KEY RESOURCES
Adopting Zero Trust with Agilicus AnyX
Learn how organisations are using Agilicus AnyX to adopt Zero Trust. Read more about industry best practices with our white papers, and learn why the platform stands out when it comes to enhancing security with our brochures.
Resources
Leveraging Agilicus AnyX to adopt an enterprise-grade, Zero Trust Architecture to enhance security and resolve access challenges. Learn more, read the case studies, brochures, white papers, and articles.
-
Agilicus AnyX versus Cloudflare Zero Trust
Compare mesh overlay VPN network technology Cloudflare Zero Trust to Agilicus AnyX. Agilicus AnyX versus Cloudflare Zero Trust
-

Managed Industrial Remote Access
Managed Industrial Remote Access Case Study: Customer Objections and Responses
-

Agilicus AnyX Configuration Security
Cloud Configuration: What is the exposure? How is it protected?
-
Agilicus AnyX versus Tosibox
Compare mesh overlay VPN technology Tosibox with Agilicus AnyX Zero Trust
-

Agilicus AnyX versus Nebula
Compare mesh overlay VPN network technology Nebula to Agilicus AnyX Zero Trust
-
Agilicus AnyX versus FortiSRA
Agilicus AnyX contrasted with Fortinet FortiSRA
-

Midland Texas Transforms Water Purification Cyber Security
The City of Midland, Texas chose Agilicus AnyX Zero Trust to secure its Water Purification plant
-
ACME Manufacturing Transforms Security and Efficiency with Agilicus AnyX
ACME manufacturing chose Agilicus AnyX to enable SAP access to a multi-division, contract-manufacturing environment. Safely, Securely, Simply.
-

Secure Remote Updates For Air-Gapped Systems
Challenges with, and solutions for, Secure Remote Updates in modern complex control systems deployed in locked-down, air-gap-style networks. Agilicus AnyX enables and secures remote updates for air gaps.
-
Agilicus AnyX versus Splashtop
Agilicus AnyX versus TeamViewer. Compare a Zero Trust Network Access system with full authentication, authorisation, versus a niche solution.
-
High Availability Dual WAN Remote Industrial Connectivity
Industry cannot stop. Industry is also commonly located in remote areas with less network connectivity choices. Learn how Agilicus AnyX facilitates High Availability Dual WAN Remote Industrial Connectivity.
-
Wastewater Zero Trust Remote Operations and Asset Management
Wastewater Zero Trust Remote Operations and Asset Management. Learn how this industrial control systems engineering company expanded their service offering with Agilicus AnyX.
-
Agilicus AnyX versus TeamViewer
Agilicus AnyX versus TeamViewer. Compare a Zero Trust Network Access system with full authentication, authorisation, versus a niche solution.
-
Subscription Model and Remote Access In Industrial Control
Subscription Model and Remote Access In Industrial Control. The quest for revenue creates risks for operation.
-
Merging Local Identity With Online Identity
Modern online Identity with Azure, Google, Okta. Manufacturing plants with Local Identity — onsite users Unify with Agilicus AnyX
-

How the Town of Mono Future-Proofed its Cybersecurity Infrastructure and Transformed Municipal Operations
The Town of Mono future-proofed its cyber security infrastructure and exceeded compliance requirement by transitioning to Zero Trust.
-
Starlink Remote Cameras: 3-Steps to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable Starlink Remote Camera inbound remote access, despite CGNAT. Access your security video from anywhere.
-
Zero Trust VTScada Twilio Alerts
Zero Trust VTScada Twilio Alerts. Monitor your VTScada system with Twilio. Without exposing its login to the Internet. Simple, secure, no config change.
-

Starlink and Synology NAS: How to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable inbound remote access to your Starlink and Synology NAS setup, despite CGNAT. Access your files from anywhere.
-

NIST SP 800 53 Mapping To Zero Trust
NIST SP 800 53 is a comprehensive set of security controls. Zero Trust Network Architecture is a technology. Explore the intersection.
-

Case Study: Apple Screen Sharing, Zero Trust, Multi Factor Authentication
Remote Apple Screen Sharing with Zero Trust, Single-Sign-On, Multi-Factor Authentication. Without a VPN.
-

Zero Trust VNC Remote Desktop
1-click VNC remote desktop, single-sign-on, multifactor authentication. Zero Trust VNC Remote Desktop provides high-convenience with high security.
-

How the City of Kenosha Transitioned to Zero Trust
How the City of Kenosha Transitioned to Zero Trust using Agilicus Zero Trust to achieve EPA compliance and gain multi-factor authentication, vendor security, audit trails, and network visibility.
-
NIST SP 800-53 in Critical Infrastructure
NIST SP 800-53 is a core part of the NIST cybersecurity framework. It provides mappings of controls to various other standards. Zero Trust is a complementary architecutre supporting these controls.
-
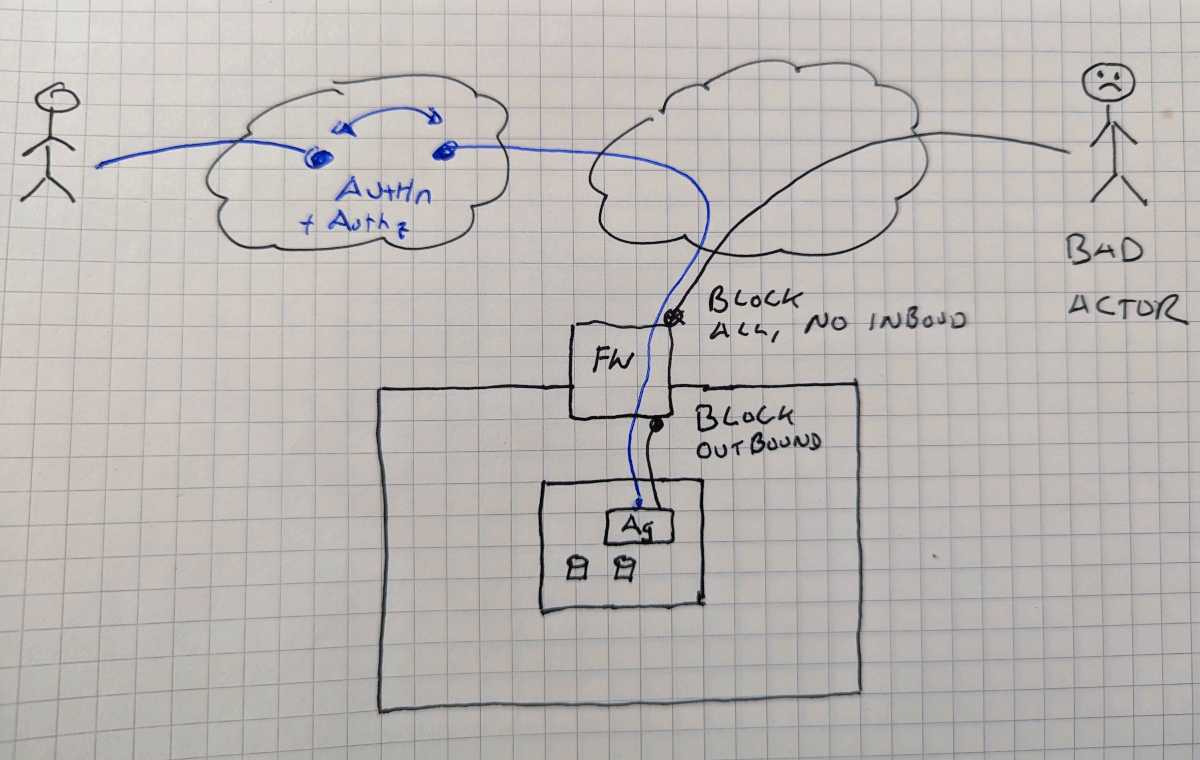
Zero Trust Air Gap Lock Down Inbound and Outbound
Air Gaps are a useful but inconvenient tactic as a part of a defense in depth strategy. Learn how a Zero Trust Air Gap Lockdown Inbound and Outbound can provide convenience and security together.
-
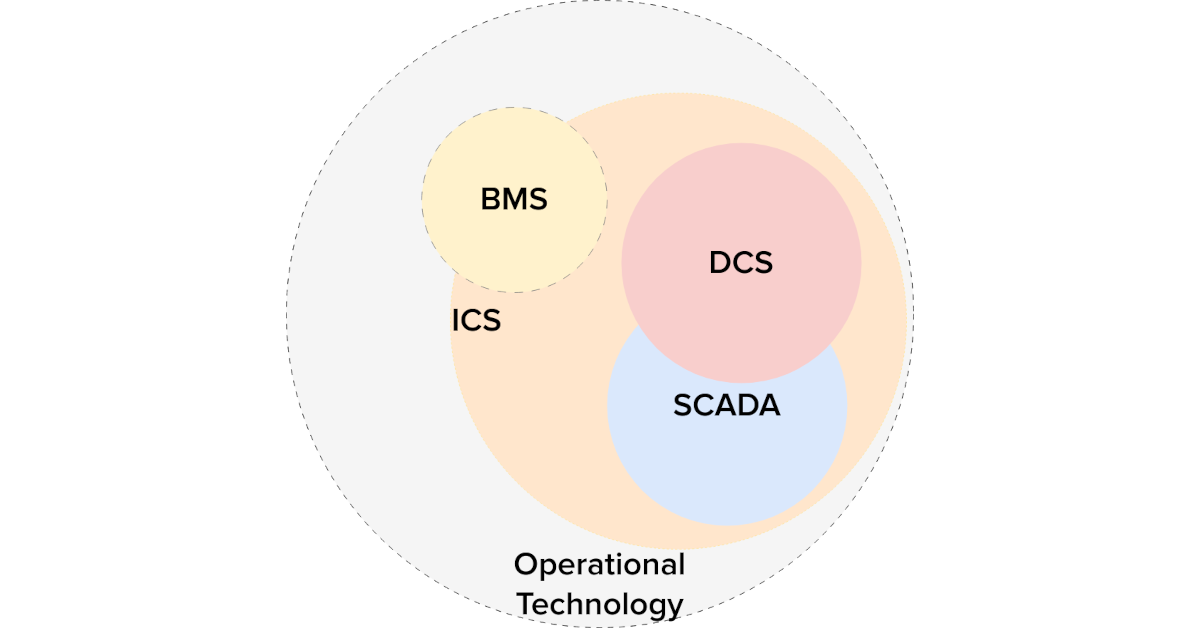
Piercing The Purdue Model: Zero-Trust In Operational Technology
Unravelling the interaction between the Purdue Model and Zero Trust: When married together in operational technology, the outcomes can be transformative.
-

Multi-Factor Authentication On The Internal Network
Cyber-Insurance compliance require multi-factor on internal network resources? Routers? Servers? Learn how to implement without a VPN, without changes.
-

Quickly Meet Cyber Security Insurance Requirements with Agilicus AnyX
Meet Cyber Security Insurance Requirements. Accelerate cyber readiness and reduce risk by adopting a network access and security strategy that meets compliance criteria while bolstering cyber defences organisation wide.
-

Case study: Protecting Critical Municipal Infrastructure and Securing Operational Technology at a Water Treatment Facility
Protect a municipal SCADA water treatment facility. Provide multi-factor authentication, secure remote access to staff and partners with single-sign-on.
-
Industrial Zero-Trust Micro-Segmentation
Micro-Segmentation Zones are a best practice for Industrial Control security. Simplify and increase effectivity with identity-based Zero-Trust. Industrial Zero-Trust Micro-Segmentation
-

Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture
Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture. Cyber threats come from all angles these days, yet most businesses are still ill equipped to properly keep the bad actors out.
-

Remote Desktop Access: Managing Cyber Risk with Zero Trust Network Access
Eliminate unmanaged cyber risk by securing remote desktop access through zero trust network access and improve your cybersecurity posture.
-
Case Study: Secure Access to Critical Infrastructure for Partners and Vendors
Critical Infrastructure for Partners and Vendors. A Municipality modernised a water treatment facility to enable secure connectivity for various internal teams (IT, Public Works), partner organisation, and their systems integrator.
-
Secure Remote Connectivity to 100 Critical Infrastructure Sites, Nationwide
A major systems integrator that services critical infrastructure across the United States seamlessly transformed their service model through Zero Trust, to reduce costs while enabling secure remote connectivity to over 100 customer sites. Learn how Agilicus AnyX was used to simplify access while ensuring the systems integrator could adhere to each customers expectations on security.
-
Enabling Secure Access to Web Applications through Zero Trust
Learn how Agilicus helped a Canadian Municipality extend secure access to web applications for mobile workers through a zero trust framework.
-

Strengthening Cybersecurity in Industrial Control Systems for Public Water Infrastructure
Secure and simplify your Industrial Control Systems to Improve Cybersecurity in Industrial Control Systems for Public Water Infrastructure
-

Third Party and Vendor Access Management for Critical Infrastructure
Adopting Vendor Access Management and enforcing multi-factor authentication for access to municipal critical infrastructure.
-

Add Multi-Factor Authentication to Legacy Systems with Agilicus AnyX
A municipality was seeking a method for securing access to the SCADA systems through the implementation of Multi-Factor Authentication.
-

Resources – Adopting Zero Trust with Agilicus AnyX
Resources: White Papers, Case Studies, Articles about how Agilicus AnyX Zero-Trust Network Architecture operates and the problems it has solved.
-
Case Study: A VPN Alternative for Securing Remote Access to Legacy Applications
A municipality in Southern Ontario was seeking a method of securing remote access to legacy applications – responsible for the treasury, billing, and permit functions.
-

Azure Application Consent
The Agilicus AnyX platform uses external Identity Providers rather than creating ‘parallel’ identities for users to remember. What permissions are being granted on those upstream systems?
-

Starlink Port Forwarding
Starlink. Good enough except for starlink port forwarding. Reach your devices from remote with Agilicus, securely, simply, reliably.
-

Quickly Meet Cyber Security Insurance Requirements with Agilicus AnyX
Meet Cyber Security Insurance Requirements. Accelerate cyber readiness and reduce risk by adopting a network access and security strategy that meets compliance criteria while bolstering cyber defences organisation wide.
-

Strengthening Cybersecurity in Industrial Control Systems for Public Water Infrastructure
Secure and simplify your Industrial Control Systems to Improve Cybersecurity in Industrial Control Systems for Public Water Infrastructure
-

Agilicus AnyX Configuration Security
Cloud Configuration: What is the exposure? How is it protected?
-

Secure Remote Updates For Air-Gapped Systems
Challenges with, and solutions for, Secure Remote Updates in modern complex control systems deployed in locked-down, air-gap-style networks. Agilicus AnyX enables and secures remote updates for air gaps.
-

High Availability Dual WAN Remote Industrial Connectivity
Industry cannot stop. Industry is also commonly located in remote areas with less network connectivity choices. Learn how Agilicus AnyX facilitates High Availability Dual WAN Remote Industrial Connectivity.
-

Subscription Model and Remote Access In Industrial Control
Subscription Model and Remote Access In Industrial Control. The quest for revenue creates risks for operation.
-

Merging Local Identity With Online Identity
Modern online Identity with Azure, Google, Okta. Manufacturing plants with Local Identity — onsite users Unify with Agilicus AnyX
-

NIST SP 800 53 Mapping To Zero Trust
NIST SP 800 53 is a comprehensive set of security controls. Zero Trust Network Architecture is a technology. Explore the intersection.
-

NIST SP 800-53 in Critical Infrastructure
NIST SP 800-53 is a core part of the NIST cybersecurity framework. It provides mappings of controls to various other standards. Zero Trust is a complementary architecutre supporting these controls.
-

Zero Trust Air Gap Lock Down Inbound and Outbound
Air Gaps are a useful but inconvenient tactic as a part of a defense in depth strategy. Learn how a Zero Trust Air Gap Lockdown Inbound and Outbound can provide convenience and security together.
-

Piercing The Purdue Model: Zero-Trust In Operational Technology
Unravelling the interaction between the Purdue Model and Zero Trust: When married together in operational technology, the outcomes can be transformative.
-

Multi-Factor Authentication On The Internal Network
Cyber-Insurance compliance require multi-factor on internal network resources? Routers? Servers? Learn how to implement without a VPN, without changes.
-

Remote Desktop Access: Managing Cyber Risk with Zero Trust Network Access
Eliminate unmanaged cyber risk by securing remote desktop access through zero trust network access and improve your cybersecurity posture.
-

Industrial Zero-Trust Micro-Segmentation
Micro-Segmentation Zones are a best practice for Industrial Control security. Simplify and increase effectivity with identity-based Zero-Trust. Industrial Zero-Trust Micro-Segmentation
-

Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture
Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture. Cyber threats come from all angles these days, yet most businesses are still ill equipped to properly keep the bad actors out.
-

Azure Application Consent
The Agilicus AnyX platform uses external Identity Providers rather than creating ‘parallel’ identities for users to remember. What permissions are being granted on those upstream systems?
-

Starlink Port Forwarding
Starlink. Good enough except for starlink port forwarding. Reach your devices from remote with Agilicus, securely, simply, reliably.
-

From Smoke Stacks to Smartscapes: Evolving Industrial Operations in the Digital Age
Smoke Stacks to Smartscapes. Past, Present, Future, the evolution in-place of the industrial control system, and the airgrap that once protected it.
-
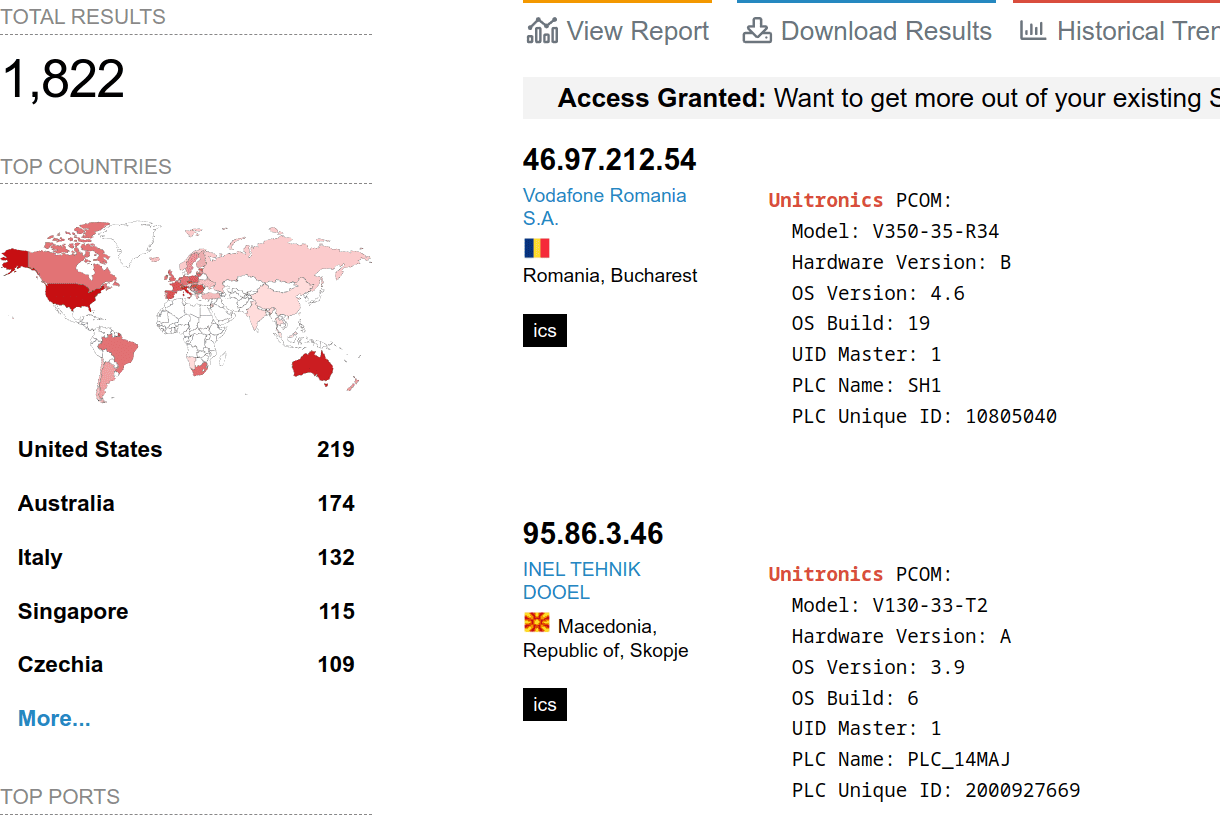
Avoid Exploitation of Unitronics PLCs used in Public Water Systems
Exploitation of Unitronics PLCs used in Public Water Systems for political purposes. Recommendations.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-

EPA Cybersecurity Recommendations: Unpacking the Impact on Public Water Systems
This article will help you understand the new EPA cybersecurity recommendations, why they matter for public water systems, and the recommended solution.
-

Protecting Against the OWASP Top 10 Web Application Vulnerabilities
The OWASP Top 10 is a standard awareness document that outlines the most critical web application security risks and vulnerabilities. Learn how Agilicus AnyX is designed to eliminate an attacker’s visibility into the potential OWASP Top 10 web application vulnerabilities.
-
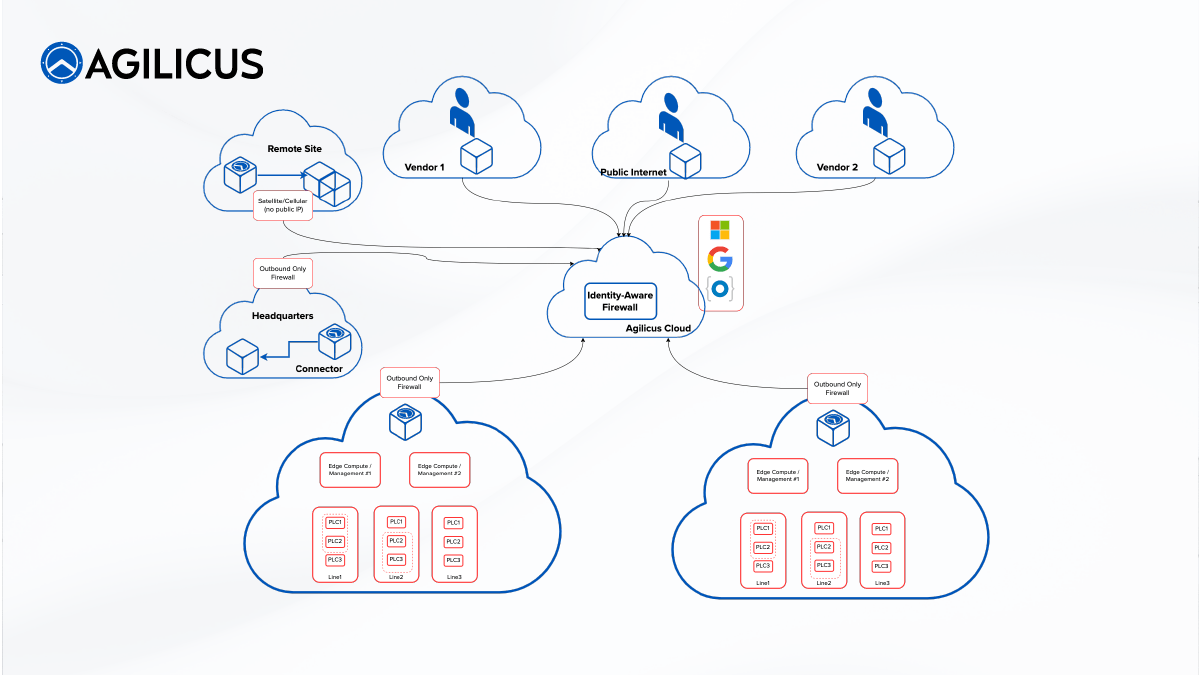
Agilicus and Operational Technology
Zero Trust Network Architecture can effectively meet the growing demand for enhanced cyber security in industrial and operational technology.
-

Industrial Air Gap – A Tale Of 2 Users
Industrial devices are hard to secure. Commonly done only via direct local access. Teams, however, wish remote access to improve efficiency. A solution to this battle is Zero Trust.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-
NIST sp 800-63B: How Well Do I Know You?
Zero-Trust Network Architecture has 3 steps: Authenticate (Who), Authorise(What), Access(How). 3 Levels of strength of the who are defined in NIST sp 800-63B. Does the goldilocks principle apply to you? Read on!
-

Agilicus AnyX versus Cloudflare Zero Trust
Compare mesh overlay VPN network technology Cloudflare Zero Trust to Agilicus AnyX. Agilicus AnyX versus Cloudflare Zero Trust
-

Agilicus AnyX versus Tosibox
Compare mesh overlay VPN technology Tosibox with Agilicus AnyX Zero Trust
-

Agilicus AnyX versus Nebula
Compare mesh overlay VPN network technology Nebula to Agilicus AnyX Zero Trust
-
Agilicus AnyX versus FortiSRA
Agilicus AnyX contrasted with Fortinet FortiSRA
-
Agilicus AnyX versus Splashtop
Agilicus AnyX versus TeamViewer. Compare a Zero Trust Network Access system with full authentication, authorisation, versus a niche solution.
-

Agilicus AnyX versus TeamViewer
Agilicus AnyX versus TeamViewer. Compare a Zero Trust Network Access system with full authentication, authorisation, versus a niche solution.
-

Zero Trust VTScada Twilio Alerts
Zero Trust VTScada Twilio Alerts. Monitor your VTScada system with Twilio. Without exposing its login to the Internet. Simple, secure, no config change.
-

Zero Trust VNC Remote Desktop
1-click VNC remote desktop, single-sign-on, multifactor authentication. Zero Trust VNC Remote Desktop provides high-convenience with high security.
-

Managed Industrial Remote Access
Managed Industrial Remote Access Case Study: Customer Objections and Responses
-

Midland Texas Transforms Water Purification Cyber Security
The City of Midland, Texas chose Agilicus AnyX Zero Trust to secure its Water Purification plant
-

ACME Manufacturing Transforms Security and Efficiency with Agilicus AnyX
ACME manufacturing chose Agilicus AnyX to enable SAP access to a multi-division, contract-manufacturing environment. Safely, Securely, Simply.
-
Wastewater Zero Trust Remote Operations and Asset Management
Wastewater Zero Trust Remote Operations and Asset Management. Learn how this industrial control systems engineering company expanded their service offering with Agilicus AnyX.
-

How the Town of Mono Future-Proofed its Cybersecurity Infrastructure and Transformed Municipal Operations
The Town of Mono future-proofed its cyber security infrastructure and exceeded compliance requirement by transitioning to Zero Trust.
-

Starlink Remote Cameras: 3-Steps to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable Starlink Remote Camera inbound remote access, despite CGNAT. Access your security video from anywhere.
-

Starlink and Synology NAS: How to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable inbound remote access to your Starlink and Synology NAS setup, despite CGNAT. Access your files from anywhere.
-

Case Study: Apple Screen Sharing, Zero Trust, Multi Factor Authentication
Remote Apple Screen Sharing with Zero Trust, Single-Sign-On, Multi-Factor Authentication. Without a VPN.
-

How the City of Kenosha Transitioned to Zero Trust
How the City of Kenosha Transitioned to Zero Trust using Agilicus Zero Trust to achieve EPA compliance and gain multi-factor authentication, vendor security, audit trails, and network visibility.
-

Case study: Protecting Critical Municipal Infrastructure and Securing Operational Technology at a Water Treatment Facility
Protect a municipal SCADA water treatment facility. Provide multi-factor authentication, secure remote access to staff and partners with single-sign-on.
-

Secure Remote Connectivity to 100 Critical Infrastructure Sites, Nationwide
A major systems integrator that services critical infrastructure across the United States seamlessly transformed their service model through Zero Trust, to reduce costs while enabling secure remote connectivity to over 100 customer sites. Learn how Agilicus AnyX was used to simplify access while ensuring the systems integrator could adhere to each customers expectations on security.
-

Add Multi-Factor Authentication to Legacy Systems with Agilicus AnyX
A municipality was seeking a method for securing access to the SCADA systems through the implementation of Multi-Factor Authentication.
-

Third Party and Vendor Access Management for Critical Infrastructure
Adopting Vendor Access Management and enforcing multi-factor authentication for access to municipal critical infrastructure.
-

Enabling Secure Access to Web Applications through Zero Trust
Learn how Agilicus helped a Canadian Municipality extend secure access to web applications for mobile workers through a zero trust framework.
-

Case Study: Secure Access to Critical Infrastructure for Partners and Vendors
Critical Infrastructure for Partners and Vendors. A Municipality modernised a water treatment facility to enable secure connectivity for various internal teams (IT, Public Works), partner organisation, and their systems integrator.
-

Case Study: A VPN Alternative for Securing Remote Access to Legacy Applications
A municipality in Southern Ontario was seeking a method of securing remote access to legacy applications – responsible for the treasury, billing, and permit functions.
-

Legacy Life-Extend: More Users, More Secure, No Changes
Legacy municipal support systems are difficult to make widely available without compromising security. Learn how to solve.
-

Cyber Alerts, Best Practices: Put Advice To Action
Government agencies are publishing cyber advice. Each notice is individually full of good facts and advice, but collectively, they are creating indecision: what do I do first? when? how? With what budget? Today we will talk about how to interpret, how to implement, economically, without disruption.
-

A VPN Alternative for Local Governments
The VPN, a powerful tool, is not appropriate for all users. Learn how we can connect the digitally disenfranchised. Single Sign-on for all, multi-factor on everything.
-

A VPN Alternative for Manufacturing
The VPN, a powerful tool, is not appropriate for all manufacturing users. Learn how we can connect the people who need it.
-

Cybersecurity on a Budget, Secure and Simple
Whether it’s remote operations and support, on site staff, or routine maintenance – ensuring your industrial water systems have proper access controls without causing a strain on your budget is crucial.
-

Add Remote Support, Leverage Your Specialists
Add Remote Support, Leverage Your Specialists Fix Remote Access, Improve Efficiency Sending your staff to customer sites costs valuable time and resources. Your automation and support specialists are unable to help on other projects from across the country, while their services might only be needed for a couple hours daily. Enabling remote setup, troubleshooting, and […]
-

Simplify Remote Access, Secure Industrial Equipment
No VPN, No Shadow IT Like TeamViewer. Simplify and Secure remote manufacturing industrial access for multiple divisions, contract manufacturers, vendors
-

Nation State Attacks on Critical Infrastructure – Assess, Understand, Protect
Nation State Attacks on Critical Infrastructure – Assess, Understand, Protect Putting a cellular router on SCADA, PLCs, or HMIs considerably improves your efficiency and allows you to remotely access these interfaces – it also considerably increases your risk. Systems become scannable and easily accessed by anyone who stumbles across them. It is easier than ever […]
-

Nation State Attacks on Water – Assess, Understand, Protect
See how an attacker gains access to information of public water systems. We will use tools like Shodan and nmap to detect and assess common vulnerabilities within industrial water systems.
-

VPN Alternative: Decrease Risk, Increase Simplicity
VPN Alternative: Decrease Risk, Increase Simplicity Local Governments have many different systems to safeguard and manage. These can include industrial control systems such as SCADA, HMIs in water treatment facilities, ERP systems running payroll, and bylaw enforcement mobile applications, to name a few. Users may not be able to install your VPN software on their […]
-

Remote Operations: VPN Alternatives to Improve Simplicity and Security
The VPN, a powerful tool, is not appropriate for all users. Learn how Agilicus can connect the people who need it.
-

VPN Alternatives for Manufacturing
Learn how Agilicus connects the people who need it with a VPN Alternative for manufacturing. Single Sign On for all, regardless of partner or employee. Multi-factor where needed, even on legacy applications.
-

VPN Alternatives for Water and Critical Infrastructure
VPN Alternatives for Water: Emergency directives regarding VPNs serve as a wake up call for a rethink.
-

VPN Alternative for Local Governments
3 recent emergency directives on VPNs? A VPN is a security risk in local government networks. Examine Zero Trust VPN Alternative for Local Governments
-

Securing Wastewater Remote Connectivity with Segmentation and Zero Trust
The modern wastewater plant is now a blend of data centers and pipes. Learn about the complex challenges of allowing remote connectivity to systems in a wastewater treatment facility
-

Solve Vendor Multi-Factor and Single Sign-On for Industrial Support
Learn how you can securely enable vendor remote access to industrial control systems with multi-factor authentication, least privilege access, and single sign-on.
-

Add Wastewater Remote Operations, Expand Revenue
Learn how wastewater remote operations is unlocking new, more profitable and predictable revenue streams by adding pre-defined remote operations services to their portfolio.
-
Fortifying Manufacturing Systems: A Foolproof Framework for Secure Remote Access
Fortifying Manufacturing Systems. Enable secure remote access for any user (with any company) who requires access to systems on the manufacturing floor.
-

Secure Access for Water: Unlock Application-Only Remote Desktop Access Anytime, Anywhere
Secure Access for Water: Unlock Application-Only Remote Desktop Access Anytime, Anywhere Learn how to get the most out of your RDP apps and workflows with Agilicus AnyX. Discover how to streamline access while limiting access to the right people at the right time. Watch The Recording Webinar Highlights Remote Desktop Protocol (RDP) is a business-critical […]
-

VPN Alternative for Local Governments: Why and How
A VPN is a security risk in local government networks. Examine Zero Trust alternatives.
-
How to Connect to an HMI without a VPN
Connect to an HMI without a VPN. Extend secure access to employees and vendors.
-

A Modern Air Gap for Operational Technology
Learn how creating a modern air gap increases your security posture drastically compared to legacy solutions like the VPN and TeamViewer.
-
A Modern Air Gap for Operational Technology
Learn how creating a modern air gap increases your security posture drastically compared to legacy solutions like the VPN.
-

Strengthening the Security Structure of a Water Treatment Facility
Join us online on February 9 and learn how a modern security structure can be strengthened in a water treatment facility.
-
Secure Remote Access for Water: Sharing Multiple Dashboards Over VNC
Learn how to get the most out of your VNC apps and workflows with Agilicus AnyX. Discover how to streamline access while limiting it to the right people at the right time.
-

Municipal Cybersecurity Success Stories from Across Canada
Two Canadian Municipalities share their experience deploying Zero Trust with Agilicus AnyX to increase their Cyber Security.
-

The City of Kenosha’s Zero Trust Cybersecurity Transformation
Discover how the City of Kenosha seamlessly pivoted towards a resilient, Zero Trust environment. Embrace a non-VPN paradigm to safeguard your local government.
-

Securing Access to Industrial Control Systems with Zero Trust
Learn how to modernize the manufacturing floor with secure, remote access to Industrial Control System without a VPN or new hardware.
-

Keeping Manufacturing Lines Safe and Efficient: The Power of Least Privilege Access
Keeping Manufacturing Lines Safe and Efficient: The Power of Least Privilege Access. Discover how the principle of least privilege access can ensure your manufacturing systems are safe and running smoothly.
-
Simple, Seamless, Secure: A New Era of Vendor Access for Manufacturing
Join us to learn how organizations are mastering vendor access management to reduce cyber risk without complicated workarounds or disruptive implementations.
-

SSH via Zero Trust. No public IP needed.
Use Zero Trust networking to provide access with no public IP, no inbound firewall changes, and, remain end-to-end encrypted.
-
Authentication and the API Key
We all think about authentication as a user signing-in. But what about, once signed in, the ‘create api key’ that is a permanent password? Where does that go? Zapier? Script in home dir?
-
Simple 3-Step Program To Reduce The Risk Of Ransomware
Simple 3-Step Program To Reduce The Risk Of Ransomware