AnyX Guide Type: example
-

Phoenix Contact PLCnext Engineer with Zero Trust
Support and manage PLCNext devices across multiple customers, multiple sites, simultaneously, without a VPN, with Agilicus AnyX
-

VTScada Single-Sign-On
Enable single-sign-on, multi-factor authentication to VTScada for external users via Agilicus AnyX
-

Hikvision DS-2CD3132-I
The Hikvision DS-2CD3132-I is an embedded CCTV surveillance camera. It is entirely unsafe for it to have any Internet access, either inbound, or outbound. However, it is a solid device with good performance. In this example, we recommend putting the device on an isolated network segment, no inbound, no outbound connectivity. Straddling this segment place…
-

Microsoft Power BI Desktop And Zero Trust with Agilicus
With Microsoft Power BI desktop application and Agilicus AnyX one can visually explore data through a free-form drag-and-drop canvas, a broad range of modern data visualizations, and an easy-to-use report authoring experience.
-

Agilicus Zero Trust with acSELerator QUICKSET
The SEL Quickset communication software is a tool to quickly and easily configure, commission, and manage devices for power system protection, control, metering, and monitoring. When used via Agilicus, it can be used securely through the AnyX platform via a Zero Trust approach.
-

Sample LibreNMS Application
Create an authenticating proxy to LibreNMS on a private network.
-
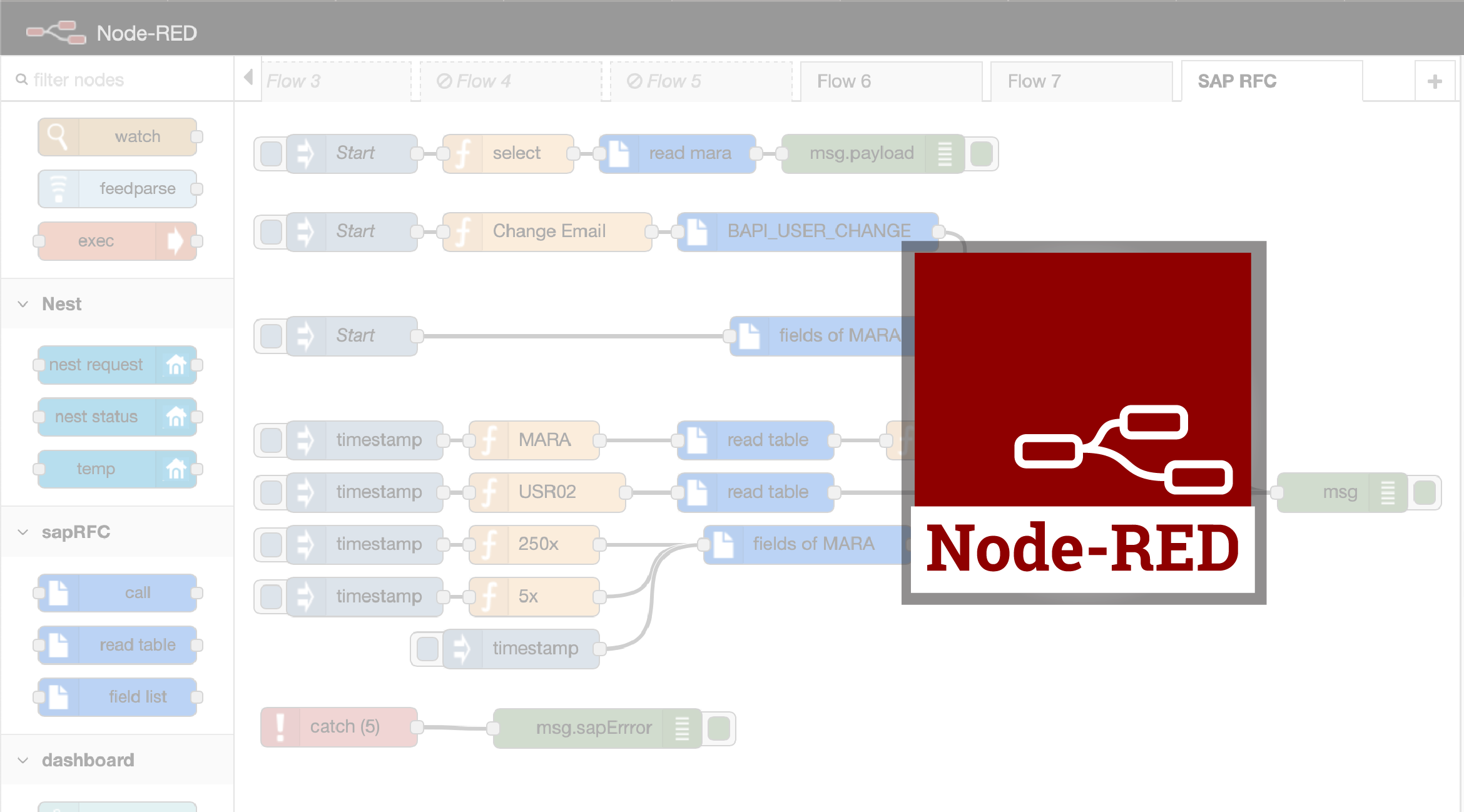
Sample Node Red
Node Red is a web-based hardware event programming system. It is ideal to run under Agilicus AnyX
-
Sample: CNAME With Google Domains
Configure your own custom domain to use with Agilicus AnyX. Example with Google Domains shown.
-
Sample Grafana In Kubernetes
Secure access to Grafana in Kubernetes: no ingress, any user, single sign on
-
Sample Application Demonstration
A sample web server, single executable, instructions on how to run it as if it were e.g. your wiki, and securely expose it to named users on Internet.
-

Sample Dual-Endpoint Web Application (Dashboard + API)
Some web applications have HTML + API’s separately. See how to login as a single endpoint and use externally without change.
-

Locked-Down Networks Certificate Revocation
Your firewall blocks all but specific outbound IP access. Your Let’s Encrypt or other certificates are not checking CRL or OCSP revocation. Here we show how to resolve.
-

VTScada and Twilio Inbound Access
VTScada and Twilio Inbound Access. VTScada interfaces to Twilio for alert management, nominally requiring inbound IP. Do with private IP, no port forwarding, geo-ip block via Agilicus AnyX
-
Sample: Hosted Icecast
Learn how to setup an on-site icecast server, give it public Internet access with no firewall changes.
-
Sample Hosted Application
You compile your web application, we do the rest: hosting, certificate, authentication, logging. Just drag and drop the zip from your build.
-
Sample React Application
Create a sample React application, configure it to use OpenID Connect Authentication and Authorisation to Agilicus platform.
-

Sample: Rockwell Studio 5000
Learn how to use the Agilicus Launcher with Rockwell Studio 5000 RSLinx to seamlessly access PLCs in multiple sites, without a VPN.
-

Sample: Schneider Electric Control Expert
Learn how to use the Agilicus Launcher with Schnedier Electric Control Expert to seamlessly access PLCs in multiple sites, without a VPN.
-

Sample Kafka Messaging From AWS VPC To Private Network
Access a Kafka broker with no direct network access, both ends firewalled from each other, from the world.
-

Connect to VTScada – Adding a Web Application
Learn how to add an application to the Agilicus platform and connect to VTScada through a zero trust model
-
Real VNC & Raspberry Pi
The Raspberry PI (with Raspbian) comes pre-installed with a VNC-like server. This can be configured to support standard authentication and used via Agilicus Any-X
-
Sample: Synology Local SSL
No more snake-oil self-signed certificates, even on local lan. Let Agilicus AnyX connector automate the task.
-
UDP via SSTP VPN
Use Agilicus AnyX as a means of connecting a VPN to an otherwise unconnectable location. UDP via SSTP VPN
-

Agilicus Connector Air Gap Machine With Containers
Setup a host firewall to create a virtual airgap on a Linux machine running containers with the Agilicus connector.
-

Print Via Service Forwarder
Print on a remote printer from a local site. Use the Agilicus Connector plus Service Forwarder.
-

Print via Launcher
Use a remote printer from a local application via Agilicus Launcher.