KEY RESOURCES
Adopting Zero Trust with Agilicus AnyX
Learn how organisations are using Agilicus AnyX to adopt Zero Trust. Read more about industry best practices with our white papers, and learn why the platform stands out when it comes to enhancing security with our brochures.
Resources
Leveraging Agilicus AnyX to adopt an enterprise-grade, Zero Trust Architecture to enhance security and resolve access challenges. Learn more, read the case studies, brochures, white papers, and articles.
-

The Fragility of Interdependence: Securing the Hyper-Specialised Supply Chain in the Age of Cyber-Physical Convergence
The £1.9bn JLR breach exposed supply chain fragility. Download the Agilicus whitepaper to learn how Zero Trust secures the industrial mesh against cyber threats.
-
Multi-Site Manufacturing
The transition to multi-site manufacturing and industry 4.0 requires a remote access solution that delivers seamless, identity-based access for every site and contractor.
-
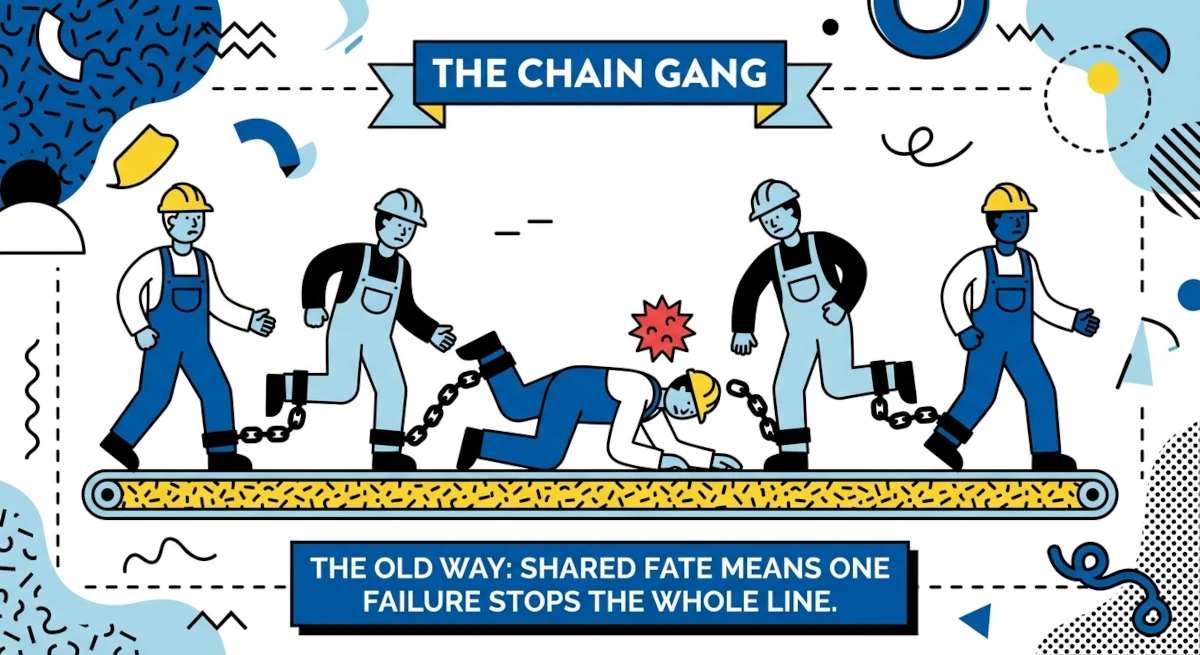
The Frictionless Factory: Solving the Connectivity Crisis in Hyper-Specialised
Is your VPN architecture killing your Mean Time To Repair? In the era of the hyper-specialized supply chain, legacy VPNs create operational drag and dangerous “Shared Fate” risks—as proven by the massive Fall 2025 Jaguar Land Rover outage. This whitepaper explains why modern manufacturers are abandoning Layer-3 VPNs for Agilicus AnyX. Discover how the “Island Architecture” delivers instant, clientless access to third-party experts, ensuring your production line stays up even when your supplier goes down. Read the full whitepaper to…
-

Agilicus AnyX Brochure
Agilicus AnyX is the only purpose-built product to solve the industry challenges of enabling any user (staff, partner, vendor) to safely, securely, simply remotely operate operational technology, without re-architecting the underlying SCADA networks.
-

Northern Rockies Regional Municipality
How Northern Rockies Regional Municipality Transitioned to a Zero-Trust Enabled Work From Anywhere Environment with Agilicus AnyX
-
Agilicus AnyX versus Cloudflare Zero Trust
A direct comparison between Agilicus AnyX and Cloudflare Zero Trust. This article evaluates the fundamental differences between Agilicus’s simple, integration-focused platform and Cloudflare’s complex, DNS-based SASE approach. Key features examined include client-less access, one-click identity integration, and support for legacy and industrial protocols without requiring network changes.
-

Managed Industrial Remote Access
Discover how Water Control Automation successfully deployed a managed industrial remote access solution using Agilicus AnyX. This case study explores the complex access requirements of diverse stakeholders—including equipment manufacturers, system integrators, and remote operators—and details how a Zero Trust framework met stringent security and operational demands. Key challenges addressed include enabling secure single sign-on, ensuring comprehensive audit trails, and eliminating the need for traditional VPNs.
-

Agilicus AnyX Configuration Security
Cloud Configuration: What is the exposure? How is it protected? Learn how Agilicus AnyX is more secure than an on-premise system.
-
Agilicus AnyX versus Tosibox
A detailed comparison between Agilicus AnyX and Tosibox for securing operational technology (OT) environments. This article contrasts the Zero Trust, application-aware proxy architecture of Agilicus AnyX with Tosibox’s orchestrated overlay VPN. Key differentiators examined include user-based authentication, single sign-on, browser-only access, and fine-grained authorization, highlighting the differences between a modern Zero Trust solution and a traditional VPN approach.
-

Agilicus AnyX versus Nebula
A comparative analysis of Agilicus AnyX and Nebula for secure remote access, with a focus on Operational Technology environments. This article contrasts Agilicus’s comprehensive Zero Trust architecture with Nebula’s overlay VPN mesh system. Key differences explored include the ability to connect to devices without client software, application-layer protocol awareness, and the capacity for detailed, per-user audit records.
-
Agilicus AnyX versus FortiSRA
A feature-by-feature comparison of Agilicus AnyX and Fortinet’s FortiSRA for securing Operational Technology (OT) environments. This article contrasts the complete Zero Trust architecture of Agilicus AnyX with FortiSRA’s approach, highlighting differences in agentless deployment, included high-availability, native identity integration for single sign-on, and support for legacy applications and embedded devices.
-

Midland Texas Transforms Water Purification Cyber Security
The City of Midland, Texas chose Agilicus AnyX Zero Trust to secure its Water Purification plant
-

Understanding Cyber Security Risk
Risk management is not about achieving zero risk: it is about aligning security controls with organisational appetite and opportunity.
-

VPNs: Complex, non-compliant, and lacking security for modern remote access
VPNs were once the go-to remote access solution but prove to be an insufficient foundation for secure remote access in today’s landscape
-

Securing the Distributed Supply Chain: Why Identity is the New Air Gap
The manufacturing landscape has transformed into a complex, distributed supply chain, yet security models remain dangerously outdated. This article exposes the critical friction points of Industry 4.0, revealing how legacy access methods create unacceptable risks. Learn why a Zero Trust Architecture, prioritizing identity, is the imperative solution for securing this interconnected world, making identity the new air gap.
-

ACME Manufacturing Transforms Security and Efficiency with Agilicus AnyX
ACME manufacturing chose Agilicus AnyX to enable SAP access to a multi-division, contract-manufacturing environment. Safely, Securely, Simply.
-

Secure Remote Updates For Air-Gapped Systems
Challenges with, and solutions for, Secure Remote Updates in modern complex control systems deployed in locked-down, air-gap-style networks. Agilicus AnyX enables and secures remote updates for air gaps.
-
Agilicus AnyX versus Splashtop
Compare Agilicus AnyX, a comprehensive Zero Trust Network Access platform, with Splashtop, a tool for remote desktop access. This article evaluates both solutions on features like native client support, single sign-on, multi-factor authentication, detailed auditing, and embedded HMI support, highlighting the security and functionality differences.
-
High Availability Dual WAN Remote Industrial Connectivity
Industry cannot stop. Industry is also commonly located in remote areas with less network connectivity choices. Learn how Agilicus AnyX facilitates High Availability Dual WAN Remote Industrial Connectivity.
-
Wastewater Zero Trust Remote Operations and Asset Management
Wastewater Zero Trust Remote Operations and Asset Management. Learn how this industrial control systems engineering company expanded their service offering with Agilicus AnyX.
-
Agilicus AnyX versus TeamViewer
A detailed comparison between Agilicus AnyX and TeamViewer, evaluating a comprehensive Zero Trust platform against a traditional remote access tool. This article highlights key differentiators, including Agilicus’s seamless single sign-on, browser-only access options, granular read-only roles, and extensive audit capabilities. Learn why customers are upgrading from niche legacy platforms to a full Zero Trust solution to enhance security, especially in light of recent cyber attacks on critical infrastructure.
-
Subscription Model and Remote Access In Industrial Control
Subscription Model and Remote Access In Industrial Control. The quest for revenue creates risks for operation.
-
Merging Local Identity With Online Identity
Modern online Identity with Azure, Google, Okta. Manufacturing plants with Local Identity — onsite users Unify with Agilicus AnyX
-

How the Town of Mono Future-Proofed its Cybersecurity Infrastructure and Transformed Municipal Operations
The Town of Mono future-proofed its cyber security infrastructure and exceeded compliance requirement by transitioning to Zero Trust.
-
Starlink Remote Cameras: 3-Steps to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable Starlink Remote Camera inbound remote access, despite CGNAT. Access your security video from anywhere.
-
Zero Trust VTScada Twilio Alerts
Zero Trust VTScada Twilio Alerts. Monitor your VTScada system with Twilio. Without exposing its login to the Internet. Simple, secure, no config change.
-

Starlink and Synology NAS: How to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable inbound remote access to your Starlink and Synology NAS setup, despite CGNAT. Access your files from anywhere.
-

NIST SP 800 53 Mapping To Zero Trust
NIST SP 800 53 Mapping To Zero Trust. NIST SP 800 53 is a comprehensive set of security controls. Zero Trust Network Architecture is a technology. Explore the intersection.
-

Case Study: Apple Screen Sharing, Zero Trust, Multi Factor Authentication
Remote Apple Screen Sharing with Zero Trust, Single-Sign-On, Multi-Factor Authentication. Without a VPN.
-

Zero Trust VNC Remote Desktop
1-click VNC remote desktop, single-sign-on, multifactor authentication. Zero Trust VNC Remote Desktop provides high-convenience with high security.
-

How the City of Kenosha Transitioned to Zero Trust
How the City of Kenosha Transitioned to Zero Trust using Agilicus Zero Trust to achieve EPA compliance and gain multi-factor authentication, vendor security, audit trails, and network visibility.
-
NIST SP 800-53 in Critical Infrastructure
NIST SP 800-53 is a core part of the NIST cybersecurity framework. It provides mappings of controls to various other standards. Zero Trust is a complementary architecutre supporting these controls.
-
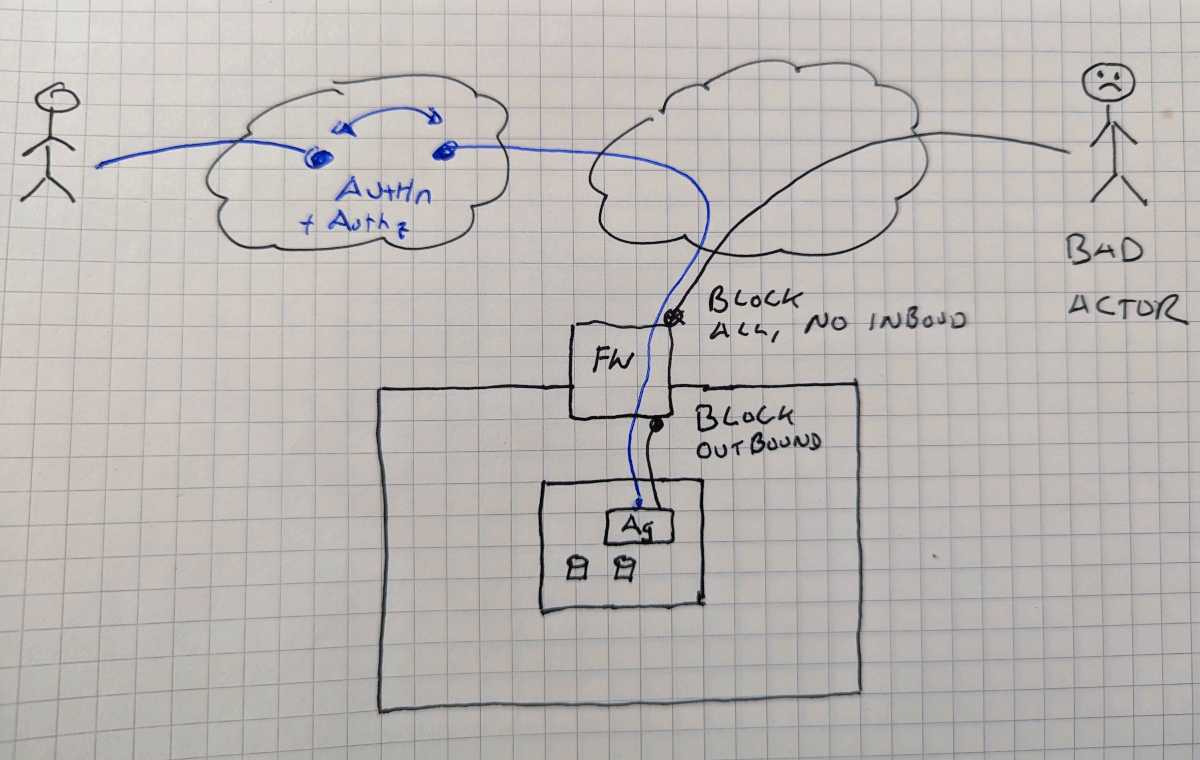
Zero Trust Air Gap Lock Down Inbound and Outbound
Air Gaps are a useful but inconvenient tactic as a part of a defense in depth strategy. Learn how a Zero Trust Air Gap Lockdown Inbound and Outbound can provide convenience and security together.
-
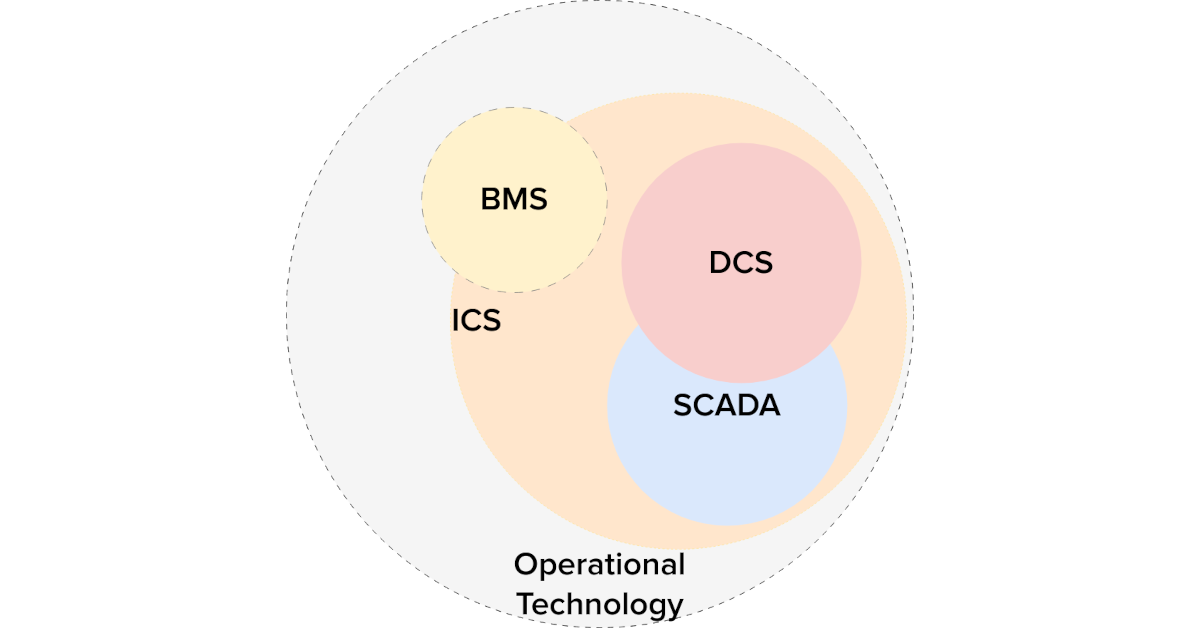
Piercing The Purdue Model: Zero-Trust In Operational Technology
Unravelling the interaction between the Purdue Model and Zero Trust: When married together in operational technology, the outcomes can be transformative.
-

Multi-Factor Authentication On The Internal Network
Cyber-Insurance compliance require multi-factor on internal network resources? Routers? Servers? Learn how to implement without a VPN, without changes.
-

Quickly Meet Cyber Security Insurance Requirements with Agilicus AnyX
Meet Cyber Security Insurance Requirements. Accelerate cyber readiness and reduce risk by adopting a network access and security strategy that meets compliance criteria while bolstering cyber defences organisation wide.
-

Case study: Protecting Critical Municipal Infrastructure and Securing Operational Technology at a Water Treatment Facility
Protect a municipal SCADA water treatment facility. Provide multi-factor authentication, secure remote access to staff and partners with single-sign-on.
-
Industrial Zero-Trust Micro-Segmentation
Micro-Segmentation Zones are a best practice for Industrial Control security. Simplify and increase effectivity with identity-based Zero-Trust. Industrial Zero-Trust Micro-Segmentation
-

Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture
Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture. Cyber threats come from all angles these days, yet most businesses are still ill equipped to properly keep the bad actors out.
-

Remote Desktop Access: Managing Cyber Risk with Zero Trust Network Access
Eliminate unmanaged cyber risk by securing remote desktop access through zero trust network access and improve your cybersecurity posture.
-

Strengthening Cybersecurity in Industrial Control Systems for Public Water Infrastructure
Secure and simplify your Industrial Control Systems to Improve Cybersecurity in Industrial Control Systems for Public Water Infrastructure
-

Azure Application Consent
The Agilicus AnyX platform uses external Identity Providers rather than creating ‘parallel’ identities for users to remember. What permissions are being granted on those upstream systems?
-
Case Study: Secure Access to Critical Infrastructure for Partners and Vendors
Critical Infrastructure for Partners and Vendors. A Municipality modernised a water treatment facility to enable secure connectivity for various internal teams (IT, Public Works), partner organisation, and their systems integrator.
-
Enabling Secure Access to Web Applications through Zero Trust
Learn how Agilicus helped a Canadian Municipality extend secure access to web applications for mobile workers through a zero trust framework.
-

Resources – Adopting Zero Trust with Agilicus AnyX
Resources: White Papers, Case Studies, Articles about how Agilicus AnyX Zero-Trust Network Architecture operates and the problems it has solved.
-

Third Party and Vendor Access Management for Critical Infrastructure
Adopting Vendor Access Management and enforcing multi-factor authentication for access to municipal critical infrastructure.
-

Add Multi-Factor Authentication to Legacy Systems with Agilicus AnyX
A municipality was seeking a method for securing access to the SCADA systems through the implementation of Multi-Factor Authentication.
-

Case Study: Secure Access to Critical Infrastructure for Partners and Vendors
Critical Infrastructure for Partners and Vendors. A Municipality modernised a water treatment facility to enable secure connectivity for various internal teams (IT, Public Works), partner organisation, and their systems integrator.
-
Secure Remote Connectivity to 100 Critical Infrastructure Sites, Nationwide
A major systems integrator that services critical infrastructure across the United States seamlessly transformed their service model through Zero Trust, to reduce costs while enabling secure remote connectivity to over 100 customer sites. Learn how Agilicus AnyX was used to simplify access while ensuring the systems integrator could adhere to each customers expectations on security.
-
Case Study: A VPN Alternative for Securing Remote Access to Legacy Applications
A municipality in Southern Ontario was seeking a method of securing remote access to legacy applications – responsible for the treasury, billing, and permit functions.
-

Agilicus AnyX Brochure
Agilicus AnyX is the only purpose-built product to solve the industry challenges of enabling any user (staff, partner, vendor) to safely, securely, simply remotely operate operational technology, without re-architecting the underlying SCADA networks.
-

Quickly Meet Cyber Security Insurance Requirements with Agilicus AnyX
Meet Cyber Security Insurance Requirements. Accelerate cyber readiness and reduce risk by adopting a network access and security strategy that meets compliance criteria while bolstering cyber defences organisation wide.
-

Strengthening Cybersecurity in Industrial Control Systems for Public Water Infrastructure
Secure and simplify your Industrial Control Systems to Improve Cybersecurity in Industrial Control Systems for Public Water Infrastructure
-

The Fragility of Interdependence: Securing the Hyper-Specialised Supply Chain in the Age of Cyber-Physical Convergence
The £1.9bn JLR breach exposed supply chain fragility. Download the Agilicus whitepaper to learn how Zero Trust secures the industrial mesh against cyber threats.
-

Multi-Site Manufacturing
The transition to multi-site manufacturing and industry 4.0 requires a remote access solution that delivers seamless, identity-based access for every site and contractor.
-

The Frictionless Factory: Solving the Connectivity Crisis in Hyper-Specialised
Is your VPN architecture killing your Mean Time To Repair? In the era of the hyper-specialized supply chain, legacy VPNs create operational drag and dangerous “Shared Fate” risks—as proven by the massive Fall 2025 Jaguar Land Rover outage. This whitepaper explains why modern manufacturers are abandoning Layer-3 VPNs for Agilicus AnyX. Discover how the “Island Architecture” delivers instant, clientless access to third-party experts, ensuring your production line stays up even when your supplier goes down. Read the full whitepaper to…
-

Agilicus AnyX Configuration Security
Cloud Configuration: What is the exposure? How is it protected? Learn how Agilicus AnyX is more secure than an on-premise system.
-

Securing the Distributed Supply Chain: Why Identity is the New Air Gap
The manufacturing landscape has transformed into a complex, distributed supply chain, yet security models remain dangerously outdated. This article exposes the critical friction points of Industry 4.0, revealing how legacy access methods create unacceptable risks. Learn why a Zero Trust Architecture, prioritizing identity, is the imperative solution for securing this interconnected world, making identity the new air gap.
-

VPNs: Complex, non-compliant, and lacking security for modern remote access
VPNs were once the go-to remote access solution but prove to be an insufficient foundation for secure remote access in today’s landscape
-

Secure Remote Updates For Air-Gapped Systems
Challenges with, and solutions for, Secure Remote Updates in modern complex control systems deployed in locked-down, air-gap-style networks. Agilicus AnyX enables and secures remote updates for air gaps.
-

High Availability Dual WAN Remote Industrial Connectivity
Industry cannot stop. Industry is also commonly located in remote areas with less network connectivity choices. Learn how Agilicus AnyX facilitates High Availability Dual WAN Remote Industrial Connectivity.
-

Subscription Model and Remote Access In Industrial Control
Subscription Model and Remote Access In Industrial Control. The quest for revenue creates risks for operation.
-

Merging Local Identity With Online Identity
Modern online Identity with Azure, Google, Okta. Manufacturing plants with Local Identity — onsite users Unify with Agilicus AnyX
-

NIST SP 800 53 Mapping To Zero Trust
NIST SP 800 53 Mapping To Zero Trust. NIST SP 800 53 is a comprehensive set of security controls. Zero Trust Network Architecture is a technology. Explore the intersection.
-

NIST SP 800-53 in Critical Infrastructure
NIST SP 800-53 is a core part of the NIST cybersecurity framework. It provides mappings of controls to various other standards. Zero Trust is a complementary architecutre supporting these controls.
-

Zero Trust Air Gap Lock Down Inbound and Outbound
Air Gaps are a useful but inconvenient tactic as a part of a defense in depth strategy. Learn how a Zero Trust Air Gap Lockdown Inbound and Outbound can provide convenience and security together.
-

Piercing The Purdue Model: Zero-Trust In Operational Technology
Unravelling the interaction between the Purdue Model and Zero Trust: When married together in operational technology, the outcomes can be transformative.
-

Multi-Factor Authentication On The Internal Network
Cyber-Insurance compliance require multi-factor on internal network resources? Routers? Servers? Learn how to implement without a VPN, without changes.
-

Industrial Zero-Trust Micro-Segmentation
Micro-Segmentation Zones are a best practice for Industrial Control security. Simplify and increase effectivity with identity-based Zero-Trust. Industrial Zero-Trust Micro-Segmentation
-

Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture
Eliminate Attack Vectors and Stop Cyber Threats in Their Tracks with a Zero Trust Architecture. Cyber threats come from all angles these days, yet most businesses are still ill equipped to properly keep the bad actors out.
-

Remote Desktop Access: Managing Cyber Risk with Zero Trust Network Access
Eliminate unmanaged cyber risk by securing remote desktop access through zero trust network access and improve your cybersecurity posture.
-

Azure Application Consent
The Agilicus AnyX platform uses external Identity Providers rather than creating ‘parallel’ identities for users to remember. What permissions are being granted on those upstream systems?
-

Starlink Port Forwarding
Starlink. Good enough except for starlink port forwarding. Reach your devices from remote with Agilicus, securely, simply, reliably.
-

From Smoke Stacks to Smartscapes: Evolving Industrial Operations in the Digital Age
Smoke Stacks to Smartscapes. Past, Present, Future, the evolution in-place of the industrial control system, and the airgrap that once protected it.
-
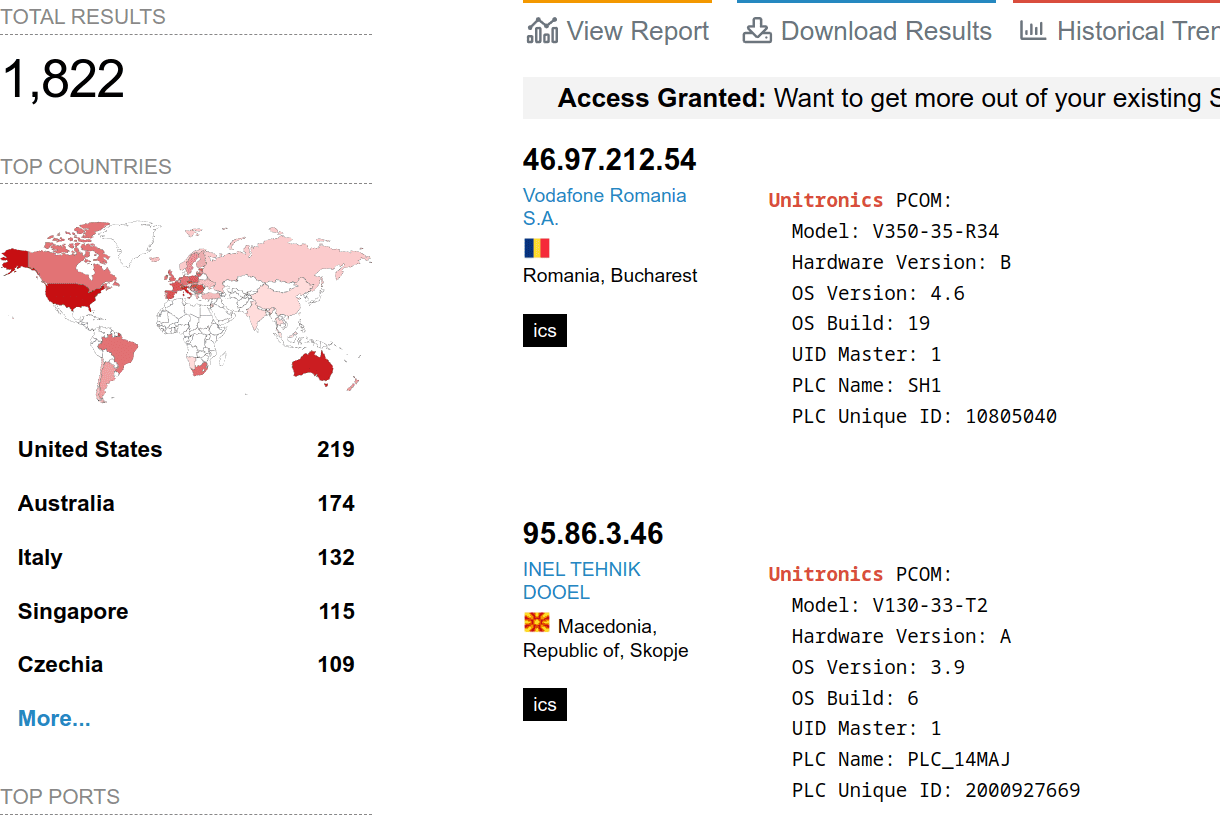
Avoid Exploitation of Unitronics PLCs used in Public Water Systems
Exploitation of Unitronics PLCs used in Public Water Systems for political purposes. Recommendations.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-

EPA Cybersecurity Recommendations: Unpacking the Impact on Public Water Systems
This article will help you understand the new EPA cybersecurity recommendations, why they matter for public water systems, and the recommended solution.
-

Protecting Against the OWASP Top 10 Web Application Vulnerabilities
The OWASP Top 10 is a standard awareness document that outlines the most critical web application security risks and vulnerabilities. Learn how Agilicus AnyX is designed to eliminate an attacker’s visibility into the potential OWASP Top 10 web application vulnerabilities.
-
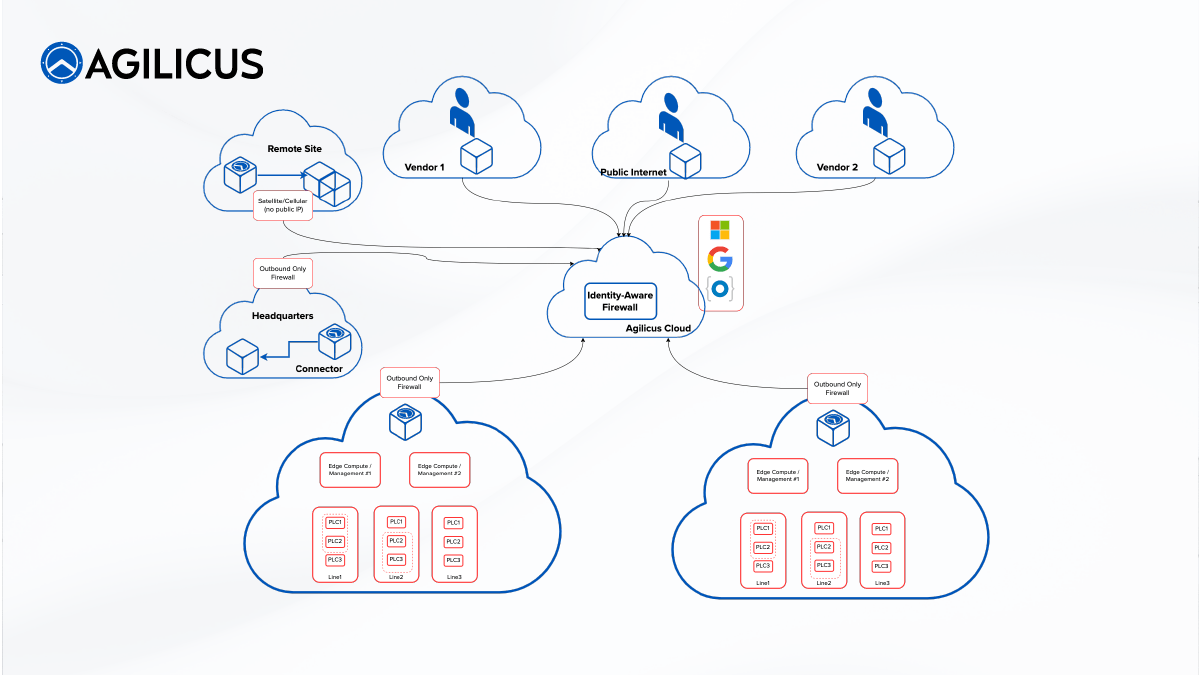
Agilicus and Operational Technology
Zero Trust Network Architecture can effectively meet the growing demand for enhanced cyber security in industrial and operational technology.
-

Industrial Air Gap – A Tale Of 2 Users
Industrial devices are hard to secure. Commonly done only via direct local access. Teams, however, wish remote access to improve efficiency. A solution to this battle is Zero Trust.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-
NIST sp 800-63B: How Well Do I Know You?
Zero-Trust Network Architecture has 3 steps: Authenticate (Who), Authorise(What), Access(How). 3 Levels of strength of the who are defined in NIST sp 800-63B. Does the goldilocks principle apply to you? Read on!
-

Agilicus AnyX versus Cloudflare Zero Trust
A direct comparison between Agilicus AnyX and Cloudflare Zero Trust. This article evaluates the fundamental differences between Agilicus’s simple, integration-focused platform and Cloudflare’s complex, DNS-based SASE approach. Key features examined include client-less access, one-click identity integration, and support for legacy and industrial protocols without requiring network changes.
-

Agilicus AnyX versus Tosibox
A detailed comparison between Agilicus AnyX and Tosibox for securing operational technology (OT) environments. This article contrasts the Zero Trust, application-aware proxy architecture of Agilicus AnyX with Tosibox’s orchestrated overlay VPN. Key differentiators examined include user-based authentication, single sign-on, browser-only access, and fine-grained authorization, highlighting the differences between a modern Zero Trust solution and a traditional VPN approach.
-

Agilicus AnyX versus Nebula
A comparative analysis of Agilicus AnyX and Nebula for secure remote access, with a focus on Operational Technology environments. This article contrasts Agilicus’s comprehensive Zero Trust architecture with Nebula’s overlay VPN mesh system. Key differences explored include the ability to connect to devices without client software, application-layer protocol awareness, and the capacity for detailed, per-user audit records.
-
Agilicus AnyX versus FortiSRA
A feature-by-feature comparison of Agilicus AnyX and Fortinet’s FortiSRA for securing Operational Technology (OT) environments. This article contrasts the complete Zero Trust architecture of Agilicus AnyX with FortiSRA’s approach, highlighting differences in agentless deployment, included high-availability, native identity integration for single sign-on, and support for legacy applications and embedded devices.
-

Understanding Cyber Security Risk
Risk management is not about achieving zero risk: it is about aligning security controls with organisational appetite and opportunity.
-
Agilicus AnyX versus Splashtop
Compare Agilicus AnyX, a comprehensive Zero Trust Network Access platform, with Splashtop, a tool for remote desktop access. This article evaluates both solutions on features like native client support, single sign-on, multi-factor authentication, detailed auditing, and embedded HMI support, highlighting the security and functionality differences.
-

Agilicus AnyX versus TeamViewer
A detailed comparison between Agilicus AnyX and TeamViewer, evaluating a comprehensive Zero Trust platform against a traditional remote access tool. This article highlights key differentiators, including Agilicus’s seamless single sign-on, browser-only access options, granular read-only roles, and extensive audit capabilities. Learn why customers are upgrading from niche legacy platforms to a full Zero Trust solution to enhance security, especially in light of recent cyber attacks on critical infrastructure.
-

Zero Trust VTScada Twilio Alerts
Zero Trust VTScada Twilio Alerts. Monitor your VTScada system with Twilio. Without exposing its login to the Internet. Simple, secure, no config change.
-

Zero Trust VNC Remote Desktop
1-click VNC remote desktop, single-sign-on, multifactor authentication. Zero Trust VNC Remote Desktop provides high-convenience with high security.
-

Northern Rockies Regional Municipality
How Northern Rockies Regional Municipality Transitioned to a Zero-Trust Enabled Work From Anywhere Environment with Agilicus AnyX
-

Managed Industrial Remote Access
Discover how Water Control Automation successfully deployed a managed industrial remote access solution using Agilicus AnyX. This case study explores the complex access requirements of diverse stakeholders—including equipment manufacturers, system integrators, and remote operators—and details how a Zero Trust framework met stringent security and operational demands. Key challenges addressed include enabling secure single sign-on, ensuring comprehensive audit trails, and eliminating the need for traditional VPNs.
-

Midland Texas Transforms Water Purification Cyber Security
The City of Midland, Texas chose Agilicus AnyX Zero Trust to secure its Water Purification plant
-

ACME Manufacturing Transforms Security and Efficiency with Agilicus AnyX
ACME manufacturing chose Agilicus AnyX to enable SAP access to a multi-division, contract-manufacturing environment. Safely, Securely, Simply.
-
Wastewater Zero Trust Remote Operations and Asset Management
Wastewater Zero Trust Remote Operations and Asset Management. Learn how this industrial control systems engineering company expanded their service offering with Agilicus AnyX.
-

How the Town of Mono Future-Proofed its Cybersecurity Infrastructure and Transformed Municipal Operations
The Town of Mono future-proofed its cyber security infrastructure and exceeded compliance requirement by transitioning to Zero Trust.
-

Starlink Remote Cameras: 3-Steps to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable Starlink Remote Camera inbound remote access, despite CGNAT. Access your security video from anywhere.
-

Starlink and Synology NAS: How to Enable Inbound Remote Access
Learn to use Agilicus AnyX to enable inbound remote access to your Starlink and Synology NAS setup, despite CGNAT. Access your files from anywhere.
-

Case Study: Apple Screen Sharing, Zero Trust, Multi Factor Authentication
Remote Apple Screen Sharing with Zero Trust, Single-Sign-On, Multi-Factor Authentication. Without a VPN.
-

How the City of Kenosha Transitioned to Zero Trust
How the City of Kenosha Transitioned to Zero Trust using Agilicus Zero Trust to achieve EPA compliance and gain multi-factor authentication, vendor security, audit trails, and network visibility.
-

Case study: Protecting Critical Municipal Infrastructure and Securing Operational Technology at a Water Treatment Facility
Protect a municipal SCADA water treatment facility. Provide multi-factor authentication, secure remote access to staff and partners with single-sign-on.
-

Enabling Secure Access to Web Applications through Zero Trust
Learn how Agilicus helped a Canadian Municipality extend secure access to web applications for mobile workers through a zero trust framework.
-

Case Study: Secure Access to Critical Infrastructure for Partners and Vendors
Critical Infrastructure for Partners and Vendors. A Municipality modernised a water treatment facility to enable secure connectivity for various internal teams (IT, Public Works), partner organisation, and their systems integrator.
-

Third Party and Vendor Access Management for Critical Infrastructure
Adopting Vendor Access Management and enforcing multi-factor authentication for access to municipal critical infrastructure.
-

Add Multi-Factor Authentication to Legacy Systems with Agilicus AnyX
A municipality was seeking a method for securing access to the SCADA systems through the implementation of Multi-Factor Authentication.
-

Case Study: A VPN Alternative for Securing Remote Access to Legacy Applications
A municipality in Southern Ontario was seeking a method of securing remote access to legacy applications – responsible for the treasury, billing, and permit functions.
-

Secure Remote Connectivity to 100 Critical Infrastructure Sites, Nationwide
A major systems integrator that services critical infrastructure across the United States seamlessly transformed their service model through Zero Trust, to reduce costs while enabling secure remote connectivity to over 100 customer sites. Learn how Agilicus AnyX was used to simplify access while ensuring the systems integrator could adhere to each customers expectations on security.
-

Why VPNs Are Not a Viable Solution for Multi-Site Manufacturing
As manufacturing networks expand, traditional VPNs create dangerous security gaps like lateral movement and unrestricted access. Join us to discover a safer alternative for multi-site connectivity. Learn how to implement secure, granular remote access that streamlines maintenance, enforces MFA, and protects your critical industrial systems—without the clunky VPN.
-
Improve Mean Time To Repair with a Zero Trust Architecture for Remote Maintenance
When a system suffers an outage or other operational issues, requiring internal or third-party users to be on-site can cost valuable time and money. Allowing your users to remotely access systems allows you to resolve issues faster.
-

How AI Threatens the Industrial Control Systems in Small and Mid-Size Manufacturing
As we move towards 2026 and AI tools become more capable, hackers are turning to them more and more, creating new threats across the board. Explore how you can protect your organization by adopting Zero Trust
-

Cyber Breaches Can Shut Down Your Production Floor
The manufacturing industry is going through a revolution, industry 4.0, impacting the industrial control systems on your manufacturing floor. Protect your organization from evolving threats.
-

Protecting Local Governments from Evolving Cyber Threats
With a recent rise of threat actors conducting large scale cyber attacks you need to ensure that remote access is properly implemented and systems aren’t reachable to threat actors.
-

Upcoming Remote Access Regulation: How Zero Trust Prepares Your Water Infrastructure
Maryland is mandating water facilities and critical infrastructure adopt strict cybersecurity policies for their remote access and network operations. States like New York, California, Texas, and others are quickly following suit. Stay Ahead with Zero Trust
-

Zero Trust: The Cyber Security Mandate for Insuring Your Municipality.
Learn how a Zero Trust framework helps municipalities meet evolving cyber insurance requirements, comply with state mandates, and secure remote access.
-

Municipal Remote Access: Protecting Against Cyber Threats While Streamlining How Users Access Shared Resources
Cyber threats against municipalities are increasing and becoming smarter. With AI backed threat actors and new network vulnerabilities being taken advantage of, the threat to municipalities is larger today than ever. This webinar offers a look into protecting your municipality resources while streamlining remote access.
-

The New Standard for Industrial Water Systems: Industry 4.0 and Hybrid Workforces
Water/wastewater facilities are going through a revolution with technology becoming engrained in critical infrastructure operations. Learn how to safely allow remote access to your critical infrastructure.
-
Cyber Criminals are Adopting AI: Keep your Critical Infrastructure Protected
As threat actors increasingly adopt the use of AI they’ve become able to execute cyber attack attempts at a more personal level, faster. Learn how you can protect your critical infrastructure in a new cyber threat landscape.
-

Protecting Water Systems from Cyber Threats
Don’t choose between security and accessibility. Learn how to secure your water systems while empowering your team to remotely access the resources they need.
-

Remote Operations: Support Client Systems Without VPNs
Your clients rely on your team to keep their industrial control systems up and running smoothly through routine maintenance and ongoing remote support. Learn how you can deploy efficient and effective remote operations while exceeding client security policies
-

Improving Wastewater Remote Connectivity with Zero Trust
Learn how you can enable remote connectivity to industrial water systems on wastewater treatment facility networks.
-

How Securicore Utilizes Zero Trust for Remote Access
Join Agilicus and Securicore to learn how you can enable Zero Trust remote access to the systems/resources on your network
-

Eliminate Shared Passwords for Vendor Access
Learn how you can – without sacrificing security or creating a large spend in time, effort, and resources – enable remote access to industrial control systems on your floor
-

How to Implement Zero Trust for Local Government
Local governments are making the switch to a Zero Trust security model to protect their systems against modern threats. Join us to learn how.
-

Securely Connect to Client Resources, Streamline Operations
Your clients rely on your team to help keep their industrial control systems up and running (HMI, PLC, SCADA) smoothly through routine maintenance and ongoing remote support. Providing remote support can become a headache when firewall/VPN configurations are unique for each client, requiring multiple logins, settings, and platforms for each support ticket.
-

HMI, PLC, and SCADA Water Systems with Multi-Factor Authentication
Multi-factor authentication and single sign-on are two quick and effective ways to improve your security posture without causing a major disruption in your users’ workflow
-

VNC & RDP for Water: Access Dashboards Remotely
Learn how to get the most out of your Virtual Network Computing (VNC) and Remote Desktop Protocol (RDP) for HMI and other usage
-

Add Remote Operations: Support Clients Faster & Reduce Costs
Learn how implementing remote operations to your organization can unlock new efficiencies in the way you troubleshoot and service client systems.
-

Master Vendor and Contractor Access Management
Learn to establish and leverage a robust vendor access management program that reduces third-party cyber risk without complicated workarounds
-

Add Wastewater Remote Operations, Streamline Service
Join us to learn how implementing remote operations to your organization can unlock new efficiencies in the way you troubleshoot and service public water systems.
-

VPN Alternatives for Water and Critical Infrastructure
Learn how we can connect the people who need it. Single Sign On for all, regardless of partner or employee. Multi-factor where needed, even on legacy applications. WITHOUT granting full VPN access.
-

Legacy Life-Extend: More Users, More Secure, No Changes
Legacy municipal support systems are difficult to make widely available without compromising security. Learn how to solve.
-

Cyber Alerts, Best Practices: Put Advice To Action
Government agencies are publishing cyber advice. Each notice is individually full of good facts and advice, but collectively, they are creating indecision: what do I do first? when? how? With what budget? Today we will talk about how to interpret, how to implement, economically, without disruption.
-

A VPN Alternative for Local Governments
The VPN, a powerful tool, is not appropriate for all users. Learn how we can connect the digitally disenfranchised. Single Sign-on for all, multi-factor on everything.
-

A VPN Alternative for Manufacturing
The VPN, a powerful tool, is not appropriate for all manufacturing users. Learn how we can connect the people who need it.
-

Cybersecurity on a Budget, Secure and Simple
Whether it’s remote operations and support, on site staff, or routine maintenance – ensuring your industrial water systems have proper access controls without causing a strain on your budget is crucial.
-

Add Remote Support, Leverage Your Specialists
Learn how to enhance efficiency and reduce costs by enabling remote support for your specialist teams. This webinar explores how Agilicus AnyX allows you to meet customer security requirements, incorporate remote access into your service offerings, and lower mean time to repair. Discover how to empower your automation and support specialists to manage multiple client needs simultaneously without the need for costly site visits, VPNs, or hardware installations.
-

Simplify Remote Access, Secure Industrial Equipment
No VPN, No Shadow IT Like TeamViewer. Simplify and Secure remote manufacturing industrial access for multiple divisions, contract manufacturers, vendors
-

SSH via Zero Trust. No public IP needed.
Use Zero Trust networking to provide access with no public IP, no inbound firewall changes, and, remain end-to-end encrypted.
-
Authentication and the API Key
We all think about authentication as a user signing-in. But what about, once signed in, the ‘create api key’ that is a permanent password? Where does that go? Zapier? Script in home dir?
-
Simple 3-Step Program To Reduce The Risk Of Ransomware
Learn a simple 3-step program to significantly reduce the risk of ransomware attacks. This video outlines the foundational principles of modern security: Authentication, Authorization, and Access. Key steps include enabling multi-factor authentication on your identity provider and consolidating all applications to use a single identity, eliminating locally stored accounts. Discover how implementing these measures can shift your security posture from risk to reward.
-

tailscale
Tailscale creates a better VPN. Agilicus AnyX replaces the need for one. Discover why Layer 7 precision beats Layer 3 connectivity for modern security.