Firewall Configuration
SIGNUP
During the new organisation Signup flow you may find an error as below. This is caused by a corporate network filter (e.g. Palo Alto) which blocks certain encrypted flows.
Overview
During the new organisation Signup flow you may find an error as below. This is caused by a corporate network filter (e.g. Palo Alto) which blocks certain encrypted flows.
You may have firewalls in two locations: between your browser and the Internet (e.g. if you run endpoint protection software, or are using a device not currently on your corporate network), and, between the Agilicus Connector and the Internet.
Firewall Configuration: End-User Browser to Internet
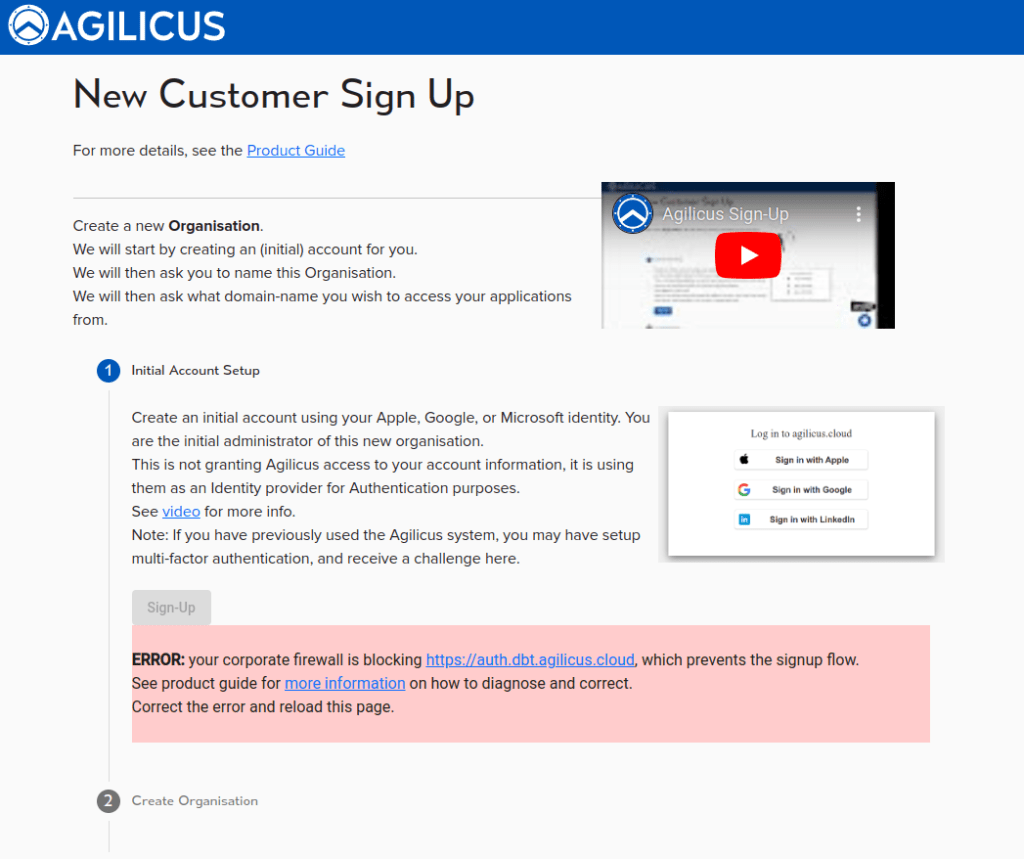
In order to use your browser with the Agilicus AnyX platform, whether for signup purposes, or for ongoing usage, you need to be able to navigate to these host names:
- https://admin.agilicus.cloud (signup only)
- https://auth.agilicus.cloud (signup only)
- https://api.agilicus.com/
- *.YOURDOMAIN (each of yoru resources will appear hre)
(where YOURDOMAIN is the domain name you will choose during the signup process).. You will know you need these rules if you see errors like below image.
In addition, your name server (DNS) must be able to resolve:
- ca-1.agilicus.ca
- api.agilicus.com
- www.agilicus.com
The most common problem observed is that if you navigate to https://auth.agilicus.cloud you get an error implying the connection was RESET. This is typically done by a content-filtering firewall such as Palo Alto blocking “auth.*” as a domain name.
To resolve, work with your outbound firewall filtering vendor to allow:
- *.agilicus.com
- *.agilicus.ca
- *.agilicus.cloud
Firewall configuraton: Agilicus Connector to Internet
The Agilicus Connector makes outbound connections only, on port 443 HTTPS only. It will have 2 outbound TCP connections (for resilience) as well as periodic ones to its API and update server.
Configure your outbound firewall to allow:
- www.agilicus.com (upgrades)
- api.agilicus.com (configuration)
- agent-server.ca-1.agilicus.ca
- *.YOURDOMAIN (authentication via auth.YOURDOMAIN)
If you prefer to use IP (and port) – based rules, you may use as below. Note: it is possible this list will change in the future.
- 34.95.12.47 (www.agilicus.com)
- 35.203.36.11 (api.agilicus.com)