One thing all industrial control installations have in common, they straddle the complexity of modern information technology with the dangers of operational technology and its inherent control of things which can go bump and boom. They have Hard Industrial Cybersecurity, but are hardly secure.
My observation of industrial installations is that policy and technology choices often make it hard for people to operate securely, and, they inevitably find a way to make it simpler, at the cost of security. If its hard to operate securely, it becomes hardly secure.
One of the most common risks comes around the authentication system. The air gap architecture of the typical plant, whether its a waste water treatment plan, a nuclear waste processing facility, energy, etc, makes typical cloud services unavailable. And, this removes the common single-sign-on, necessitating a parallel identity scheme. And, this means that users, forced to remember this parallel password with different rules fall back, as you would expect, to the 3 big risks:
- sharing the password with other users
- sharing the password with other less secure systems
- writing the password down
In the Oldsmar water treatment hack, a desire for efficiency caused users to add a parallel access system (TeamViewer) with shared passwords. In the Colonial Pipeline attack, a VPN with a parallel authentication system, shared with external partners, gave deep and wide access, allowing ransomware to wander in.
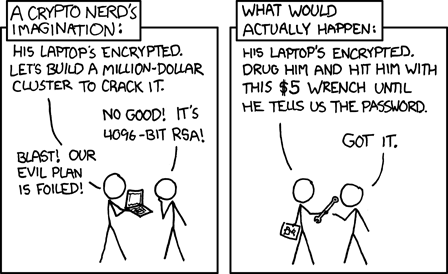
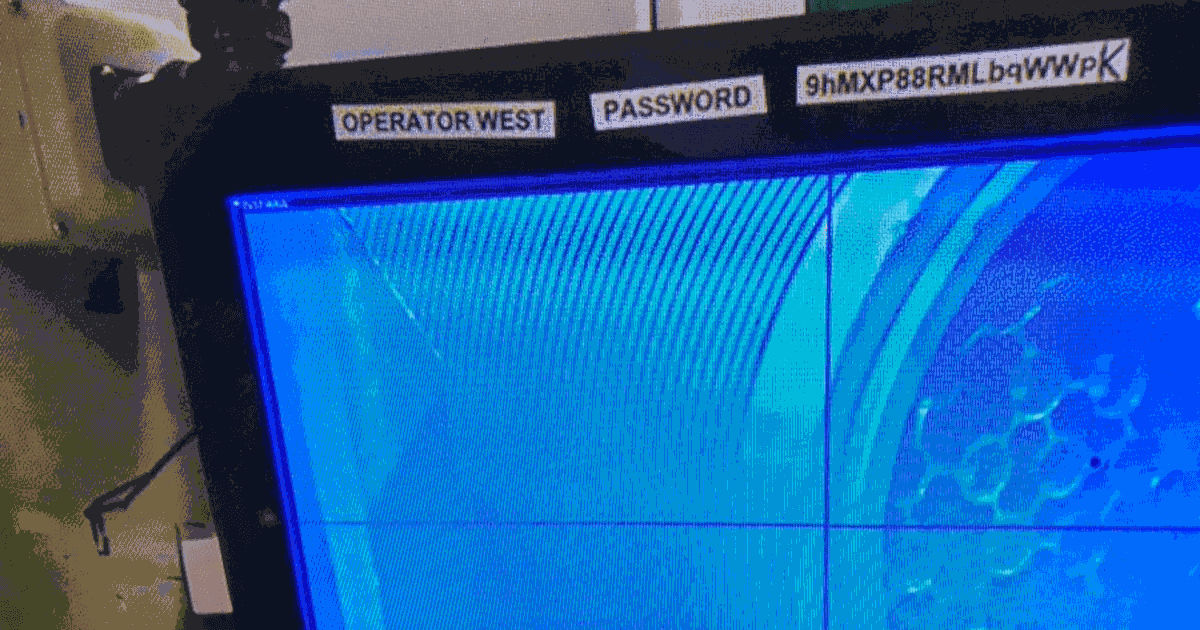
In the featured image above, we can see a TV crew given access to a nuclear processing site (Stellafield) uncovering the dirty secret of ‘writing it down’. The password looks hard to remember, and, seems to be on a shared console (shared account). It makes me think of one of my favourite xkcd comics, the committee coming up with the password rules on the left, and the operators on the right:
Now, traditionally in cybersecurity we think of money as the objective. And, if its not money, its reputation. But here, in a nuclear waste plant, the penny might be dropping. The downside might not be $ or resigned CISO’s, but, might be far more sinister. Its the health and welfare of many people that makes this require Hard Industrial Cybersecurity.
So what is the solution? If unguessable passwords are defeated by postit and TV, what can we do? Make it simpler to be secure. If all users can use their existing, native, account across all systems, with a simple single-sign-on that is common, consistent, familiar, they are much less likely to move to ‘shared’ alternatives, written down alternatives.
To achieve this Hard Industrial Cybersecurity, you need a form of unified authentication (allowing each of your own staff, your partner staff to sign in natively), you need a method of securely, precisely, narrowly, traversing that air gap. You need Agilicus AnyX Zero Trust.