The ostrich has a novel approach to threats: pretend they don’t exist. Commonly known as the head-in-sand approach. Do you want to be an ostrich when it comes to vulnerabilities in your software, your web site? Or do you want to be a bit more open-minded?
Security researchers look for vulnerabilities. You may not even know of the existence of the security researcher nor the vulnerability they are researching. But, you may be susceptible to the attack they research. Getting that info into your hands will make it more likely you are on of the first to resolve the issue, the last to be attacked. And this can save you money.
Some organisations even offer “bug bounties”, recognising that paying a small amount may obviate the need to pay a large amount later.
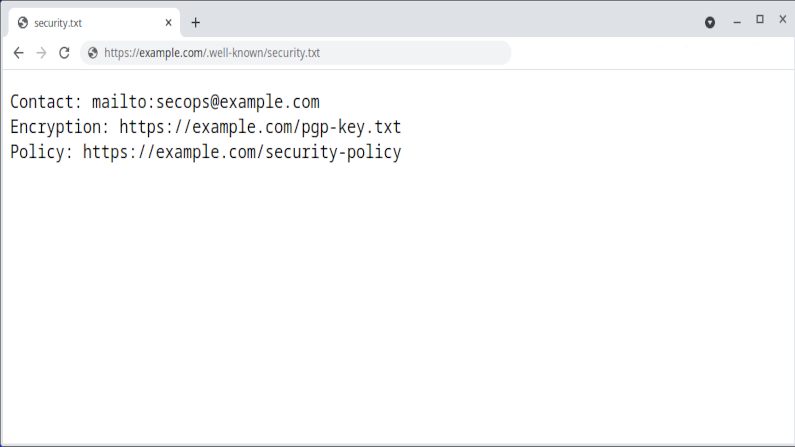
Now, the challenge. How do you document in a simple way for all to understand your policies, procedures, etc? Who should the security researcher contact? How should they authenticate themself? How will you authenticate yourself to them? Etc. Well the good folks at the IETF have a standard in progress on the topic called “A File Format to Aid in Security Vulnerability Disclosure“. The TL;DR is “add a file called /.well-known/security.txt to your web site”. A slightly more involved “overview’ can be found at “securitytxt.org“.
Will this standard change the world? No. Is it easy to implement? Yes. Does it have any downside? None that I can see.