Category: Defence-In-Depth
-
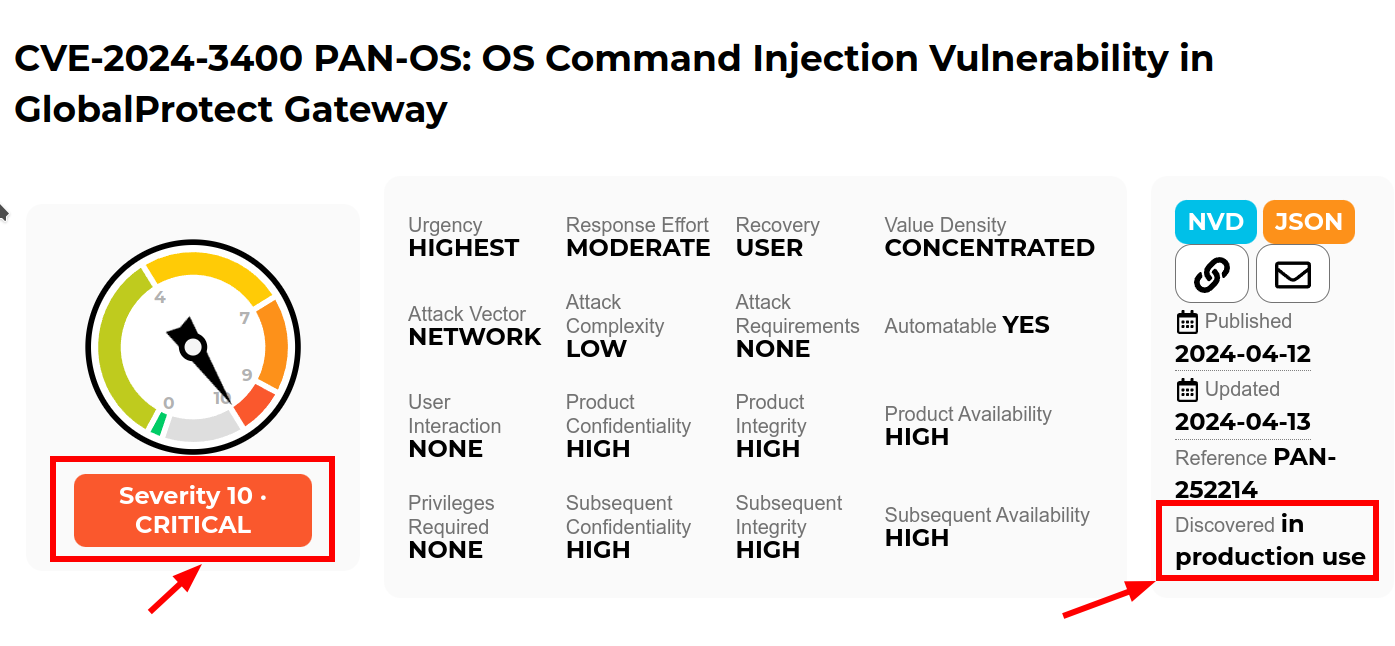
Quis custodiet ipsos custodes: When Good Firewalls Go Bad
Recently Palo Alto announced a 10.0 CVE in the Global Protect feature of their PAN-OS firewall. “Unauthenticated attacker [can] execute arbitrary code with root privileges on the firewall”. Well, that is not good. But, how “not good” is it? It’s terrifyingly bad ungood in fact.
-
Three Strategies To Help: Cisco ASA AnyConnect and WebVPN added to CISA Known Exploits
Cisco ASA AnyConnect and WebVPN added to CISA Known Exploits. Do you have one running on autopilot in your plant somewhere? Maybe between the IT and OT network? Maybe running the DMZ?
-

Ground Hog Day: Fortinet VPN Edition
Another day, another VPN letting the world in to snoop around and fondle your crown jewels: Fortinet edition.
-

Dutch Defence Detail Dastardly Dirty Deed
The Netherlands ministry of defence just published the cliff-hanger document TLP:CLEAR MIVD AIVD Advisory COATHANGER regarding a remote access attack of their Fortinet FortiGate VPN by “a state-sponsored actor from the People’s Republic of China”. CVE-2022-42475 was the weakness. One thing that is unusual about the report is the direct attribution: this is rare.
-

Howto: Open Source Intelligence and your Digital Footprint
Let me show you a very simple means of Open Source Intelligence (OSINT) on yourself. If I can do this, anyone can do this, and if anyone can do this, someone bad can do this.
-

Off-Grid Agricultural Cyber Physical Systems
The “John Deere Business Model” of taking something traditional and making it subscription. Starlink and its complex remote access needs due to CGNAT. And, cybersecurity, notably Cyber Physical Systems with their scary downsides of being able to move and cause damage.
-
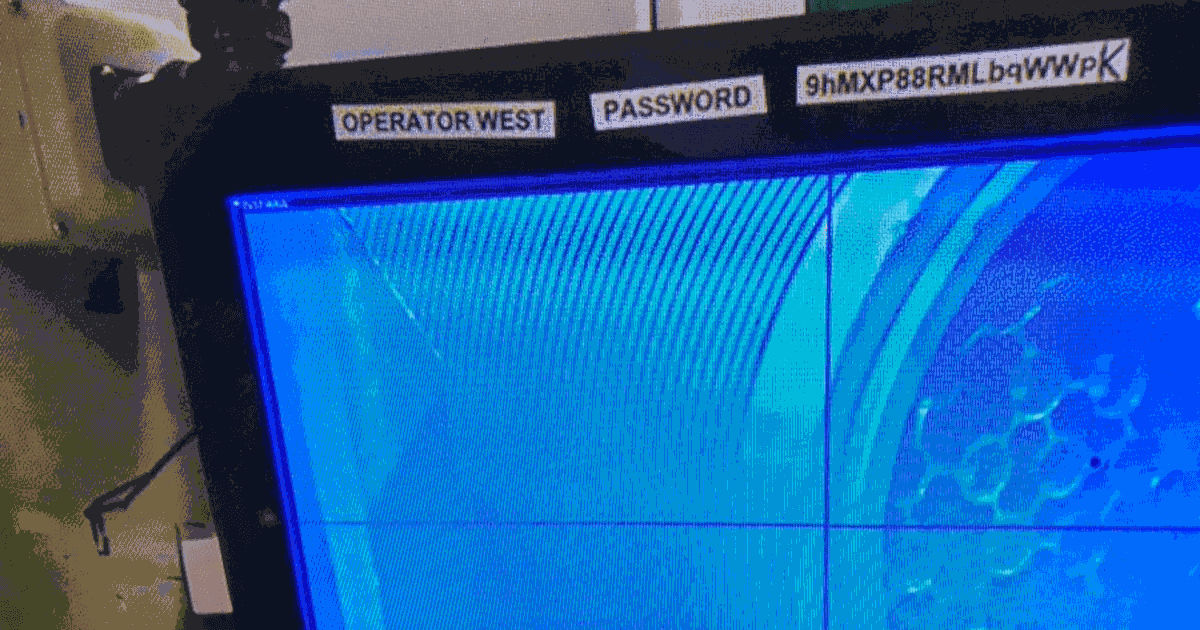
Hard Industrial Cybersecurity is hardly secure, nuclear waste edition
One thing all industrial control installations have in common, they straddle the complexity of modern information technology with the dangers of operational technology and its inherent control of things which can go bump and boom. Hard Industrial Cybersecurity
-
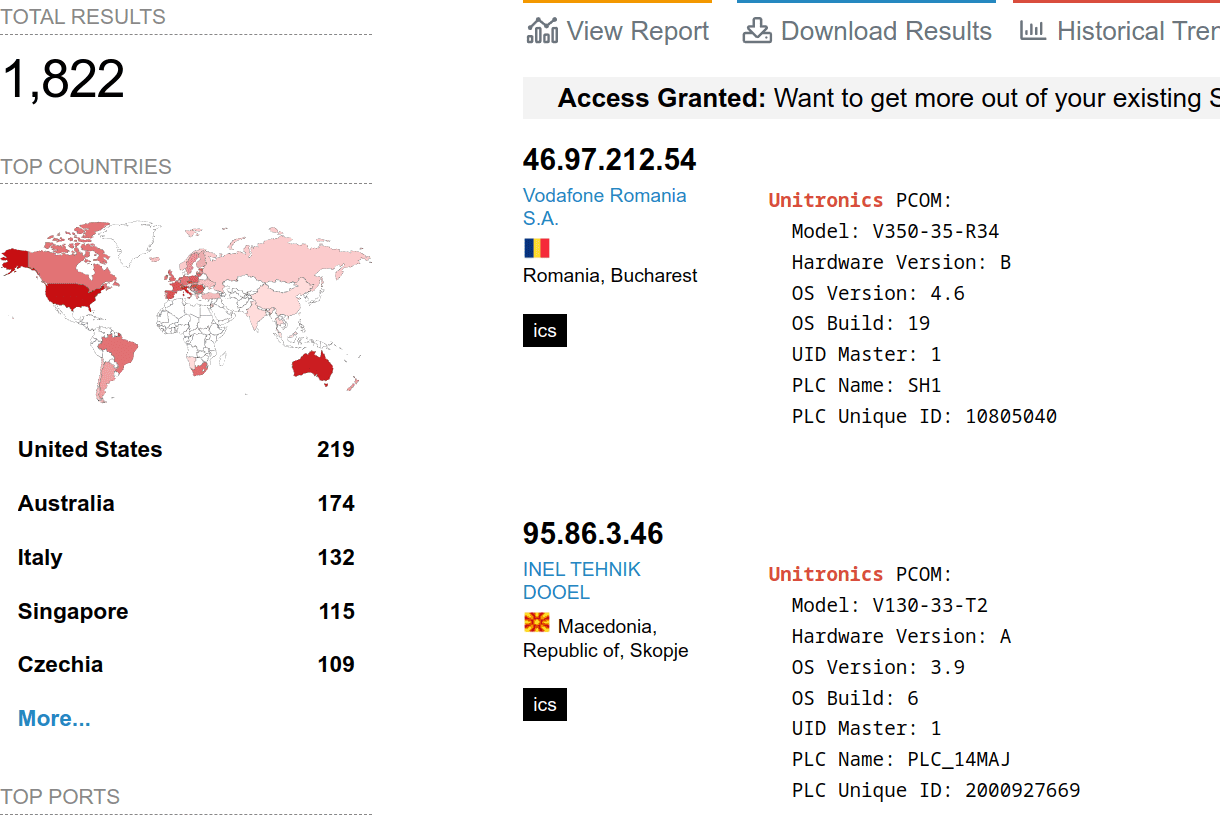
Avoid Exploitation of Unitronics PLCs used in Public Water Systems
Exploitation of Unitronics PLCs used in Public Water Systems for political purposes. Recommendations.
-

Attainable Municipal Zero Trust
Attainable Municipal Zero Trust: Key insights from recent Zero Trust implementations by Municipalities. Why, How, What ROI, Lead use cases.
-
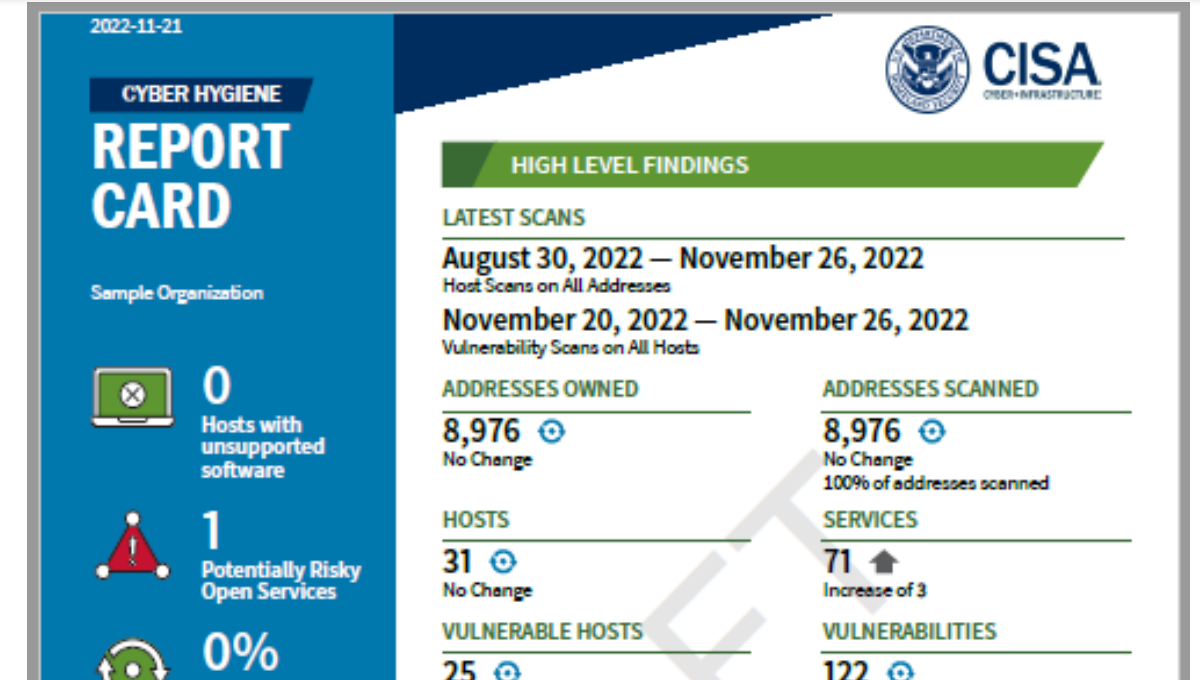
CISA Cyber Scan Water
CISA has announced a free (as in beer) service to scan water systems for vulnerabilities. Agilicus has used this scan for a year, receiving weekly reports.
-

Terminator Becomes National Standard
I’ll be back. Iconic line foreshadows rise of cyber-physical-systems. Terminator trifecta of physical machines, artificial intelligence, cyber-security awry.
-
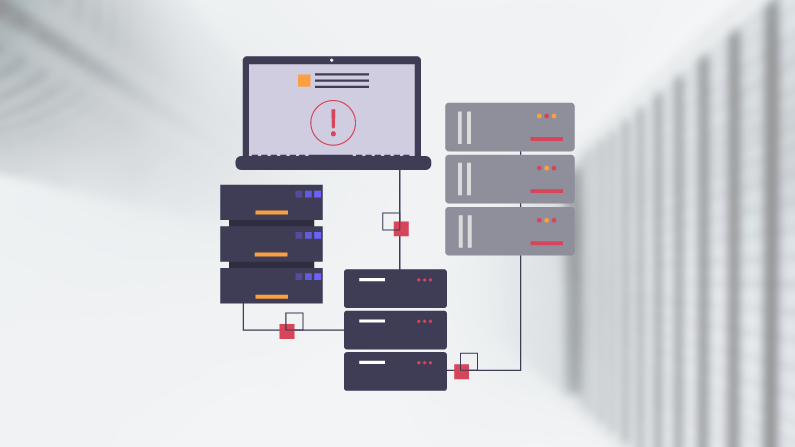
Another Day, Another Exploit – Protecting Against the ProxyNotShell Exchange Server Zero-Day Vulnerability
Learn how zero trust protects against the new Microsoft Exchange Server zero-day exploit affecting Outlook Web Access (OWA), ProxyNotShell. With Agilicus, you’ll block lateral traversal and prevent unauthorised traffic from arriving at your resources while ensuring they are still accessible to legitimate users.
-

Well Timed or Coincidental, Cue the Phishing Attacks as 2.5M Students Affected by Data Breach
Days after announcing student loan forgiveness in the United States, 2.5 million student borrowers had their personal information exposed in a data breach and are at an increased risk of being targeted in a phishing attack.
-

Protecting Against the OWASP Top 10 Web Application Vulnerabilities
The OWASP Top 10 is a standard awareness document that outlines the most critical web application security risks and vulnerabilities. Learn how Agilicus AnyX is designed to eliminate an attacker’s visibility into the potential OWASP Top 10 web application vulnerabilities.
-

Quickly Meet Cyber Security Insurance Requirements with Agilicus AnyX
Meet Cyber Security Insurance Requirements. Accelerate cyber readiness and reduce risk by adopting a network access and security strategy that meets compliance criteria while bolstering cyber defences organisation wide.
-
570 News Agilicus Interview
Interviewed on 570 News Tech Spotlight. listen to the interview here, I talk through some of the simple risks and how we help. And a bear joke.
-
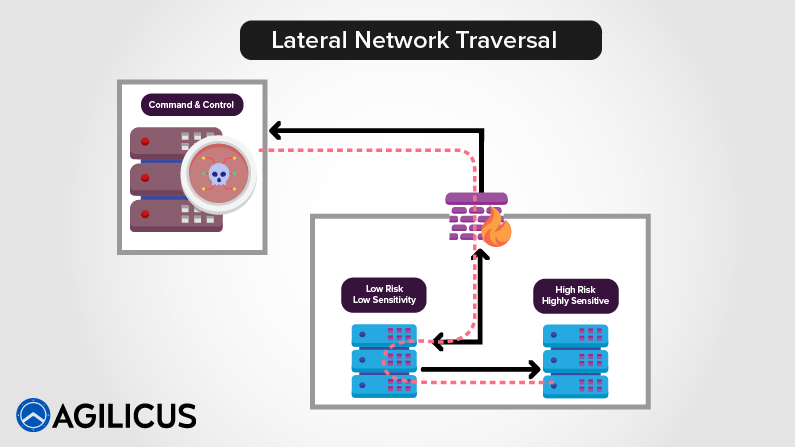
Chewy Centre Protected By A Sponge
The M&M is not a good network design: chewy centre, hard shell. Recent cisco router vulnerabilities discussed for defense in depth.
-

Log4Shell – Not Even the Smart Thermostat is Safe
Ignoring systems that may be deemed ‘unimportant’ in comparison to your revenue-generating technology stack will leave your organization open to compromise from the Log4Shell vulnerability.
-

A Little Consequences Go A Long Way: Return Of The Bear Joke
Two hikers see a bear. One bends over to tie shoes. Other says, you can’t out run a bear. First says, just need to outrun you. Pause laughter
-

Fake It Till You Make It: Canadian Bank Multi-Factor Authentication Edition
A big 5 Canadian bank has a fake multi-factor authentication sytem, allowing anyone to fall back to password. Why? How is this acceptable?
-
The Economic Cost Of Not Having Multi-Factor: MSP Lawsuit Edition
Managed Service Provider Breached. Customer pays out. Who is at fault? Lawsuit to determine. Multi-factor authentication to prevent.
-

Cyber-Security For Thee But Not For Me
How some public sector entities have great cyber-awareness training, but exempt the elected and senior staff. From Great To Good in one step.
-

Minimum Viable Secure Product
A simple set of controls for a Minimum Viable Secure Product. Open source for us all to use. Implement, ask in RFP, common baseline to follow
-

Telnet In Canada: Why?
Telnet. 40 years old, not fit for purpose. Alive and well in Canada. No amount of mitigation or multi-factor authentication makes it OK.
-
Syniverse Hack, Multi-Factor Authentication, Who Cares? You Should!
This article discusses SMS as a second factor for multi-factor authentication in context with the Syniverse hack.
-

I AM. I HAVE. I KNOW. Multi-Factor Authentication
I AM. I HAVE. I KNOW. The trifecta of simple and secure. Why does it improve security so much? Because the factors are not correlated. Use at least 2.
-
Add multi-factor authentication to old applications
Your cyber insurance is up for review. IGet all applications authenticated with multi-factor, simply, quickly, compliantly.
-
The Pipeline Ransomware Came Via The VPN
A criminal group takes over a nations energy via a VPN. Its time to treat the VPN as a risk, not a security solution. Zero Trust is better.
-

Zero Day Zero Trust Is Your Defense in Depth
Zero Trust. The principle of limiting access to user resource pairs. It is part of a good defense in depth strategy. It is also a key defense to Zero Day.
-

3 Simple Steps To Reduce Ransomware Risk
These three simple steps will dramatically reduce your ransomware risk. Achievable, understandable, reasonable.