DevOps: How We Build
Overview
DevOps. Comining development practices with Operations practices. Shifting things left. Moving to a more continuous cycle of integration and delivery.
DevOps has spawned a culture. A set of tools. It is highly complementary with Agile, of which Agilicus is a strong proponent.
-

Core Web Vitals WordPress Improve Recaptcha Performance
Core Web Vitals WordPress performance is important for user experience, for search optimisation. Learn how to improve wordpress and recaptcha CWV.
-

Speedup WordPress By Dequeue Unused Scripts
Speedup wordpress by dequeing unused scripts and css. The Events Calendar is used as an example. Faster load, less parse, better core web vitals.
-
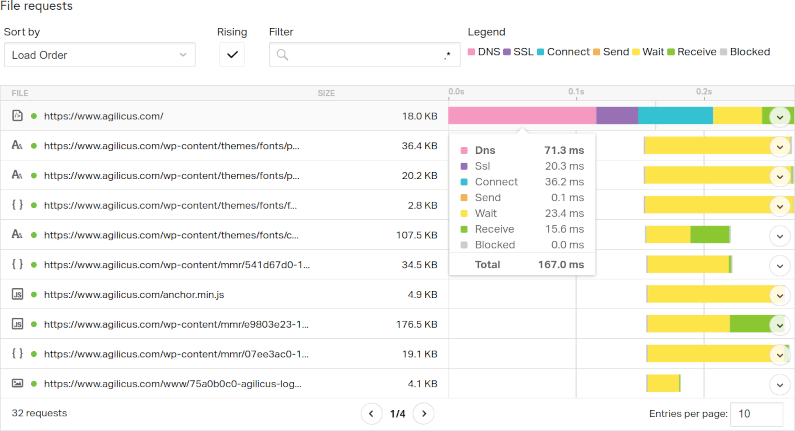
Its Always DNS: Latency In Web Load Time
Latency, specifically DNS Latency, is a big factor in web page load time. Don’t over-focus on bandwidth, examine prefetch and latency to improve.
-
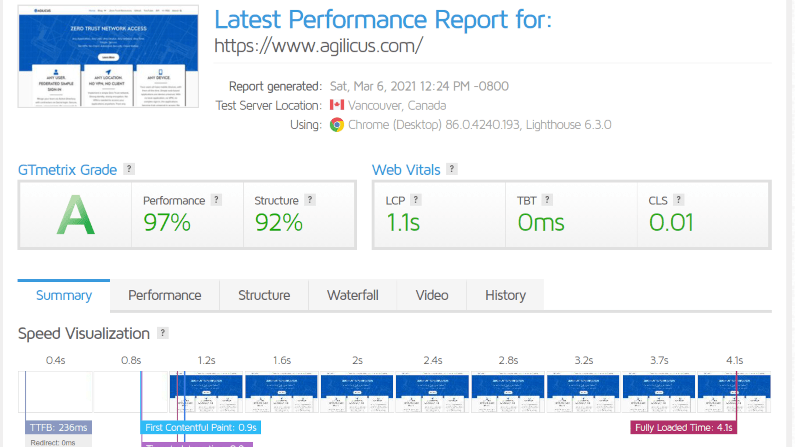
The Quest For Web Site Performance Perfection
Web site performance. Search engines favour sped. Milliseconds matter. Performance is as important as the content, as important as the appearance.
-
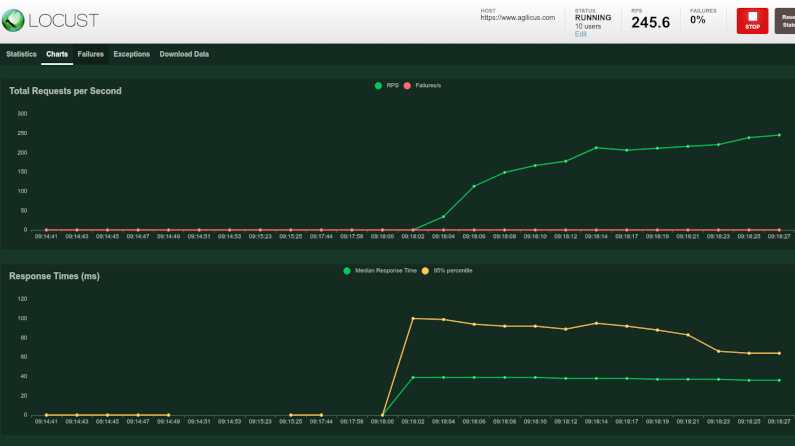
Latency And Load Testing Your Web Site With Locust and Istio
Your web site uses new technology. Shake it down by using your Sitemap for Latency and load testing with locust and istio.
-

Embrace Failures: find the start times of Kubernetes pods
Cloud Native: embracing failures. Assume Strength in Numbers. Don’t spend large time on a single infinitely reliable thing, assume each component will fail.
-
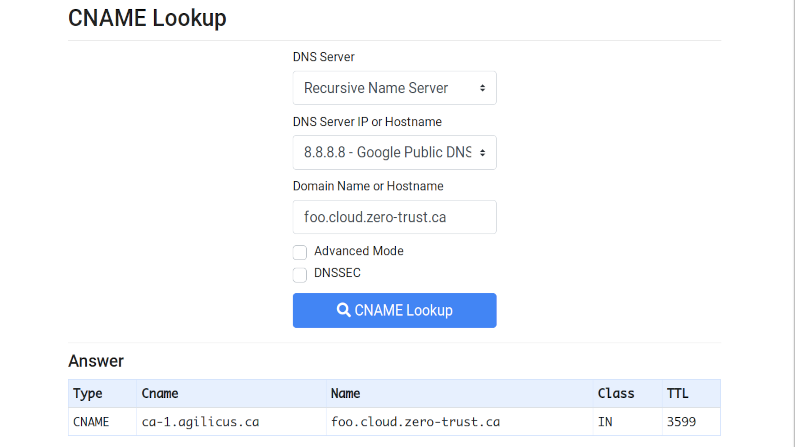
Internet Redirect & Alias: The CNAME
CNAME. Invented in 1987, used in today’s SaaS. See how your domain can be shared with your partners.
-

Dockerhub and pull limits: cache some insurance
Concerned about the new dockerhub rate limits? Run Kubernetes? Run CI? Deploy a pull-through cache simply to reduce the risk and impact.
-
The deep rabbit hole of email in cloud
Email. Port 25. Security. Spam. Its more complex than it used to be to be a good Internet citizen for email sending. Cloud edition.
-

Delicious Dogfood: Cloud Native WordPress
Take WordPress. Modernise it. Make it cloud-native. Add tidb cloud-native database. Add stateless storage.
-

Finding your Google ID and reclaiming your Gitlab account
OpenID Connect, a powerful single-sign-on with strong security, and locking the user to the upstream ID means if their name changes you are insulated.
-

Logging real remote address with Nginx and Lua
For audit, security, tracing, we want the origin IP logged. Load-balancers can mask this. Learn how to log the true client IP from nginx with lua, when that nginx is behind a load-balancer (reverse proxy)
-

Tame the legacy beast with API’s
Large legacy systems hold our data hostage. Tame their grip with REST-ful API’s and microservices. Fear no more on upgrades or even replacements.
-

Creating the reliable cloud with unreliable components
Secure. Reliable. Economical. All three. We have embraced failures to create a reliable municipal hybrid cloud with unreliable components, economically.
-

Kustomizing Kustomize: Releasing Our Tools
Declarative. It becomes a way of life. We have chosen kustomize to safely build our inventory of YAML, including Istio and Cert-Manager. But, it has proven incredibly non-DRY. After some refactoring etc, I made a few Generators and Transformers to cover some of the most common cases. And, today, for the low low price of […]
-

Declarative GitFlow: restrict kustomize to master branch
Prevent accidents from happening on un-merged feature branches with GitFlow and kustomize.
-
Defense in Depth: Securing your new Kubernetes cluster from the challenges that lurk within
Cloud Native Day Presentation. The dangers that lurk inside your Kubernetes Cluster, what to watch out for.
-

Cloud Security Blasphemy: Secrets in git
Ever wondered why so many breaches happen due to secrets being checked in to source control? Want to make it easy to commit them to git, and be secure at the same time? Read On!
-

Keep your certificates young and fresh
TLS certificates, unlike wine, do not get better with age. Refresh them before they hit the end of their lifecycle.
-

That’s the kind of password an idiot uses on luggage: cloud security
Passwords. bits of plain text that end up everywhere in automated systems. etcd. A `secure` way to share secrets. The Internet. A place that everything is guaranteed to end up. This is a toxic brew, read on!
-

The naked cloud: elasticsearch is stretch but doesn’t cover security
Wide open elasticsearch on the Internet. Its common. The user usually believes since they use private IP (NAT) they are protected. Wrong.
-

Static Application Security for Nodejs (with Gitlab CI)
Static application security for nodejs and Gitlab CI without changing your containers. SAST the easy way using docker FROM.
-

Safely secure secrets: a sops plugin for kustomize
Secrets get committed to git, forgotten, and then resurrected by the wrong people later. Don’t let this happen to you, use sops. And be declarative, use kustomize. And do it with this cool new library I wrote.
-

They got in via the logging! remote exploits and DDoS using the security logs
Amplification attacks occur when a small request causes a larger response. NTP and DNS have both been prone to this, but now cloud logging? Read on!
-

Increasing the usefulness of your Kubernetes Ingress logging
Using fluent-bit annotations can increase the usefulness of your Kubernetes nginx-ingress logging. Create a custom regex parser.
-

When your security tools cost more than the thing they protect
The (memory) cost of all the security proxies can be higher than the thing they protect. Let’s look at Istio.
-

Protect your API key (and your credit rating)
Google API keys. Powerful. Commonly used on websites. But able to cost you a lot of money. Learn how to protect them and your wallet.
-

Fluent-Bit log routing by namespace in Kubernetes
Fluent-Bit log routing by namespace or by cluster. Route the logs from the right input(s) to the right outputs in fluent-bit in kubernetes.
-

What a wicked NAT we weave: detangling the cloud
Cloud. It achieves its elastic nature using Load Balancers and Proxies. The sad side affect of these is they remove the source IP. Let’s try to bring it back.
-
Unix to the Rescue
Ever wanted to apply Kubernetes secrets without displaying or persisting the secret value? Well now you can: Unix to the rescue!