Secure Remote Access without a VPN
FAST, BETTER, SECURE
Equip your workforce with frictionless access to shared resources and eliminate the VPN with a secure alternative.
Agilicus AnyX is a modern alternative to remote access that is helping organisations go VPN-less to eliminate time, costs, and security risks.
Single Sign On. Multi-Factor Authentication. No Shared accounts. Single Resource permissions.
/imagae

How the VPN Introduces Cyber Risk
Virtual Private Networks (VPNs) have served as the digital backbone for most organisations and businesses over the last 25 years. However, this perimeter-based approach to access has a multitude of attack vectors and is no longer a match for modern cyber threats. Recently, an attack on an energy pipeline via the VPN vector brought this risk to mass-media attention.
Unauthorised access via the VPN can lead to a number of cyber attacks including lateral traversal, ransomware, and data exfiltration. By design when a user has access to resources on a VPN, they can also access everything on that VPN. VPN exploit is one of the most common attack vectors facing organisation. Thus Secure Remote Access without a VPN is desirable.
Learn how Zero Trust offers a secure alternative to remote access »
Why It’s Time for a VPN Alternative
High Fixed Costs
Cost isn’t just a matter of user licenses and hardware. The more secure a VPN is, the greater the sacrifice in convenience and productivity, which translates into high fixed costs of operation.
Network-Wide Risk Exposure
A corporate VPN is an all-in solution that, once breached, exposes the entire network to lateral-traversal leaving users, applications, and customer and corporate data vulnerable.
VPN’s Trust Users by Default
Once a user gains access to the VPN, they are trusted by default, even if access was gained via compromised credentials. There is no real distinction between assailants and legitimate users.
The VPN was invented over a quarter-century ago. While the technology has seen drastic improvements, your VPN could be the attack vector that leaves your organization open to exploit by a malicious actor. It may be time to adopt a modern security solution that shifts access from the perimeter and binds it to the user.
CASE STUDY Secure Remote Access without a VPN
A VPN Alternative for Securing Remote Access to Legacy Applications
Learn how Agilicus AnyX is being used to replace the VPN at a water treatment facility and enhance security while enabling remote access to previously unsupported legacy applications.
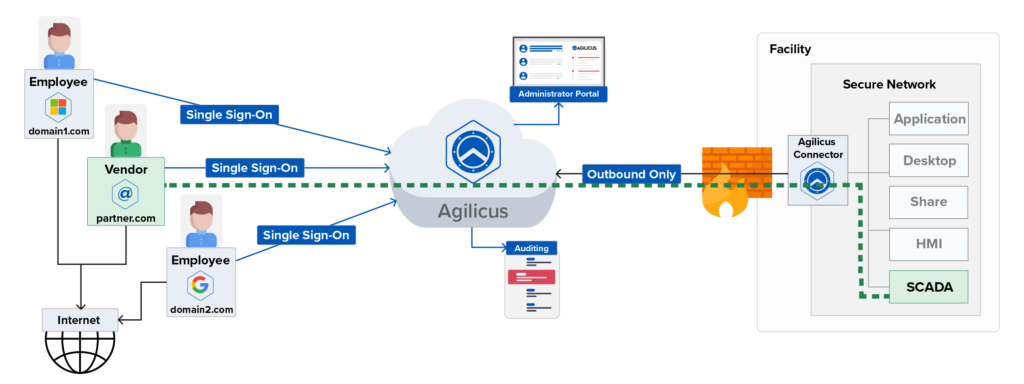
VPN-Less Access
With a foundation in Zero Trust, Agilicus AnyX requires all users to have the necessary permissions and prove who they are in order to gain access to company resources. This is achieved through a seamless login flow that leverages single sign-on and existing credentials to ensure the end user experience is frictionless and familiar. There are no new credentials, usernames or passwords.
Likewise, operators and administrators benefit from centralized user management where they can add or remove users, leverage role-based access controls, and control permissions through fine-grained authorisation.
With Zero Trust, there is no traditional network edge. Networks can exist in the cloud, locally, or in a hybrid form and users have access to only the resources they need to do their work. Quickly adopt a Zero Trust Architecture without the need for a client, VPN, or network changes to achieve Secure Remote Access without a VPN.
VPN-Less Access with Agilicus
Ease of Implementation
Quickly enable secure access under a zero trust framework that doesn’t require end-user clients or network changes. Improve your cyber posture while making it easier for your workforce to get access to only the systems and resource they need.
Any User, Any Device
Easily extend access to employees, contractors, partners, and third party vendors using their existing corporate email ID. That means no new user names, passwords, or active directory licenses.
Role-Based Access Controls
Manage users’ permissions across roles through a single administrator portal. Get granular control over user privileges (read, write, admin, owner) and adopt least privilege access principles. Pair users with resources, rather than entire networks.
Audit System
Improved Risk and Security Analysis with per user, per application auditing capability. Get visibility with accurate information on who accessed what, when, and for how long.
Off the Public Internet
Keep organisations secure, making them accessible to authorised without being visible on the public internet. Ensure only the right user, with the right level of access is able to connect via a secure, outbound only connection.
How Agilicus AnyX Works
Get In Touch
Ready To Learn More?
Agilicus AnyX Zero Trust enables any user, on any device, secure connectivity to any resource they need—without a client or VPN. Whether that resource is a web application, a programmable logic controller, or a building management system, Agilicus can secure it with multi-factor authentication while keeping the user experience simple with single sign-on.