Agilicus AnyX gives all your users a unified single sign-on experience that simplifies the end-user experience while enhancing your overall security posture. But what do we mean when we talk about ‘all users’ or providing a unified experience? And what are the best practices around that? This article will help you better understand those concepts and what Agilicus recommends.
Understanding Unified Authentication and Federated Identity
To understand why a unified single sign-on experience is valuable, we need to go over the concept of federated identity. Federated identity is a method of linking a user’s identity across multiple separate identity management systems. It allows users to quickly move between systems while maintaining security.
There are several advantages to this. If your organisation uses thirty different tools, all with their own individual login experience and credentials, it’s a lot easier to spear phish you since the user will not be expecting consistency, and will be expecting boxes that say username/password. With Agilicus, your users log into Google or Microsoft once and from there are signed into your resources, but you the administrator control what they can do, which significantly reduces this risk and better protects against threat actors. So from a security perspective alone, it’s incredibly useful. It’s also helpful for end users to log in once and then access multiple different tools without needing to login again.
When we say ‘all users’, this doesn’t just mean employees or internal users. It includes all of your external users too (like contractors or third-party vendors). Giving all of them a universal, secure, and straightforward access experience is what Agilicus AnyX does best.
Best Practices
Shared Identity Providers
Most users sign in via Google, Microsoft.
Google might be personal (gmail) or professional (workplace).
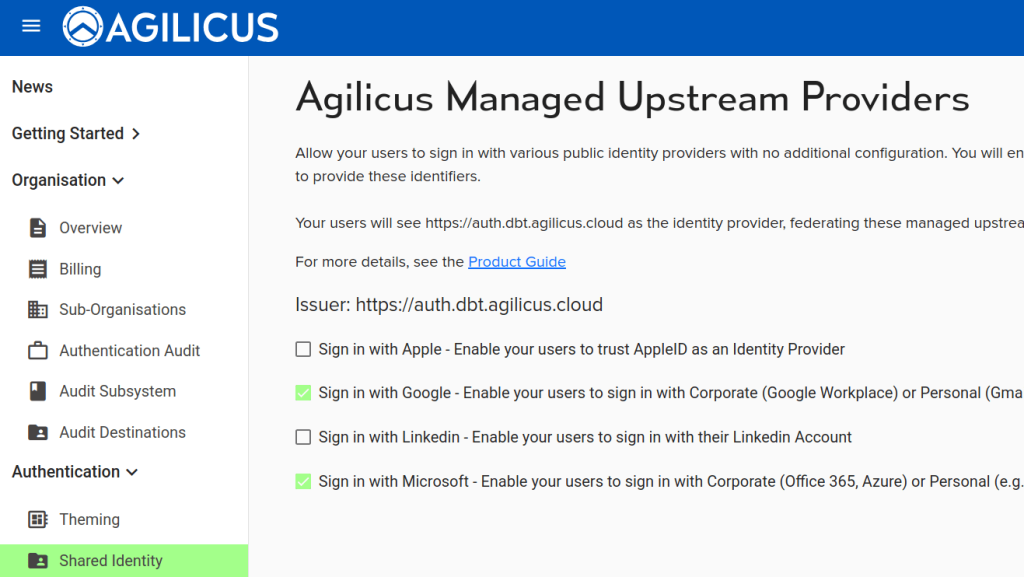
Microsoft might be Azure, Office 365,Active Directory, or hotmail.
For simplicity, these are one-click enabled.
One advantage to shared providers is it allows conveniently working with partners and their identity systems with zero config.
A downside to a shared identity provider relates to ‘auto creation’. It is usually not appropriate to auto-create users from a shared provider.
Configure Additional Identity Providers
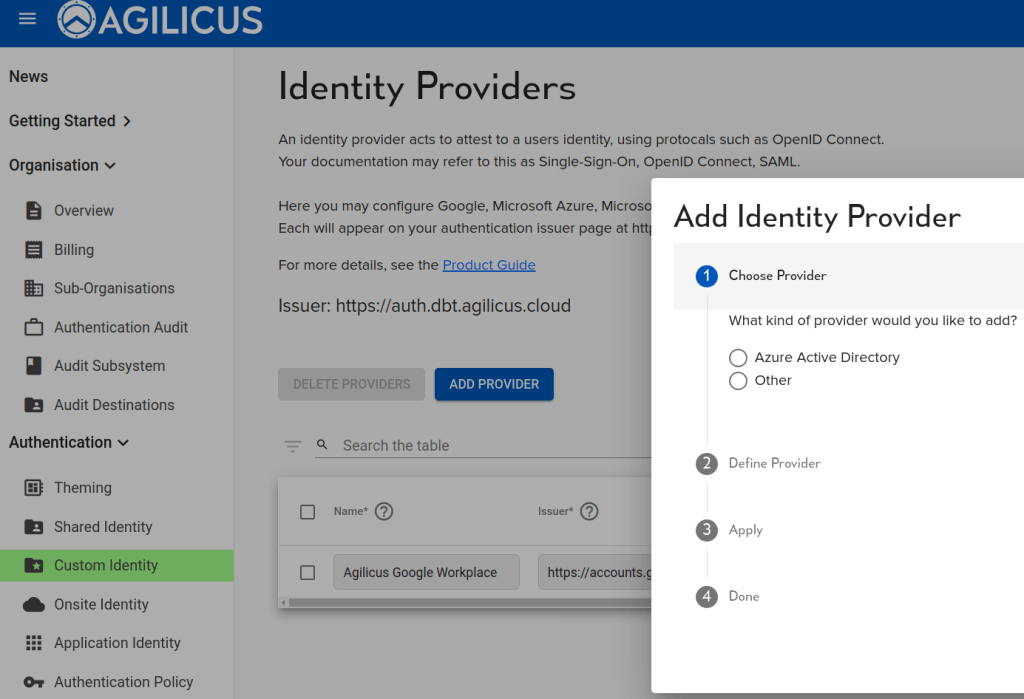
In most cases, you usually shouldn’t need to configure additional identity providers. We have what’s called a multi-tenant Azure Identity Provider. This means there is just a single instance of our software and its supporting infrastructure serves multiple identity providers like Azure and Google. Google is actually already intrinsically multi-tenant, so anybody who has a Google workplace or Gmail address can sign into our system.
Meanwhile, for Azure, we work with anybody that has Office 365 or Microsoft account, or an Azure account, but they have to allow it. You might have what’s called conditional access, which is sort of like embedded multi-factor authentication. You might want to control that in your own identity provider or a second identity provider.
For more information on this, refer to our breakdown of Azure consent flow in the Agilicus AnyX product guide.
Multi-Factor Authentication
It’s not a best practice to do multi-factor authentication twice in a row with different types. And so if Company A has multi-factor authentication embedded in their identity system, but Company B doesn’t and Company C assets that everybody must use multi-factor authentication, how do you make everyone happy?
So what Agilicus would do is use our authentication rules to say, if the identity providers don’t do multi-factor authentication, we’re going to force it. This allows you to achieve your corporate objective of everybody having multi-factor authentication without making users do it twice.
Conclusion
By understanding our unified single sign-on experience and these best practices, you’re on your way to simplifying your end-user experience while enhancing your overall security posture
If you have any feedback, questions, or are experiencing any issues, message our team via the chat button in your administrative portal or email us at support@agilicus.com.
