Let me show you a very simple means of Open Source Intelligence (OSINT) on yourself. If I can do this, anyone can do this, and if anyone can do this, someone bad can do this.
Shodan
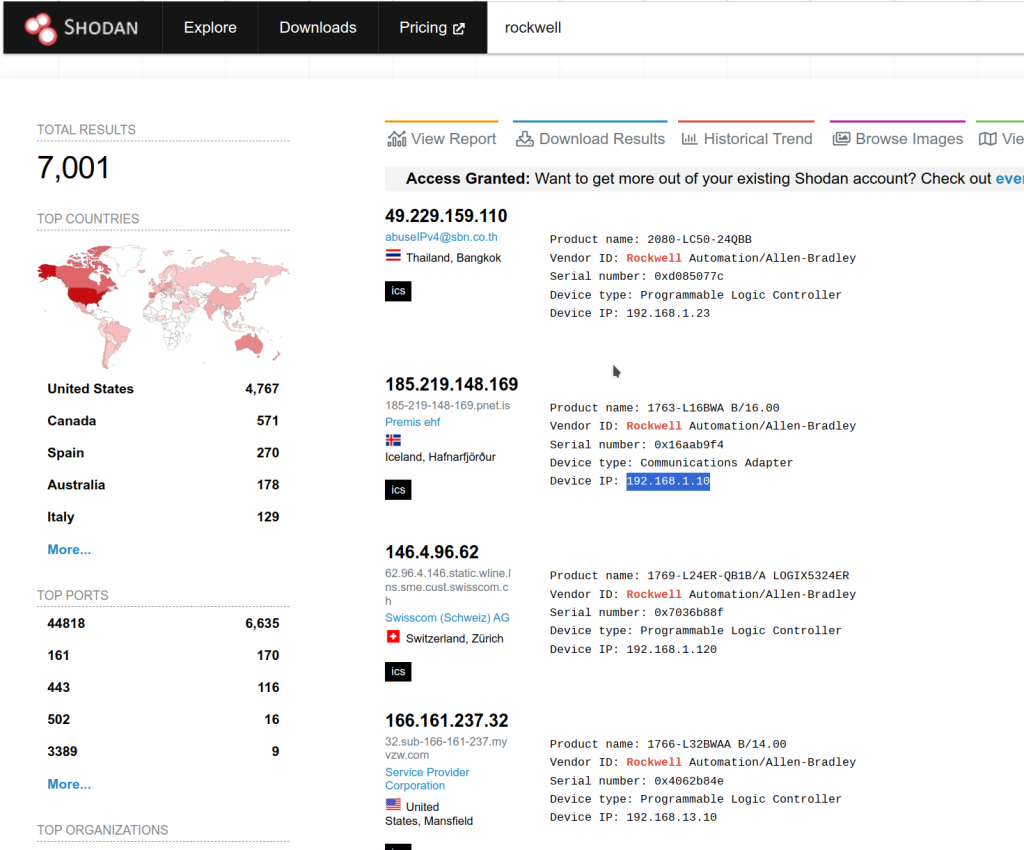
Head on over to shodan.io, type in ‘Rockwell’. Suddenly you can see a bunch of PLC that are publicly available via Ethernet/IP or modbus. Try this with some strings that mean something to your business, e.g. the main part of your domain name (so ‘agilicus’ from ‘agilicus.com’), etc. Do you see yourself? If so, so do others.
Here we can see a bunch of PLC’s, hanging out, with a lot of wireless carriers as the ISP. Let’s pick one and dig in, see what we can see. I will pick “166.169.157.23“, on myvzw.com (Verizon Wireless).
Now, we see a set of “Cards”, lets explore what they mean.
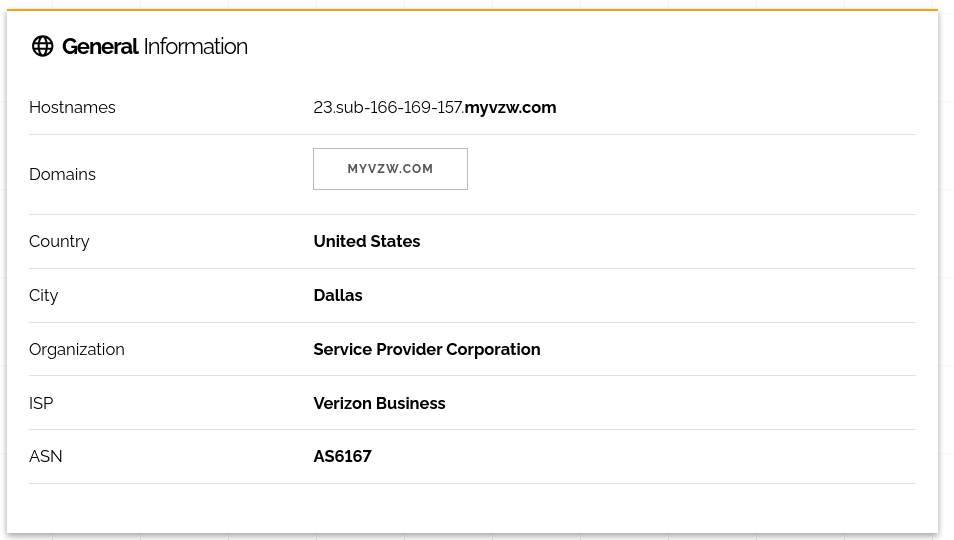
First, we see “General Information”. In this case, its not useful, since its genericall the ISP (Verizon Wireless) rather than a specific customer or site. Even the location is probably not valid since wireless is not fixed in location.
Second, we see some high level information on Web Technologies. Shodan has identified that jQuery is in use. We’ll look at this in a bit in the cURL and Browser section.

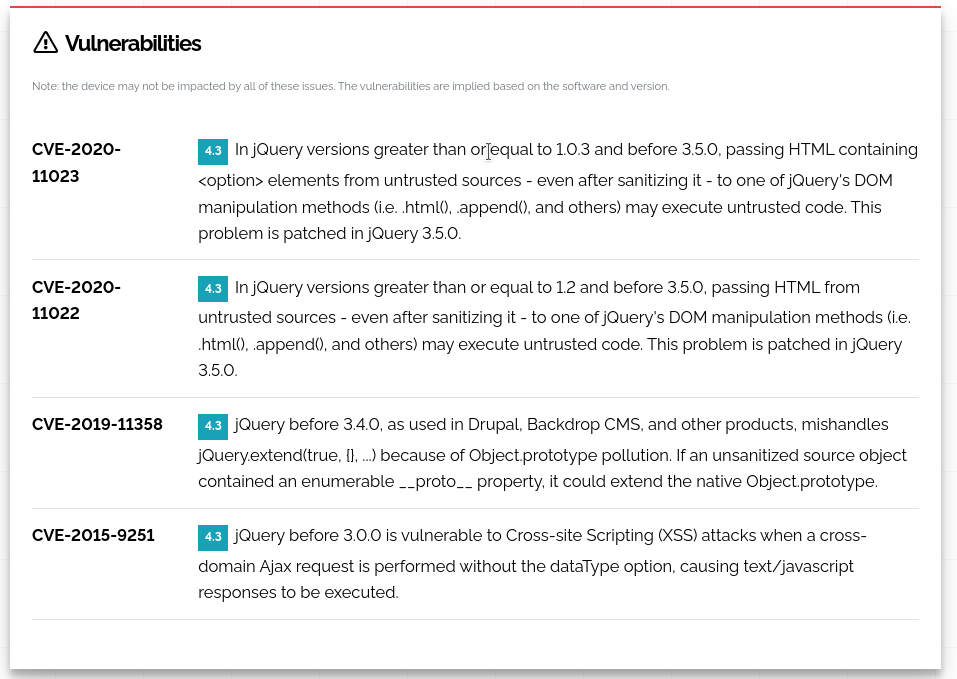
OK, now Shodan has taken a swag at vulnerabilities. Don’t consider this exchaustive, that requires a lot of work and more advanced tools like OpenVAS or Nessus etc. But, the list is non-zero, so we have some reason to think, and, perhaps be alarmed. These are all 4.3, so if this is is a mission-critical sign-in gateway, we might take action. If its something that doesn’t have any sign in, no csrf, no cookies, etc, we might not care.
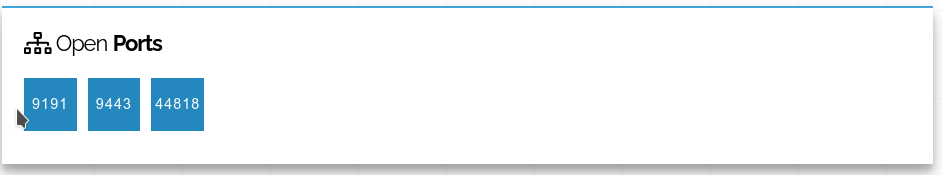
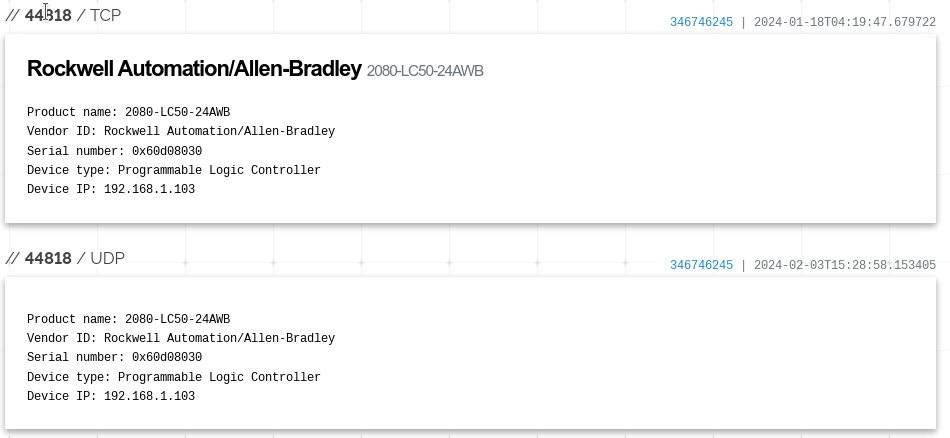
Now we get to the services. Shodan has identified 3 open parts, 9191, 9443, 44818. We can google these to see more detail, noting that 44818 is commonly used for EtherNet/IP, an industrial protocol commonly used by Rockwell Automation.
Shodan now shows us was it found in its earlier query. 9191 . It knows its a web server, but nothing more.

Now we find our first real clue. Port 9443, it has an SSL certificate. It was signed for Sierra Wireless, in 2015, and references eairlink.com.
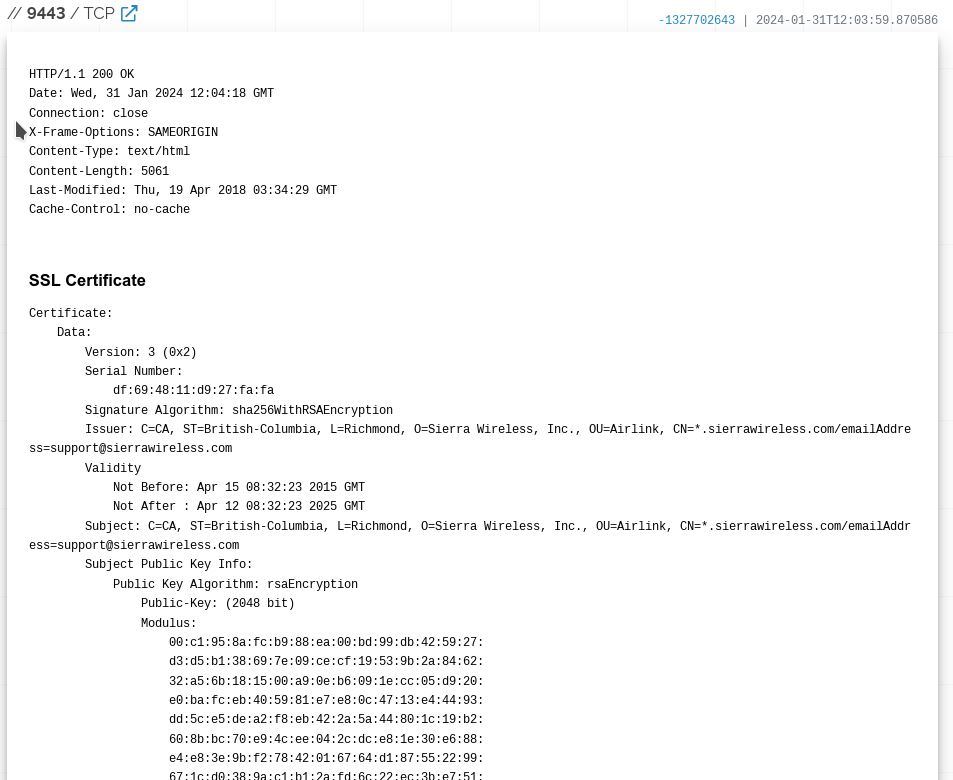
The real excitement comes on 44818, the EtherNet/IP. Spoiler, its not the Ethernet and IP you think it is, it is the Common Industrial Protocol.. Shodan has identified this is a 2080-LC50-24AWB, better known as a Micro850. A discontinued PLC. We also get another breadcrumb, which is the IP on the ‘local’ side, meaning we know at least 1 subnet past the gateway.
cURL and Browser
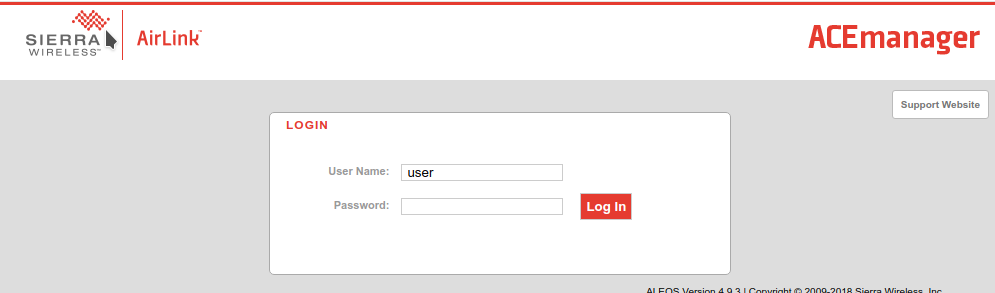
OK, we’ve learned a lot from Shodan, let’s see what else we can find. So, lets open a browser to the links above (http://IP:9191 and https://IP:9443). Suddenly we see a login screen, a product name. Its ‘Sierra ACEmanager’. Its also helpfully giving us the veresion: ALEOS Version 4.9.3
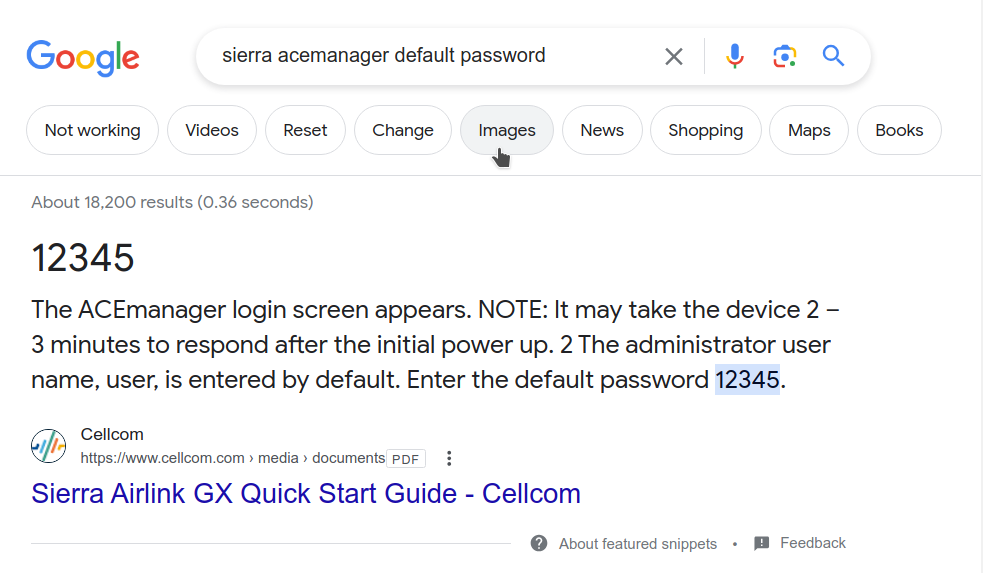
It takes but a moment to figure out the default password for this device.
NMAP
Now lets switch gears to that PLC.
# nmap --script enip-info -sU -p 44818 166.169.157.23
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-03 11:25 EST
Nmap scan report for 23.sub-166-169-157.myvzw.com (166.169.157.23)
Host is up (0.25s latency).
PORT STATE SERVICE
44818/udp open EtherNet-IP-2
| enip-info:
| type: Programmable Logic Controller (14)
| vendor: Rockwell Automation/Allen-Bradley (1)
| productName: 2080-LC50-24AWB
| serialNumber: 0x60d08030
| productCode: 157
| revision: 11.11
| status: 0x0034
| state: 0x03
|_ deviceIp: 192.168.1.103OK, that was easy, we know know the version of firmware (and confirmation of the internal IP and thus subnet).
CVE, Vulnerability

From here we can lookup some known vulnerabilities for our two devices (the Sierra Wireless and the PLC).
A simple search on ‘ALEOS Version 4.9.3 CVE’ finds an alert from CISA “Sierra Wireless AirLink with ALEOS firmware”. OK, that was easy. We now have a roadmap to 5 ways to take over the device (and this is ignoring the 12345 password issue from above). For the sake of argument, let’s assume we now can use this to gain full layer-3 access to the site, given the firewall is pretty vulnerable.
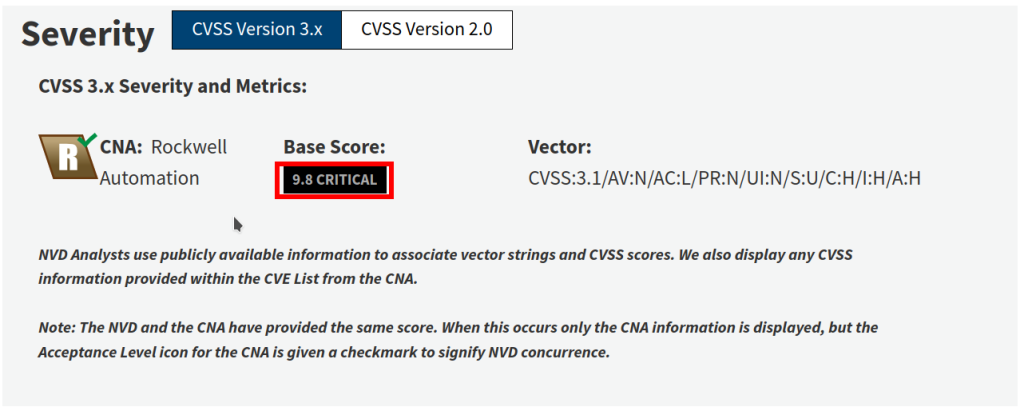
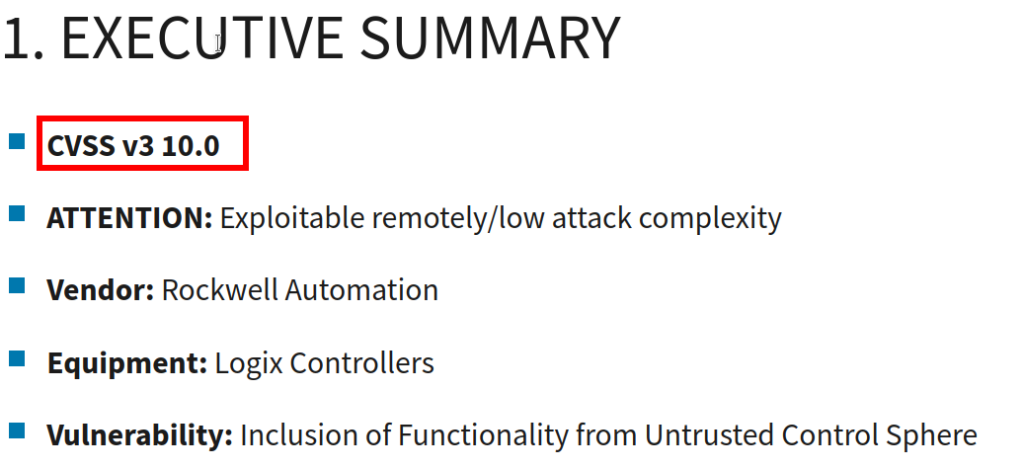
How about the one known device, the PLC? Well, there are a ton of issues referenced online. The EtherNet/IP protocol itself has no security, so we have a lot of room on that alone, but, CVE-2023-3595 seems like a good start for anyone who wishes us ill will, its rated 9.8 out of 10. If we are lazy, CISA has 10/10 one (ICSA-22-090-05) for us to dig into.
From here its an excercise for the reader to find the proof-of-concept code and exploit.
CVE and vulnerability are like an iceberg, for everyone known and reported, there is another set that are known and un-reported (the zero-days hoarded by bad actors), and for ever one of that set, there is another set of ones not yet found.
The known/known becomes the unknown/known, becomes the unknown/unknown. The ripples of risk expand.
Next Steps
The intent of this post was not to scare. It was not meant to demonstrate some deep knowledge of esoteric tools. Instead, I meant to show that the howto basics are a commodity. I don’t know where any of the sites i found in Shodan are, and I did not try to hack into them. But, anyone could, and someone will. Perhaps the example above is something deep in critical infrastructure: a water plant, an energy pipeline, a hydroelectric dam.
So my advice is, try hacking yourself. Its called red-teaming, capture the flag, pentesting, etc. If its eye-opening, then, well, use the knowledge, invest in some defense in depth, improve the authentication, authorisation, access, etc.
