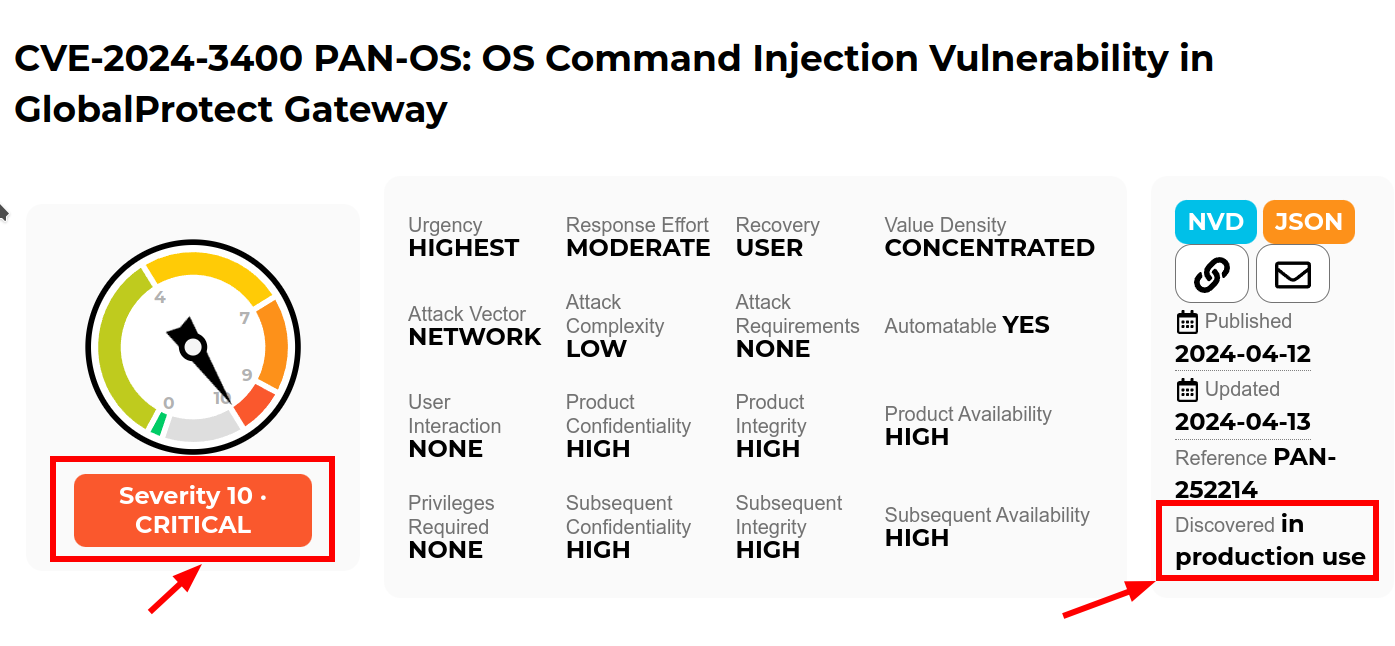
Recently Palo Alto announced a 10.0 CVE in the Global Protect feature of their PAN-OS firewall. “Unauthenticated attacker [can] execute arbitrary code with root privileges on the firewall”. Well, that is not good. But, how “not good” is it? It’s terrifyingly bad ungood in fact. Let’s discuss.
First, let’s think of the privileged position this firewall is in. It separates the trust from the non-trust. It is likely even used in a more complex zonal model, separating “Internet” from “DMZ” from “Desktops” from “Data Centre”. In fact, it can be a blueprint of where to look for someone. Fetch the firewall rules, look at the most restrictive blocks, and, well, attack there first.
Second, let’s think about other features commonly implemented on a NGFW. SSL Inspection. Its not uncommon in a corporate world to inject a “trusted CA Root Certificate” into all your devices and have the firewall inspect all the outbound traffic. And, where I say “inspect”, read “decrypt”. This means this device has the ability to read/write/modify all the traffic leaving your facility. Perhaps you have some JWT or API Key or Service Accounts used in your external cloud environment? Maybe your Identity Provider is a public one on Azure or Google. This firewall is reading your passwords in a proxyful fashion. And now, someone else owns it. A regular layer-4 firewall would be bad to breach, but one that you have taught to breach all your cryptography? Much much worse.
Third, how many of you have enabled proper single-sign-on, no-shared-account, multi-factor, for the administrative interface of all your network doo-dads and appliances? Right, none of you. So the miscreant which just waltzed into your Firewall via this attack probably now has the credentials to your other security appliances.
And, lastly, it was discovered in the field as a zero-day in active use. This means someone has known about it for perhaps a long time, and might have stealthily been using it until caught. This means… all your secrets are belong to us. Your backups. Your passwords. Your customer information. Your cloud SaaS data. The attacker might use this to spearphish your customers, business email compromise exploits, blackmail, who knows.
By having a fully-trusted device in the centre, we have facilitated what might have merely been bad to being worse. Much worse. That SSL inspection feature, once breached, that private SSL root key you installed, is a highway to hell when coupled with a critical exploit.
Now, the saving grace here, Palo Alto is acting responsibly. They have disclosed it, created a security advisory, and details on what they know. Imagine how much worse this would be if they were quiet and pretended it didn’t exist? “Palo Alto Networks is aware of malicious exploitation of this issue.” if instead of that they put some lawyer-language wishy-washy statement out?
So, once again, stop reading, start patching. And, when done, call me and let’s talk “Zero Trust” instead of “Fully Trusted”.