Agilicus AnyX Frequently Asked Questions
AnyX – Initial Setup
Agilicus AnyX requires modern cryptography with a strong chain of trust. This is achieved using Let’s Encrypt.
Some older Microsoft Windows systems are not updated to have the proper cryptographic trust information installed. You should upgrade your Windows installation, but, if this is not possible, you can manually install the certificates.
First, download the .der file from https://letsencrypt.org/certificates for each of ‘X1 & X2‘.
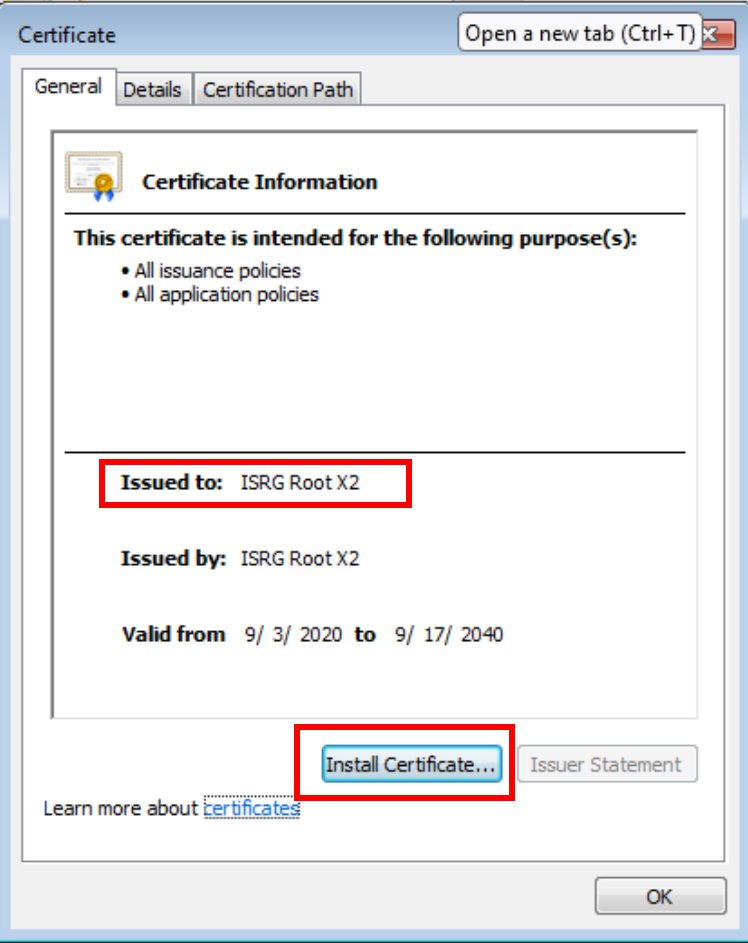
For the X1 der and X2 der, open these on your desktop. You will be prompted to open the certificate manager. From here, Install, and pick the “Trusted Root Certification Authorities”.
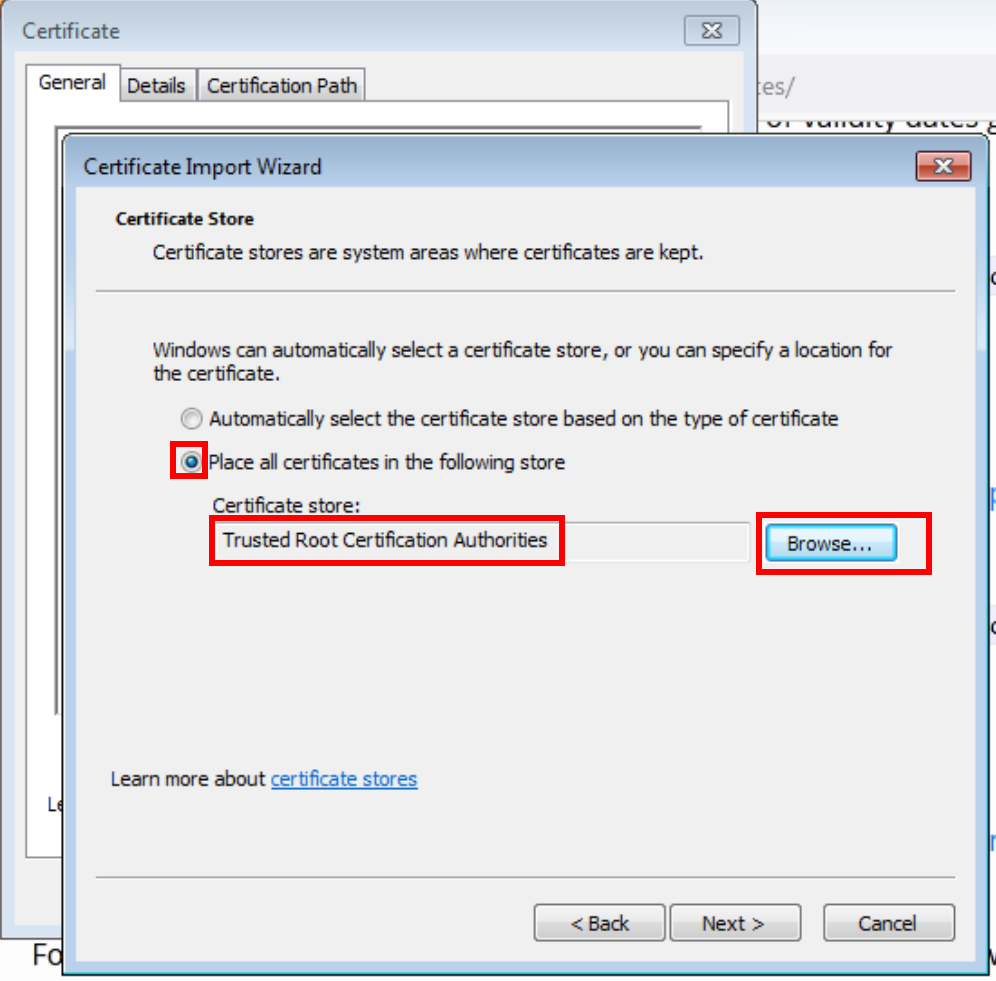
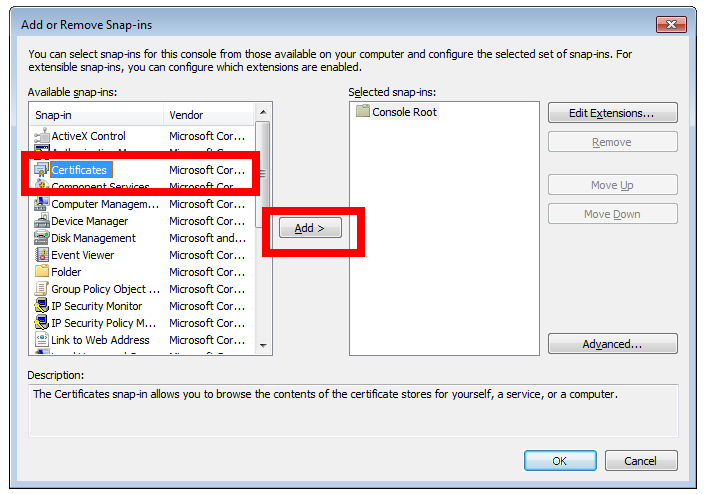
Now we must import these to the Machine trust as well (above we did your user). To do so, open ‘mmc’
Now press ‘Control-M’.
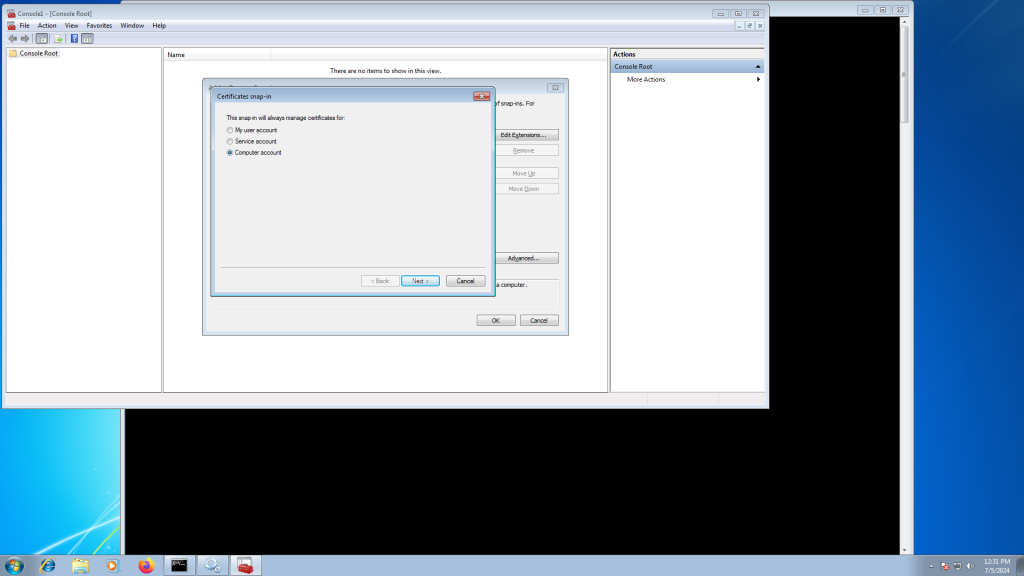
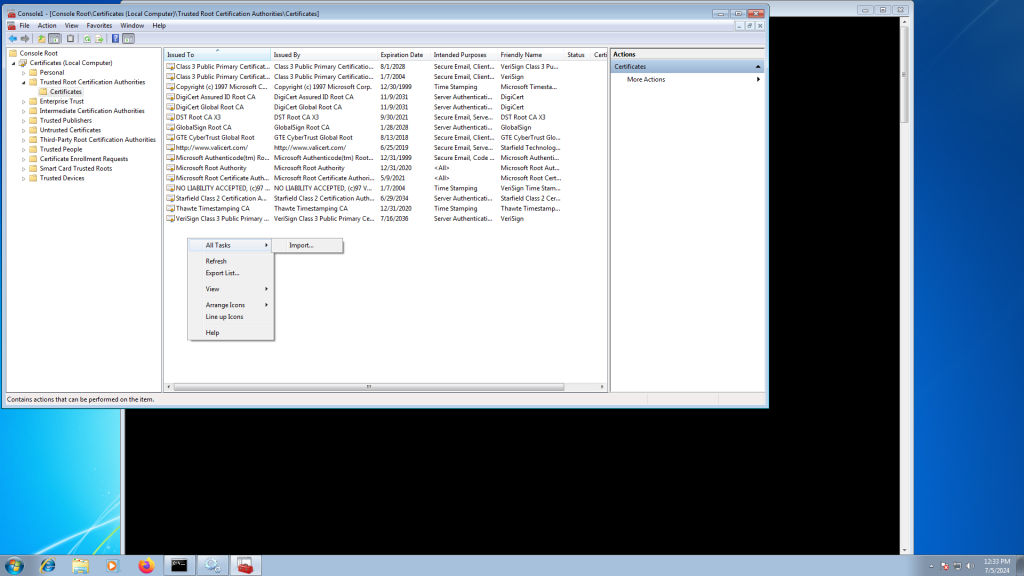
Select the X1 (and repeat for X2) certificate from earlier.
At this stage you should be able to install the Agilicus Connector.
Some customers have issues with their outbound or next-generation firewall. It might block their new domain name they use with Agilicus AnyX (e.g. connect.mydomain.com). We recommend configuring your firewall by hostname if possible. If it must be by IP, this could theoretically change in the future.
See “Firewall Configuration” for the specific rules.
Authentication, User Permissions
If you have a user who has signed in with one identity provider (e.g. Google) and you wish to change them to another (e.g. Microsoft Azure), or, the user’s email has been changed, use the ‘Update User Identity’ feature. This will disconnect the user from their existing identity provider, and, on their first new sign in, they will be adopted by the new one. Once you have selected thhis option you may change the user’s Email or switch them to a different identity provider.
On the “Access/Resource Permissions” menu in your administrative web interface you can control which users or groups have which permissions on a resource. See “Permissions” for more information.
By default you will have a ‘Shared’ Microsoft Identity Provider enabled. This allows anyone to sign in with any Microsoft account: Azure, Office 365, Outlook.com, etc. This is useful for 3rd parties, vendors, etc.
If you wish to force your users to sign in with your own Azure tenant (e.g. to enable auto-create), you may create a ‘Custom Authentication Issuer’.
You may use Time-Based One-Time Codes (TOTP) (e.g. Google Authenticator, Microsoft Authenticator, Authy, etc), or, any of the standards from the WebAuthn standard set (e.g. USB-based like YubiKey, Passkeys, TPM-based, biometric, etc).
Agilicus AnyX joins together (federates) a set of Identity Providers (IdP). As an end user, you will see this as e.g. ‘Sign In With Google’ or ‘Sign In With Microsoft’. The AnyX platform in turn presents these federated IdP as a new IdP. The Upstream Identity Provider is it original one that the user interacts with (e.g. Microsoft, Google, Active Directory Federation Services, etc).
Connector Diagnostics
The Agilicus Connector supports running in an Active/Active mode, with up to four instances running at a time.
Note that if the Connector exposes a Share, then it cannot run in Active/Active mode. Instead, consider an approach like a Agilicus Connector Windows Cluster.
Yes. First, you need to enable connector logging in Organisation -> Audit Destinations by clicking the Access and Authorization check-boxes. Your connectors will shortly start streaming their logs to Agilicus. You can see the logs in Applications->Diagnose. Fill in the time range you are interested in, then click View Logs. Note that you may see other logs related to your Organisation here. The relevant ones will have source_type equal to agent-connector
No it does not. However, given that it will use TCP/IP to connect to them, it needs to be able to route to the IP it determines for the network, and any firewalls in between must allow access to that IP and the target TCP port.
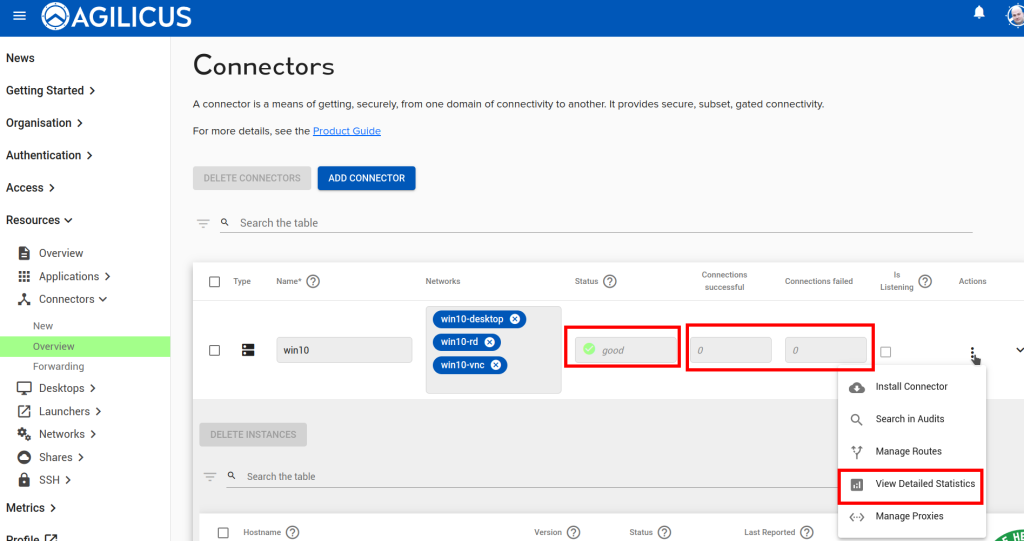
Go to the Connector->Overview screen. Each connector reports an overview status here. “Good” means all instances of the connector are running, and that they are fully connected to Agilicus.
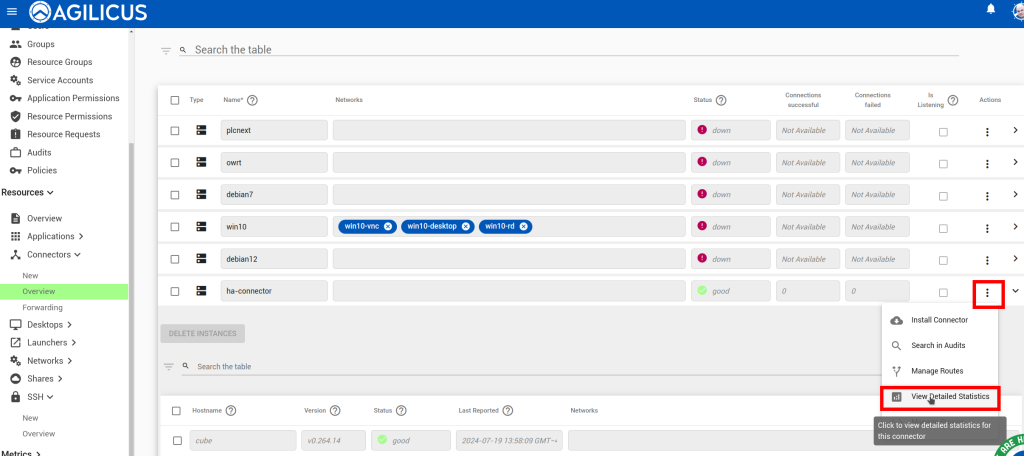
Go to the Connector->Overview screen. Your connectors will shortly begin to publish statistics. You can see a summary
of successful/failed connections in the overview table. Click Actions -> View Detailed Statistics for a breakdown of these stats.
Check that the connector itself is up (the ‘Good’/green in below). After you open the detailed statistics screen, reproduce the problem, and look at which counters increment.
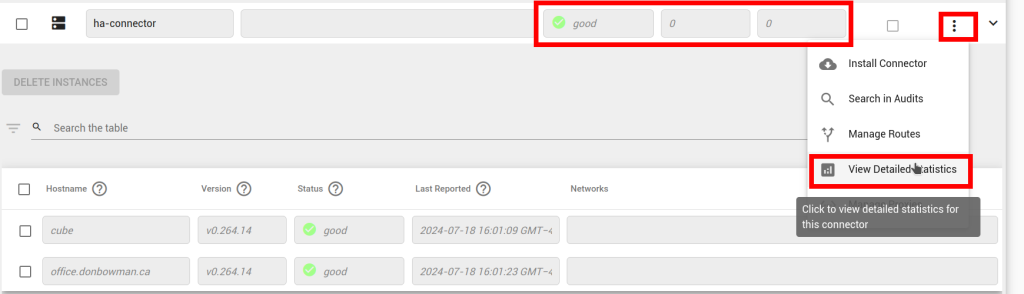
As part of maintaining its connection to Agilicus, the connector reports some system information. In the Connector->Overview screen, click on the connector in which you are interested. The resulting expanded table shows each instance of the connector and the hostname of the machine on which it is running.
When establishing a connection to a Network, the connector first determines an IP with which to communicate with. If an Override IP is present in the Network’s configuration, it will use that. Otherwise, it will use the local system’s DNS configuration to do a DNS lookup of the network’s Hostname. It then establishes a connection to that IP using the local system’s standard TCP/IP stack.
You may have a local firewall which is blocking outbound communication. See ‘Firewall Configuration‘. Check the connector logs (on Windows, using EventViewer, on Linux typically with journalctl -fu agilicus-agent)
Your Network for the HTTP server may be incorrectly configured. The connector proxies HTTP requests at the application layer. If the HTTP server runs HTTPS/TLS, the Network must be configured to initiate an HTTPS/TLS connection, and it must trust the certificate presented by the server. Conversely, if the HTTP server is plaintext (unencrypted), but the connector is configured to expect TLS, it will fail to establish the connection.
The end-user receives this message on sign-in:
Message: upstream connection failed
Action: The upstream host could be downThis indicates the Agilicus Connector is up, and the user was able to sign in correctly, however, the customer-supplied application is either down, or unreachable from the Agilicus Connector.
A common issue is a change in IP/port of the application, you may change this as below.
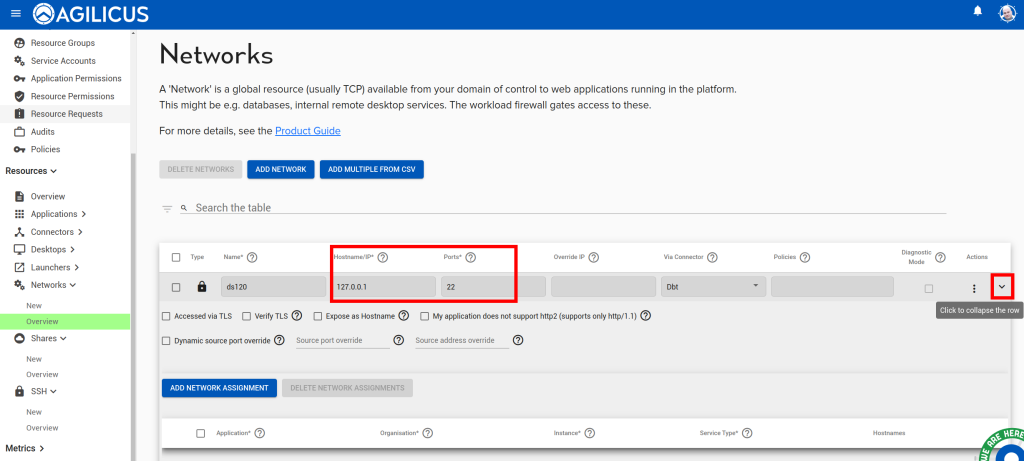
To diagnose the issue, use the detailed stats from the connector overview page:
Connector Installation
Microsoft has discontinued support for Windows 7 and Windows 2012. The Agilicus connector continues to run on these machines, however, it is important to have KB2533623 installed.
If the Windows 7 machine is missing KB2533623, the connector may fail to start. The update can be manually installed from:
https://web.archive.org/web/20200412130407/https://www.microsoft.com/en-us/download/details.aspx?id=26764
Note: it is possible a superceding KB might be installed, e.g. KB3063858 or KB4457144 or KB3063858.
Agilicus AnyX requires modern cryptography with a strong chain of trust. This is achieved using Let’s Encrypt.
Some older Microsoft Windows systems are not updated to have the proper cryptographic trust information installed. You should upgrade your Windows installation, but, if this is not possible, you can manually install the certificates.
First, download the .der file from https://letsencrypt.org/certificates for each of ‘X1 & X2‘.
For the X1 der and X2 der, open these on your desktop. You will be prompted to open the certificate manager. From here, Install, and pick the “Trusted Root Certification Authorities”.


Now we must import these to the Machine trust as well (above we did your user). To do so, open ‘mmc’

Now press ‘Control-M’.





Select the X1 (and repeat for X2) certificate from earlier.
At this stage you should be able to install the Agilicus Connector.
The connector status can be found by checking the systemctl service status:
$ sudo systemctl status agilicus-agent
The Agilicus Connector runs as a Windows Service. Open the Windows ‘Services’ app and look for ‘Agilicus Connector’. The ‘Service Status’ will show the current status.
Accurate globally synced time is critical to the proper operation of many modern cryptographic tools. It affects certificte allocation/revocation, sign-in audit logs, etc. See https://www.agilicus.com/product-guide/time-synchronisation/ for further details to ensure the local machine time synchronization is setup.
Connector logs on Windows can be found in the Windows Event Viewer. Inside Event Viewer (Local) -> Windows Logs -> Application, See “Agilicus Connector – Microsoft Windows“.
The Agilicus Connector needs to be able to reach any service it is used to expose. For a share, this means running on a machine with access to the files. For a Desktop, it means being able to reach via TCP (port 3389 or port 5900 for RDP or VNC typically) the destination system. This might mean running on the same system, this might mean running on a device on the same network segment or inside the same firewall.
Connectors
Microsoft has discontinued support for Windows 7 and Windows 2012. The Agilicus connector continues to run on these machines, however, it is important to have KB2533623 installed.
If the Windows 7 machine is missing KB2533623, the connector may fail to start. The update can be manually installed from:
https://web.archive.org/web/20200412130407/https://www.microsoft.com/en-us/download/details.aspx?id=26764
Note: it is possible a superceding KB might be installed, e.g. KB3063858 or KB4457144 or KB3063858.
General Diagnostics
End users interact with AnyX via Profile (at https://profile.MYDOMAIN). Each resource is represented by an icon. There are 3 ‘tabs’ (mine, requested, all). If an icon does not show in the ‘mine’ tab, but does show in ‘all’, the user is missing permission. If the icon does not show at all, try refreshing the browser.
Invoices, Billing
See “Organisation/Billing” in your admin portal (https://admin.MYDOMAIN). From here, select ‘VIEW/UPDATE PAYMENT INFORMATION”
See “Organisation/Billing” in your admin portal (https://admin.MYDOMAIN). From here, select ‘VIEW/UPDATE PAYMENT INFORMATION”
See “Organisation/Billing” in your admin portal (https://admin.MYDOMAIN). From here, select ‘VIEW/UPDATE PAYMENT INFORMATION”
Key Concepts
When you initially signed up to the Agilicus AnyX platform, you choose a domain (either your own DNS name with a CNAME, or, an Agilicus-supplied domain). Your domain looks something like ORGNAME.agilicus.cloud. You will have received a welcome email with this information, as well as have been automatically signed-in in your browser to e.g. https://admin.ORGNAME.YOURDOMAIN.
Resource – Desktops
TightVNC via command line allows specifying the specific display adapter number.
TIghtVNC also allows display offsets in the ‘Extra Ports’ configuration. By specifying a specific port (eg. 5091), a display offset can be configured for a monitor. Once the port is configured and known, a new desktop can be configured in the Agilicus Admin portal with the port number.
Resource – Web Applications
If you have an application hosted on a Subfolder/path in your Web Server
You may have an application hosted under a subfolder/path on your web server, possibly because it is better than having another server for it. For example: localhost:port/subpath, localhost:port/support etc.
To enable the subpath hosting for your application,
1. Go to Resources > Applications > Define and select the application from the drop down at the top of the page
2. Then in Security (tab) > Firewall Rules > HTTP Rules, change the / entry under path to your custom subpath (For example, /subpath)
3. Under Proxy (tab) > HTTP Rewrites, inside the Common Path Prefix field, enter your custom subpath again (For example, /subpath)
Web Applications use network resources. You can change where the network resource is accessed (either the connector it is bound to, or the hostname/IP/port that it is internally known as) by navigating to Networks/Overview.
The specific resource(s) will be named similarly to the web application, with -local-service appended.
Starlink
No, Apple does not provide a server platform since the XServe. The connector is supported on Linux, Windows, various embedded platforms like Synology, pfSense, Mikrotik, etc. To run the connector on an Apple Mac, you may use the Docker instructions (see Install Docker Desktop on Mac).
If you are an enthusiast, consider running the connector under Docker on your Mac.
No. The Agilicus AnyX is a SaaS solution, cloud based. In order to work with your Starlink network, you will install a small piece of software on a single device you already own.
Yes, the end user can use the web-based profile as well as the desktop based launcher. The desktop-based launcher requires OSX 11 (last supported version by Apple) or later.
You can see an animated diagram on the Agilicus Connector page. But in general, this works the same way e.g. a Google Nest thermostat works. Something inside your home network makes a persistent outbound connection to our cloud. When you are away, you will connect to our cloud, it will confirm your identity, and bridge you across these two outbound connections.
Agilicus AnyX is an implementation of Zero Trust, a security best practice. You will use single-sign-on authentication via your Google or Microsoft account (there are no passwords). You can optionally enable multi-factor authentication. All traffic is encrypted with TLS 1.3 HTTPS. You can configure firewall rules in this system for e.g. geo-ip based access, as well as other more complex rules. You will have a full audit trail of who used what when.
Agilicus AnyX is an excellent solution for web applications, for SSH (e.g. command line access), for a Share (e.g. file access), and for remote desktop (Microsoft Remote Desktop, VNC). If you have complex networking needs that require layer-3 routing this is probably not the right solution for you.
The Agilicus Connector supports many device types. Windows, Linux, OpenWRT, Synology. You can see more information on the product guide page. In general, the machine will need about 100MB of storage, 20MB of ram to operate.
It is very unlikely the Agilicus Connector will install on your camera.
We do not recommend using the RTSP feature of your camera with Agilicus AnyX. Instead we recommend using the HTTP interface.
Many security cameras have a web interface. If you have a URL you can use from your browser at home, then you can use it while away with Agilicus AnyX.
In most cases, if you have an NVR, this will work. If your camera supports ONVIF, we have specific support for some NVR with that.
Many people use Synology Surveillance Station or Shinobi NVR with Agilicus AnyX.
Sample setups for generic ONVIF cameras are here.
A sample setup for an older Hikvision is here.