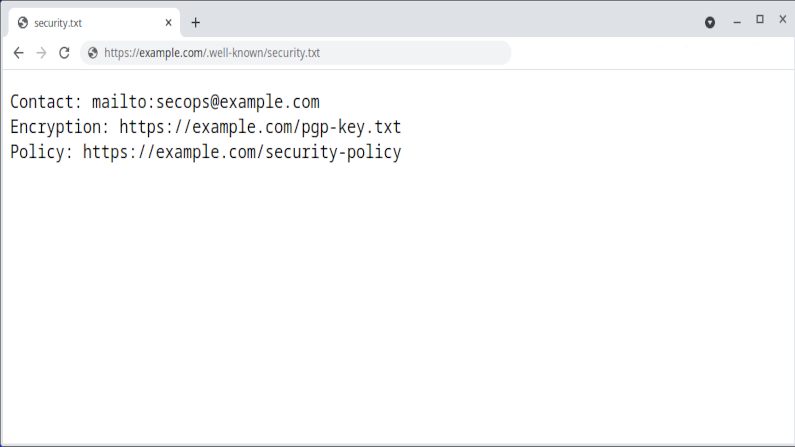
Security.txt: how to document receiving security vulnerabilities
Document how you receive and treat security vulnerability reports with the security.txt standard
-

OAuth 2.0 Protected Resource Threats
The OAuth 2.0 protected resource. It takes the access token and uses it to grant access. Watch out for it becoming compromised.
-

OAuth 2.0 Refresh Token Threats
OAuth 2.0 refresh tokens are used to obtain new access tokens on the user’s behalf. If lost, they can allow an attacker to masquerade.
-

OAuth 2.0 Token Endpoint Threats
The OAuth 2.0 Token Endpoint. Its were authorisation becomes real. Secure it to prevent guessing
-

Your password policy is wrong: NIST SP 800-63B
Your password policy is wrong. So says this NIST standard. By trying to be too strong, you end up being weak. The users write it down!
-

OAuth 2.0 Authorisation Endpoint Threats
OAuth 2.0 Authorisation Endpoints are the front-door skeleton-key creator of all your front-doors. So protect them carefully.
-

OAuth 2.0 Client Threats
OAuth 2.0 and the client. Use Defense In Depth. Secure the client, and then assume it can still be compromised. Zero Trust.
-
Fail to ban. Simple. Strong. Defense in Depth
Fail to ban. Simple. Strong. Make the attackers wait, increase their cost while decreasing your cost of defending. Defense in Depth.
-

OAuth 2.0 Threat Model and Security Considerations
OAuth 2.0 has simplified authentication and authorisation for many applications, shifting from custom code to simple library import. However, as more applications come to rely on it, this makes its weaknesses more interesting. An attacker can gain access to a broader set of data via a smaller set of tactics and techniques. First lets understand the threat areas, and then, the best current practices for addressing them.
-
Merger, Acquisition: Federated Identity And Zero Trust
Merger Acquisition Zero Trust. Two competitive or orthogonal companies become one. Achieve quick and secure with Federated Identity, Zero Trust.
-

Joint Venture: The Case For Federated Identity And Zero Trust
Joint Ventures: Good Business strategy, complex access strategy. Does one VPN to the other? Dual accounts? Zero Trust Federated Identity FTW!
-

OAuth 2.0 Proof of Possession
OAuth 2.0 replaced Proof of Possession with Bearer Tokens for simplicity, a controlversial decision. A new draft brings them back.
-

OAuth 2.0 Access Token Demonstrate Proof of Possession
Theft of an Access Token need not be a complete loss. Learn how Demonstration of Proof Of Possession can reduce this risk.
-

Zero-Trust Reduces Ransomware Risk
Target ransomware with Zero Trust. Defense in Depth with better audit, reduced access, increased simplicity.
-
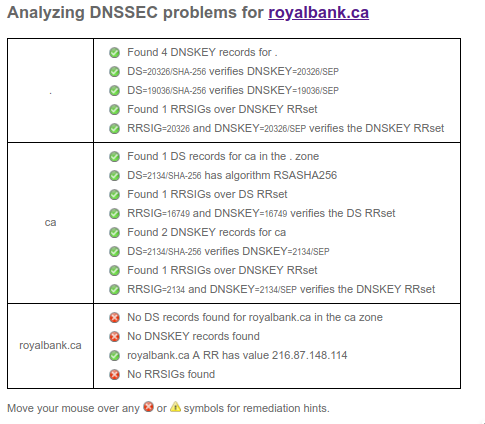
Button down your 2-factor-auth and dnssec lest ye be hijacked
DNSSEC. It helps prevent someone from poisoning a DNS cache or creating a lying recursive. Its simple to enable.
-
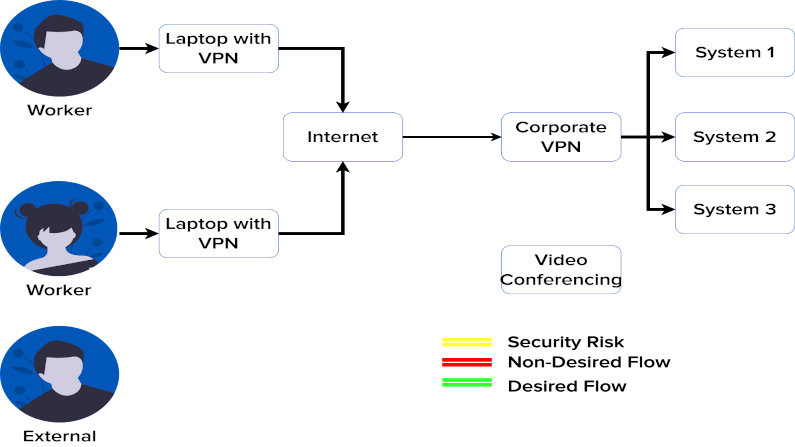
Your VPN Hates Your Video Conferencing. Here’s Why
Got VPN? Got perfect video conferencing with everyone all the time? If yes, well, this video is not for you. For the rest, read and view!
-

Blurring the web and the app: web push
Web push. An important part of making web applications peer to native, and more secure, more accessible.
-

Zero Trust Audit Logging: Reliable Meets Simple
Big investments in SIEM become big headaches due to correlating IP and NAT. Skip that with crypto-secure audit with Zero Trust via JWT.
-

Reject The Status Quo: Zero Trust Status Future
The myth of the VPN, the Firewall as the only and best method of remote access has lived for 20 years. Let’s retire it together. I discuss the myth, and, an outbound-only, no firewall reconfiguration method, no client method of achieving your goals of happier productive users accessing their data and applications.
-
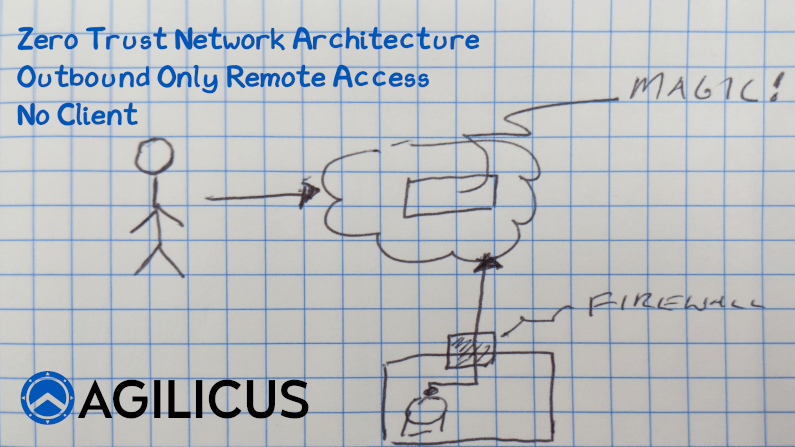
Access an Internal Resource with no Inbound Connections
Learn how to implement Zero Trust Network Access with no inbound connections, no firewall changes.
-
The Agilicus Philosophy: Continuous Learn. Do. Teach.
The Agilicus Philosophy: The world we work in changes. Our requirements change. By continuously learning and adapting, we survive and thrive.
-
My team works outside, why can’t their Kronos Timesheet?
Access your on-premise Kronos from any user, from any device, from any network. Increased security, increased simplicity. Zero Trust Networking.
-
Stupid Simple Security Trick: Add a DNS CAA Record
Want to improve your security for zero cost before you leave for the day? Add a DNS CAA Record. Watch the video to learn more!
-

You want me to sign in with what now?
“Sign in with…”. What does it mean? Why should I use it? What am I giving up? There must be a catch, right?
-

The Firewall Emperor Has No Clothes
The Firewall Emperor, long the king of security, has no clothes. Micro segmentation is just more firewalls. You want Zero Trust Network Access.
-

The JWT Bearer Token: You On The Wire
A bearer token is a cryptographic representation of who (you) and what (authorisation) that is used on a per-transaction basis. Learn and Use!
-

Dockerhub and pull limits: cache some insurance
Concerned about the new dockerhub rate limits? Run Kubernetes? Run CI? Deploy a pull-through cache simply to reduce the risk and impact.
-

Software Supply Chain Redux: npmjs shells your hosts
The software supply chain might be the biggest cyber threat out there. Easily accessible open-source, developers under pressure to deliver, complex dependencies. Trouble ensues in npm ecosystem.
-

Identity, Authorisation, Access: Microsoft Dynamics
Single Sign On with Microsoft Dynamics. First decide what this means, to who it means what. Then find a way to federate their natural, native identity providers together.
-

Take time to stop and sniff the mime type
Happy Eyeballs? Mime-Type-Sniffing? Security wins, don’t infer content type from file name.
-
The deep rabbit hole of email in cloud
Email. Port 25. Security. Spam. Its more complex than it used to be to be a good Internet citizen for email sending. Cloud edition.
-

Delicious Dogfood: Cloud Native WordPress
Take Wordpress. Modernise it. Make it cloud-native. Add tidb cloud-native database. Add stateless storage.
-

Simplify Security: Split Identity and Authorisation with Zero Trust
Zero Trust. The key principle is, we split identity and authorisation apart. We move from a perimeter-based trust (e.g. VPN + firewall) to a user + asset-based model.
-

Web Application Security 101: Get the basics right
Do what I say. The central tennet of security. In web application security, this translates to a set of headers. Learn how to use Content Security Policy, XSS, CORS, etc.
-

Don’t let the browser pass you by: keep your server up to date
Browsers update faster than servers, being consumer technology. TLS 1.0 and 1.1 are dead, update your servers.
-

WEB SECURITY 101
January 2020 Waterloo Technology Chautauqua, Web Security 101
-

USE OF POSTMAN WITH OPENID CONNECT PKCE AND API
Many API’s, Agilicus’ included, use OpenAPI to specify how they function. Authentication of these is usually left out of scope, but, provided as a bearer token. This means that if you write a web application, you want to directly use the RESTful API’s, and you do so by first authenticating via OpenID Connect PKCE flow and remembering the access token.
-
Zero Trust: Connecting The Digitally Disconnected
Digitally Disconnected. The 2nd class citizens of the 21st Century. Unable to access data due to identity or VPN. NO MORE! Zero Trust.
-

Ding Dong: The VPN is dead. Split Identity and Authorisation to Simplify Security
A philosophy that allows you to reduce cost, increase security, and increase user engagement and satisfaction. All 3 at once. Sounds crazy?
-

Finding your Google ID and reclaiming your Gitlab account
OpenID Connect, a powerful single-sign-on with strong security, and locking the user to the upstream ID means if their name changes you are insulated.
-

Email Strict Transport Security: Our First Report
Email Strict-Transport-Security. Complex to setup, but provides encryption on the transportation of your email like HTTP Strict Transport.
-

Zero Trust Architecture: Published by NIST
Zero-Trust. Make your team more efficient, increase your security, reduce your cost? What’s not to love. The line for the bandwagon starts over there.
-

Brand Indicator Achievement unlocked: BIMI and you
BIMI is a new standard for logo protecting your brand email from identity theft. Implement with DNS and DMARC today.
-

Static Application Scanning Angular: Resolving lodash npm audit
Static Application Scanning with Angular can sometimes block release with no solution. Learn about better-npm-audit.
-
Trust You? I Just Met You! How Trust-On-First-Use Can Increase Your Security
Trust-On-First-Use for enrolling multi-factor authentication.can improve your security for lower cost. Sounds like a win to me!
-

Cross-Origin-Request-Sharing and You
CORS. The method by which we secure web applications that are de-monolithed to directly use API’s
-

CORS’ing the complexity: idempotent and caching meets Vary: Origin for CORS
Cross-Origin-Request-Sharing (CORS) is challenging to implement. Learn how to make it work with multiple applications in the same browser.
-
The False Choice of Risk Versus Reach
Risk versus Reach. A false choice. We should not materially compromise security to reach more users.
-

Secure the Cookie!
The humble cookie. So controversial. So complex to secure. If your web app must have them, you must secure them.
-

The browser was the accomplice
You and your browser run inside a nice safe firewall. A firewall which doesn’t do what you think. Explore how the browser is the accomplice to the crime.
-

Zero Trust and the NTT Hack
NTT Comm discloses a breach. Firewalls lead to false assurances, allowing wide open internal access.
-

Fixing the case of the Implicit Flow modification
Meet Hank. Hank is a web application with a dark secret. It trusts you the user to not change things in the browser. Bad Hank. Learn how to fix it!
-

Why should I use Content-Security-Policy?
The Content-Security-Policy headers exists to protect the users of your web site from the content they themselves might create.
-

The Web Application Firewall and You: Who Should Use, and When.
Should I use a Web Application Firewall? What is it ? What benefit will it give me? When would I use it? Read on to learn!
-

Fixing the case of the un-sanitised input web app
Web applications may not be inherently secure. But we want them Internet available anyway. How can we reconcile these two? Let’s see!.
-

Agilicus Story: Cloud Native Computing Foundation Stories
Agilicus presents its architecture, philosophy, strategy at CNCF Eastern Canada Stories Meetup
-

DEFENSE IN DEPTH: CLOUD NATIVE DAY 2019 TALK
We often think in Boolean terms: Outside Bad, Inside Good Instead, assume each layer will be breached
-

How phishing negates your firewall
Your corporate firewall. That invulnerable bastion that lets you fearlessly run less-than-secure internal tools like a CRM, a Finance portal. But, is it really invulnerable? Or is it a paper wall at best? We look at how Cross-Site-Scripting vulnerabilities, known session ID cookies or access tokens can allow content from the world to pierce it as if it were not there. We do this using the weakest link: you.
-

Logging real remote address with Nginx and Lua
For audit, security, tracing, we want the origin IP logged. Load-balancers can mask this. Learn how to log the true client IP from nginx with lua, when that nginx is behind a load-balancer (reverse proxy)
-

Why your VPN is slow: the case of the work-at-home streaming
VPN slow? It might be your friends using YouTube and Spotify. Ration bandwidth? Split Horizon? We recommend door #3: Zero Trust, Internet Exposed, Direct.
-

Zero-Trust Makes Working From Home Secure And Reliable, Unlike VPN
A sudden influx of remote workers is stressing the VPN. That stateful device struggles. Consider a future switch to Zero-Trust, secure remote access with it.
-

Using Istio & OpenID Connect / OAUTH2 To Authorise
Make it simple and safe to be secure for your developers. Allow any internal devops site to have single-sign-on and authorisation.
-

The desktop crypto curveball: test your encryption
Encryption. Its good, if its working,. You should test your encryption, on the desktop, on the server, once in a while. Curveball recently came out, test it!.
-

Don’t trust the firewall: why defence in depth is important
A firewall is not an absolute defense. Weak things inside it can be attacked through JavaScript or other vectors. Defense in Depth is important.
-

Mutual Identity: Phone Scams And Workload Security
Establishing mutual identity trust is complex. I must know who you are, you must know who I am. People fall for phone scams with caller ID. Let’s fix for online.
-

I Fixed My Malware Injection Issue With Content-Security-Protection
My personal site had a permissive content-security-policy. This allowed malicious adware injectors to grafitti it up. I fixed mine, fix yours today.
-

Securing a web (site/app/api)
Ever wondered how to check how secure a site is (yours, another?). In this presentation I show how to do a simple assessment of security.
-

Assess Web Security Simply. You. Yes You.
Asssessing web security, The basics are faster and easier than you think. A few simple free tools, a minute or so of our time. Let’s try some sites now.
-
The Philosophy Behind The Name
Agilicus. Its a compass on a shield, reminding us of the need to protect from the east-west traffic. But what about the name? The icus part invokes Spartacus (from which […]
-

Zero-Trust Principles
The principles of zero trust make for improved security. Each component must prove itself to its neighbours. No trust is based on affinity or path. Explore.
-

Secure Exposed Access: Zero-Trust Legacy Online With High Security and No Work
Somewhere in your basement lurks a challenge. A web application that people need, but you don’t trust. Maybe its your timesheet or vacation planner. Maybe its your HR policies portal. […]
-
Free Your Applications: Ditch the IIS, Move Your .NET Apps To the Cloud. Safely. Securely. Simply
Your basement is full of servers running Microsoft IIS with .NET applications, chatting with local databases. You’ve read casually online about Cloud Native, Kubernetes, Containers, Docker. But this doesn’t apply […]
-
Strong Identity and Authentication: Avoid Named User License Costs With Federation
Implement a srong, simple, secure authentication system, including support for 2-factor authentication, without triggering named-user license costs.
-

Tame the legacy beast with API’s
Large legacy systems hold our data hostage. Tame their grip with REST-ful API’s and microservices. Fear no more on upgrades or even replacements.
-

Two-Factor Herd Immunity: Mozilla 2-factor authentication
Mozilla makes multi-factor authentication mandatory for authors. Herd Immunity suggests if we get a few more, we are all protected.
-

Remove information exposure: nginx banner
Information exposure. Many servers send a helpful banner out with the specific name and version of the software. This can in turn attract low-level attacks that use tools like Shodan.io […]
-

Auth and API: OpenID Connect for user + service, and enforcement along route
Identity: Authentication a user in a simple, secure way, with two-factor authentication, and allowing the user to interact with API are the key to success.
-

Remove SMS from your 2-factor authentication
SMS (text) has no place in your 2-factor authentication world. Remove it now and rely on a physical device (e.g. YubiKey) or TOTP (e.g. Authenticator app).
-

Creating the reliable cloud with unreliable components
Secure. Reliable. Economical. All three. We have embraced failures to create a reliable municipal hybrid cloud with unreliable components, economically.
-

Email Strict Transport Security with MTA-STS
Email security. A complex patchwork. Enable MTA-STS to get strict transport security on your STARTTLS.
-
What does your internal enterprise application login look like?
Whether your app is municipal, industrial, financial, or just vacation-booking-HR, it needs a strong, 2-factor auth system. Else you teach bad habits.
-
Hear Agilicus Talk Secure Municipal Cloud At MISA INFOSEC 2019
Take internal applications usable only by City staff with Active Directory, and make them Internet, Web, OpenID Connect, Secure, Simple, Fast. Easy!
-

Team Agilicus gets new office, Okterbest-adjacent
Team Agilicus moves to new permanent offices, assembles some desks, attends Oktoberfest. Progress!
-

Kustomizing Kustomize: Releasing Our Tools
Declarative. It becomes a way of life. We have chosen kustomize to safely build our inventory of YAML, including Istio and Cert-Manager. But, it has proven incredibly non-DRY. After some […]
-

Declarative GitFlow: restrict kustomize to master branch
Prevent accidents from happening on un-merged feature branches with GitFlow and kustomize.
-
Defense in Depth: Securing your new Kubernetes cluster from the challenges that lurk within
Cloud Native Day Presentation. The dangers that lurk inside your Kubernetes Cluster, what to watch out for.
-

Cloud Security Blasphemy: Secrets in git
Ever wondered why so many breaches happen due to secrets being checked in to source control? Want to make it easy to commit them to git, and be secure at the same time? Read On!
-

Keep your certificates young and fresh
TLS certificates, unlike wine, do not get better with age. Refresh them before they hit the end of their lifecycle.
-

We are all-in on the TLS: the HSTS preload
TLS, HTTPS. These are an important step in defence in depth. Get your entire domain on the https-only list at hstspreload.org, thank me later.
-

Git ransomware: beware the misdirection
Github ransomware. It might be a misdirection to hide more surreptitious changes to the codebase for you to import into your cloud.
-

Covert Exfiltration, Cloud Native
Your virtual-private-cloud private IP setup still has access to key API’s such as storage and messaging. Have you considered exfiltration through these?
-

Moving into a new (cloud) neighbourhood? Check its reputation!
Your shiny new cloud instances might be tarnished by the reputation of the last tenant. Use Shodan to check, and Greynoise to see if its above the norm. And above all, don’t panic!
-

Docker Hub Hack: Secure Your Supply Chain
Docker hub loses account info, deploy tokens for github + bitbucket. Supply chain security chaos should ensue. Or are we now too blase? Its not me, right?
-

That’s the kind of password an idiot uses on luggage: cloud security
Passwords. bits of plain text that end up everywhere in automated systems. etcd. A `secure` way to share secrets. The Internet. A place that everything is guaranteed to end up. This is a toxic brew, read on!
-

The naked cloud: elasticsearch is stretch but doesn’t cover security
Wide open elasticsearch on the Internet. Its common. The user usually believes since they use private IP (NAT) they are protected. Wrong.
-

Security of the upstream code, and, the importance of the egress firewall
Bad code can come in through our own import statements and software process. Do you run an egress firewall to protect the world from yourself?
-

Static Application Security for Nodejs (with Gitlab CI)
Static application security for nodejs and Gitlab CI without changing your containers. SAST the easy way using docker FROM.
-

Suffering sisyphean security solutions: make your chrome part of the solution
Use your desktop chrome to find software security flaws on sites you visit. And then fix (if your own) or notify (if not). Be part of the security solution.
-

Safely secure secrets: a sops plugin for kustomize
Secrets get committed to git, forgotten, and then resurrected by the wrong people later. Don’t let this happen to you, use sops. And be declarative, use kustomize. And do it with this cool new library I wrote.
-

They got in via the logging! remote exploits and DDoS using the security logs
Amplification attacks occur when a small request causes a larger response. NTP and DNS have both been prone to this, but now cloud logging? Read on!
-

Increasing the usefulness of your Kubernetes Ingress logging
Using fluent-bit annotations can increase the usefulness of your Kubernetes nginx-ingress logging. Create a custom regex parser.
-

When your security tools cost more than the thing they protect
The (memory) cost of all the security proxies can be higher than the thing they protect. Let’s look at Istio.
-

Protect your API key (and your credit rating)
Google API keys. Powerful. Commonly used on websites. But able to cost you a lot of money. Learn how to protect them and your wallet.
-

The supply chain security risk in action: ESLint
Software is eating the world. The software supply chain is very complex to understand and manage. One slip up upstream, and that code is in your image very rapidly. Continuous!
-

Have you set your security context recently?
Setting the security context in Kubernetes is something you need to do. Reduce the privilege as much as you can. Defense in Depth. It’s your friend.
-

Fluent-Bit log routing by namespace in Kubernetes
Fluent-Bit log routing by namespace or by cluster. Route the logs from the right input(s) to the right outputs in fluent-bit in kubernetes.
-

What a wicked NAT we weave: detangling the cloud
Cloud. It achieves its elastic nature using Load Balancers and Proxies. The sad side affect of these is they remove the source IP. Let’s try to bring it back.
-
Unix to the Rescue
Ever wanted to apply Kubernetes secrets without displaying or persisting the secret value? Well now you can: Unix to the rescue!
-

Today’s post brought to you by the letter ‘k’: quickly re-pull an image in kubernetes
Have you ever had a Pod in a Deployment that you wish would just pull the latest container image to see what’s up? Want to run the equivalent of `touch`? Read on!
-

Completely Complex Cloud Cluster Capacity Crisis: Cool as a Cucumber in Kubernetes
Keeping your cool during an upgrade is important. Let the scheduler do its work, you’ll reconverge to happiness.
-

Ceph in the city: introducing my local Kubernetes to my ‘big’ Ceph cluster
Like scalable storage? Like resilience, redundancy? Want to run your own Kubernetes cluster with great persistent disks? Let’s talk ceph!
-

Kooking Kontainers With Kubernetes: A Recipe for Dual-Stack Deliciousness
Kubernetes technically doesn’t support dual-stack (ipv4 and ipv6 simultaneously). What if you want to run some CI job in there that requires a localhost ::1 to bind to? Read on!
-

Helm, Kubernetes, and the immutable configMap… a design pattern
Add the sha-hash of a configmap contents to its name as a design pattern and simplify your Deployment restarts, knowing they always have the right value and don’t die on error.
-

Keep your cloud clean: HSTS preload
HSTS exists to secure your site, to enforce your HTTPS-only policy. Why not use it and put yourself on the preload list?
-

Laughably Loquacious Logging
Cloud logging. How much space does a typical keep-alive take if you log it? You would be shocked that 1 byte of log could be 32+ KiB of output space. Watch the entropy!
-

Security and the Cloud: The need for high bandwidth entropy
Randomness is needed for seeding encryption, particularly at session start. In an orchestrated cloud environment, we use a lot of it, but have no user to provide. What to do?
-

Snooping on your Kubernetes nodes containers without ssh’ing to it: dink
Want to see what ‘docker’ is doing on a Kubernetes node (logs, ps, images), or re-pull an image? Don’t want to ssh there? dink!
-

DoS’ing the cloud with logs
Could cloud logging be the next NTP amplification attack for a DDoS? A small input produces a larger output, the ingredients are there…
-

Using single-sign-on oauth2 across many sites in Kubernetes
Learn how to safely protect ‘internal’ or ‘development’ resources while having them on the public Internet. Simply.
-

Multiple Kubernetes contexts and your multi-coloured prompt
You are working with multiple clouds. But, you keep changing context and then accidentally applying something. Ooops. If only this could be simpler.Drop these two bits in your .bashrc. Now you can simply say ‘context foo’ and be in that context with a little bit of colour in your prompt to remind you.
-

I Declare is not the same as Make It So
Declarative vs Imperative. In a ‘declarative’ world I document the desired state, and it is the job of the system to ‘make it so’. In a declarative world you don’t need to worry about ‘how’, and you don’t need to worry about things later breaking… If they change, the system puts it back. In an imperative world, you instruct each step. Install that software, configure that port, etc. Does declarative work always? read on
-

When you throw in the towel on declarative
In a declarative world its all written down and checked into version control. No commands are used. Sometimes you hit a wall and have to punt. Here I show a simple workaround using `envsubst` for those times that declarative just doesn’t work.
-

pause: how to debug your Kubernetes setup
Sometimes you need a debug container hanging around to check something from within your cluster. You cobble something together, make the ‘command’ be ‘sleep 3600’ or ‘tail -f /dev/null’ and call it a day. But they don’t terminate gracefully. Let’s learn how to fix this.
-

Let’s Encrypt Staging. Curl without the -k
Are you lazy and use ‘-k’ to curl all the time when using Let’s Encrypt staging? Or worse, use snake-oil? Or even worse, use just http for ‘test’? Let me show you how to fix that, simply.
-

Speed your CI, decrease your cost. The preemptible node
Cloud Native means being resilient to unexpected changes, to achieving high availability through embracing failures rather than designing them out. Google has added ‘preemptible’ nodes to their Google Cloud, available to their managed Kubernetes. These nodes are a lot cheaper, but there’s a catch: sometimes they die! Can we make use of this? Let’s see, using our Continuous Integration runners of Gitlab.
-

‘first’ and ‘only’ are four-letter words in cloud. How to do something ‘once’ and ‘first’ in a Kubernetes Deployment
Cloud Native implies a continuum. A declarative world that has no special event that occurs when it is started or finished. Non cloud-native applications often have ‘start’ or ‘upgrade’ tasks that need performing. Things that need to be done ‘one’ or ‘first’ or at some lifecycle stage. How can we integrate these two worlds?
-

Let’s Encrypt Staging. Safely.
Let’s Encrypt. It makes it simple and free to have decent TLS security. But the staging environment intermediate cert is (rightly) not trusted. How can you safely use this? Find out!