Agilicus Philosophy: The Backstory
Our background. The origin story. Updates on how team Agilicus view the world.
Overview
Our background. The origin story. Updates on how team Agilicus view the world.
Small batch sizes. Continuous integration.
Focus on organisational learning.
Bringing advanced technology to make security simple and accessible.
-
Agilicus Loves Let’s Encrypt™
Agilicus builds the best Zero Trust technology. It’s built on the best encryption, and the best certificate authority, Let’s Encrypt. Our business would not be possible without their good work.
-

Ready to Strengthen Canada’s Cybersecurity Ecosystem: Agilicus Qualifies to Sell Directly to the Government of Canada
Agilicus has successfully qualified to sell its innovative Zero Trust solution directly to the Government of Canada. This will help us bolster Canada’s cybersecurity ecosystem and help agencies defend against cyber attacks.
-

Helping Organisations Qualify and Obtain Cyber Insurance – Ridge Canada Cyber Solutions and Agilicus Partner
“We are thrilled to partner with Ridge Canada to help SMBs who are scrambling to implement security controls, including multi-factor authentication and privileged access management for their cyber insurance”
-
570 News Agilicus Interview
Interviewed on 570 News Tech Spotlight. listen to the interview here, I talk through some of the simple risks and how we help. And a bear joke.
-

Agilicus Awarded Government of Canada Contract
We are pleased to announce that Agilicus has been awarded a Government of Canada Contract with Shared Services Canada (SSC). The feedback and interaction we receive from such a marquis customer on our Any X Zero Trust platform is very valuable to us, and great validation of our ideas and technology.
-

Agilicus Recognised as a Top 100 Tech Company to Watch in 2022
We are incredibly excited to announce that Agilicus has been included in the FoundersBeta Top 100 Tech Companies to Follow in 2022. Every year FoundersBeta compiles their list of the top tech companies that are disrupting markets and making waves in the industry. This year, Agilicus caught their attention with it’s, cloud-native cybersecurity platform that […]
-

Agilicus In The News: Kitchener cybersecurity firm makes remote work access simple, secure
The Record published an article today on Agilicus. It covers the back-story on what we have set out to accomplish
-
Tech Spotlight: An Impromptu Interview
Interview w/ CityNews 570. Hear the origin story of Usenet in my life, and the plan to buy Doritos. And don’t call me old, I’m experienced!
-

Agilicus Named CIX Top 20 ‘Canada’s Most Innovative Companies’
Agilicus, a leader in Zero Trust Network Access, solutions is named one of Canada’s most innovative technology companies by CIX Top 20 Early annual award.
-
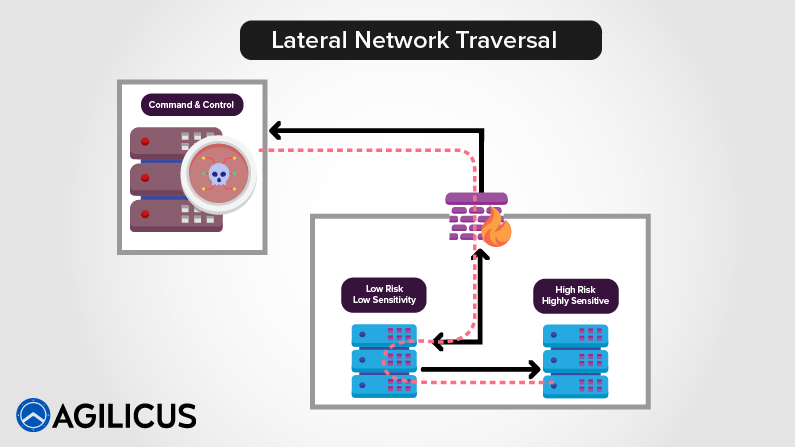
Security Report Chain: The vulnerability reports we receive
Security.txt and policy are enabling inbound reports, but the reports are not all equal quality. Should I pay for incorrect ones?
-

Brand Indicator Achievement unlocked: BIMI and you
BIMI is a new standard for logo protecting your brand email from identity theft. Implement with DNS and DMARC today.
-

Agilicus Story: Cloud Native Computing Foundation Stories
Agilicus presents its architecture, philosophy, strategy at CNCF Eastern Canada Stories Meetup
-
The Philosophy Behind The Name
Agilicus. Its a compass on a shield, reminding us of the need to protect from the east-west traffic. But what about the name? The icus part invokes Spartacus (from which the Spartan shield of the Logo derived). But the Agil part? That comes from Agile, Continuous, small batch sizes. In this video I talk a […]
-
Hear Agilicus Talk Secure Municipal Cloud At MISA INFOSEC 2019
Take internal applications usable only by City staff with Active Directory, and make them Internet, Web, OpenID Connect, Secure, Simple, Fast. Easy!
-

Team Agilicus gets new office, Okterbest-adjacent
Team Agilicus moves to new permanent offices, assembles some desks, attends Oktoberfest. Progress!
-

We are all-in on the TLS: the HSTS preload
TLS, HTTPS. These are an important step in defence in depth. Get your entire domain on the https-only list at hstspreload.org, thank me later.