The US National Security Agency (NSA) published a document giving guidance on how (and why) to adopt a Zero Trust Security Model. The TL;DR is: NSA recommends embracing Zero Trust for all critical systems.
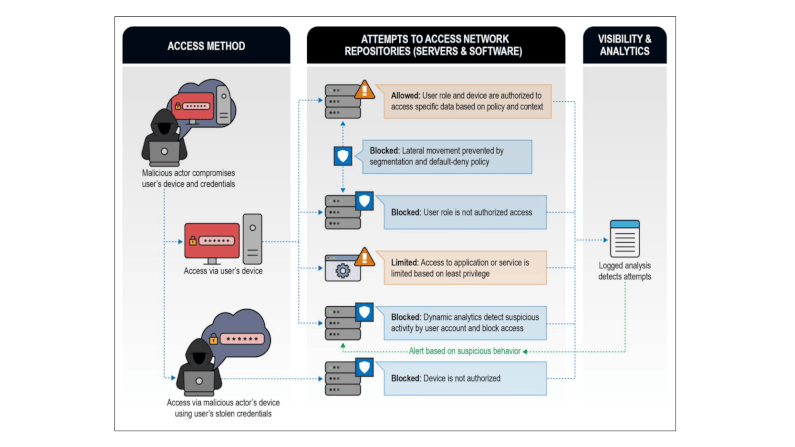
Their rationale is “Defense In Depth“: assume a breach is inevitable or has already occurred. So constantly limit access to only what is currently needed with granular access-controls. As the systems evolve and interconnect more often, at more points, across more boundaries, perimeter-based security (your VPN and single firewall) become more challenging to implement while also becoming less effective. They actual increase risk by causing a false-sense of security and reducing the time available to address real threats. Embracing zero trust means focusing on what will occur, and how to deal with it, rather than denying it can occur.
In the NSA document, they define Embracing Zero Trust (in turn from the NIST 800-207) as:
Zero Trust is a security model, a set of system design principles, and a coordinated cybersecurity and system management strategy based on an acknowledgement that threats exist both inside and outside traditional network boundaries. Zero Trust repeatedly questions the premise that users, devices, and network components should be implicitly trusted based on their location within the network. Zero Trust embeds comprehensive security monitoring; granular, dynamic, and risk-based access controls; and system security automation in a coordinated manner throughout all aspects of the infrastructure in order to focus specifically on protecting critical assets (data) in real-time within a
https://media.defense.gov/2021/Feb/25/2002588479/-1/-1/0/CSI_EMBRACING_ZT_SECURITY_MODEL_UOO115131-21.PDF
dynamic threat environment. This data-centric security model allows the concept of least privileged access to be applied for every access decision, where the answers to the questions of who, what, when, where, and how are critical for appropriately allowing or denying access to resources
https://csrc.nist.gov/publications/detail/sp/800-207/final
The key success factors for embracing zero trust listed are:
- coordinated system monitoring (e.g. single identity source, single authorisation model)
- Assume all requests from network may be malicious (fine-grained per request authorisation and audit)
- Assume all devices and infrastructure may be compromised (control the east-west as much as the north-south paths)
- Assume the supply chain is compromised (so the threat can start from inside, rather than originate outside)
You can read more about Zero Trust, how it can simplify your security, economically.