Yet another internet-breaking zero-day vulnerability, Log4Shell, has hit the wire and likely sent your IT teams into a patching frenzy, or at least it should have. Log4Shell is creating attack vectors just about everywhere and likely triggered a patch-a-thon for your technology teams as they secured important business systems. But what about operational technology like the HVAC or smart thermostat?
Ignoring systems that may be deemed ‘unimportant’ in comparison to your revenue-generating technology stack will leave your organization open to compromise from the Log4Shell vulnerability. There are a number of operational devices embedded into an organization that can be compromised through Log4Shell and could become the source of lateral network traversal by a malicious actor.
What is Log4Shell?
Log4j is a very widely used logging ‘library’ for Java-based software. Through this library, an attacker can send crafted log messages that are able to execute any arbitrary code (spyware, malware, ransomware, etc.). This zero-day vulnerability has been named Log4Shell, identified as CVE-2021-44228.
The Log4j library is currently under the purview of the Apache Foundation. The library can be added to any Java-based software for the purpose of logging application and user inputs. The library is found in many different types of applications, servers, and services, most specifically enterprise software, IoT devices, and other external/internet-facing applications. That means everything from financial companies, to hospitality, or manufacturing and industrial operations could be vulnerable or even compromised already.
While Apache has released a patch, the vulnerability is still affecting very commonly used server software such as Apache Solr, Apache Druid, Elasticsearch, Apache Dubbo, and VMware vCenter. Nearly the entire big-data stack of self-hosted and managed operators runs this software (Spark, Druid, Hadoop, Elasticsearch), which means that ingested data could also be a risk, bypassing the firewall since it’s inserted by staff.
How it Works
What makes the Log4Shell vulnerability so concerning is that wherever an expression is invoked, a lookup mechanism can find and replace the value contained, which can then be used to run any executable file. Unfortunately, there are a variety of lookups supported by Log4j (JNDI, SYS, ENV, JAVA, lower, and upper).
For example, an attacker can use the JNDI expressions in the logs to execute an attack where they make an HTTP request to a malicious web server. The request to the malicious web server can then download and execute a malicious payload. This example is one of the most common ways this vulnerability has so far been exploited.
Essentially, Log4Shell can be used to execute some arbitrary code without checking who wrote it, where it came from, and what it is going to do, leaving servers, networks, and devices open to compromise.
The popularity of Log4j means malicious actors have a huge attack surface including:
- Network headers which get logged
- URLs, filename, paths which get logged
- Instant message routing, in-game purchases, user-names, comments in blogs, and more
Nearly any field which can be set by any user can be exploitable.
Why You Should Be Concerned
There are very few companies around the world that aren’t affected by the Log4Shell vulnerability. The prevalence of the Log4j library is contributing to the panic we are seeing, especially as organizations like Amazon Web Services, Broadcom, Cisco, ConnectWise, Fortinet, IBM, Okta, VMware have been impacted.
As these major organizations ensure the patches are in place and your IT team has told you “don’t worry”, or that you “are good”, ask yourself, “did anybody check the HVAC?” What about the IoT thermostat? How about the smart projector, printer, or router?
Protecting against the Log4Shell vulnerability goes beyond updating HTTP server headers. Technology teams need to take a holistic approach to review every application or device in the organization that could be using the Log4j Java library and what it is connected to.
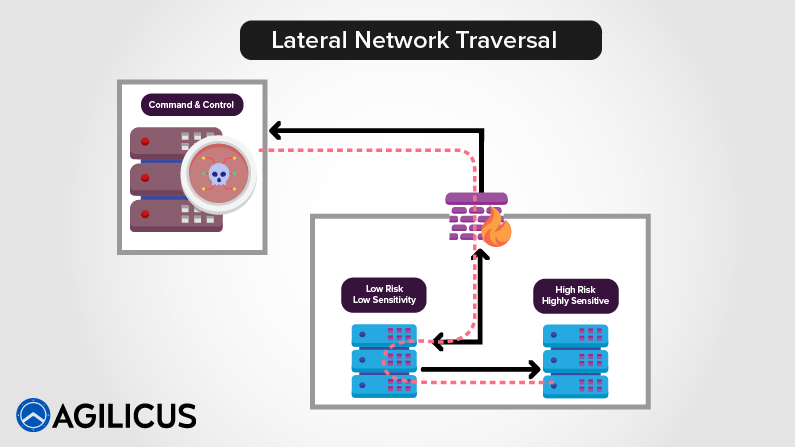
There is a huge universe of products, devices, and services we use daily that are also exposed to the Log4Shell vulnerability. Aside from cranking the thermostat up or down, the risk to an organization comes in when these devices are connected to or able to connect to an internal corporate network. Oftentimes these devices are a cybersecurity afterthought and can leave an organization vulnerable to lateral network traversal attacks.
In the case of the Log4Shell vulnerability, an unpatched afterthought like a printer or other operational device can be used to mount a man-in-the-middle attack and gain network access. After an attacker gains network access they will be able to traverse your network, snoop, steal, damage, and execute malicious software like ransomware. The net effect is that your network is crippled, your resources are compromised, and the business might find itself facing down a ransomware threat.
Another example of where Log4Shell can be used to gain network access is through any desktop software within your firewall or on your VPN is exploited. If a user can be influenced to open a URL or path with this magic string jndi://ldap, you may suddenly find yourself under attack from the inside.
So when you hear, “we’re good”, it might be appropriate to think twice about those cybersecurity afterthoughts and ask your team, “Has anyone checked the Smart Thermostat?”
What You Should Do
Evaluating your organization’s tech stack beyond the technology powering business activities, and keeping other devices in mind is a good step. The technology powering your facilities could very well be the doorway into your corporate network and if it is vulnerable to Log4Shell, malicious code could be easily executed on your network.
What should you do? Patching this zero-day vulnerability is of critical importance. If it can’t be patched, any exposed devices should be isolated from your network. You might also think twice about stopping at simply implementing a patch and instead start thinking about how you can harden your cyber posture with tools like Web Application Firewalls, or fine-grained Access Controls.
Another step in improving your resilience to these types of cyber risk events is ensuring your IT organization is using modern security frameworks like resource segmentation, Zero-Trust, Multi-Factor Authentication, containerized servers, and egress firewalls. Finally, having a great audit system could help you identify whether you’ve had an issue already and take the necessary steps to mitigate the event.
The depth of risk that Log4shell creates is showing the world that modern security problems require modern cybersecurity solutions. Advanced cybersecurity services can help you mitigate the risk of these types of zero-day attacks, which are only increasing in frequency with new ones discovered from one week to the next.
Agilicus helps organizations of all sizes implement advanced cybersecurity measures that are cost-accessible, easy to deploy, and introduce identity-based access control without the need for a VPN.