In “Your VPN Hates Your Video Conferencing. Here’s Why” I discussed why VPN’s often very negatively impact the performance of non-corporate applications. End users often complain of performance on YouTube, performance on video conferencing, VoIP issues, etc. But VPN users also complain, since the corporate network upstream becomes their downstream, and someone else watching Netflix reduces the performance of all users.
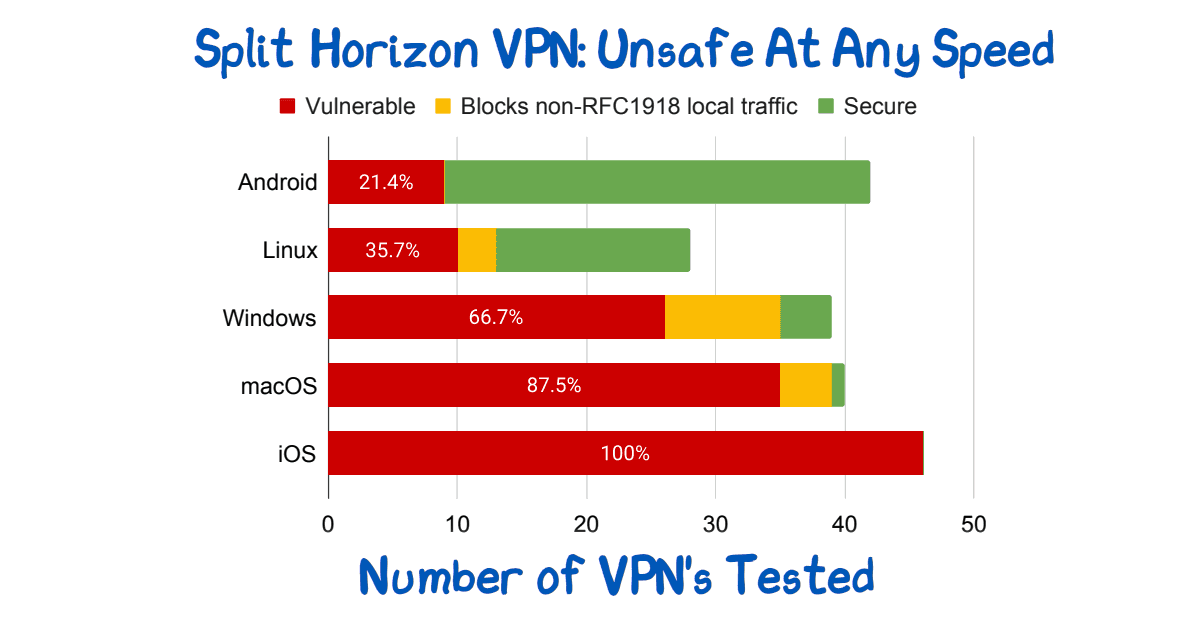
In each case, the reason is the same: in order to safely operate VPN, you must force all of the traffic into it. Companies often sacrifice security for performance by running what is called a ‘split horizon’ VPN. In a nutshell, a split-horizon VPN cherry-picks certain routes, forcing those to route into the VPN, but allowing others to use the default route, the default ISP. The end user may see this as better (since the performance is improved) but the security is dramatically reduced.
In “Bypassing Tunnels: Leaking VPN Client Traffic by Abusing Routing Tables“, the authors show just how dramatically that security is reduced. In particular, they note that 100% of VPN’s tested on iOS were insecure.
The attack vector is the routing table. Networks route to the most specific route (longest-prefix match). The corporate VPN, once configured for split-horizon, has a set of more-specific routes. A local ISP, wifi provider, etc, can in turn advertise even more specific routes, causing that traffic to be captured, altered, inspected…. things you do not want.
Is there a better solution? If the full-route VPN is too slow, and the split-horizon VPN is too weak, what should you do? We recommend a Zero Trust solution. In Zero-Trust Makes Working From Home Secure And Reliable, Unlike VPN, we discuss how making each resource available as its own, public endpoint, with appropriate authentication and authorisation, provides better performance, stronger security, simpler use. Everybody wins.
Read more of the Tunnelcrack paper including the author’s summary here.