
Power BI and Agilicus
Microsoft Power BI Desktop and Agilicus.
With Microsoft Power BI desktop application, the desktop companion to the Power BI platform, one can visually explore data through a free-form drag-and-drop canvas, a broad range of modern data visualizations, and an easy-to-use report authoring experience. By combining Zero Trust Network Access to this Microsoft tool, it becomes possible to access remote databases and reports in a secure end-to-end, TLS encrypted, Identity verified session without the need for a corporate VPN.
The Agilicus Launcher
To enhance the Power BI desktop client, we will configure a Launcher in the Agilicus management console for administrators. To learn more about the concept of Agilicus Launchers, our Product Guide offers an introduction to this secure approach at remote application deployment.
In order to properly define the end to end secure properties inside which Power BI will be enabled, we must first define the Network Resource(s) the application will be allowed to use inside our network where the Agilicus Connector is deployed. By using the principle of least privilege (PoLP), we will only expose the database resource required by the application, and we will choose whether to do so by the database IP address, or optionally, by creating an internal hostname that is only resolvable through the Agilicus AnyX platform.
For the purposes of this example, we are using Power BI Desktop (x64) v2.129.905.0 (Published 05/21/2024)
Configuring the Network Resource
In the Resources – Networks , we will define the necessary SQL Server for PowerBI to access via a Connector.
Option 1. By IP address
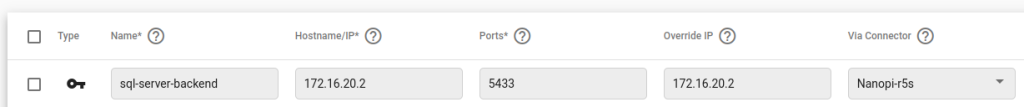
Here we are creating a Network Resource ‘sql-server-backend’ where we will define the IP address (172.16.20.2) of the SQL Server at TCP port 5433 to be reached by the connector ‘Nanopi-r5s’. This IP address must be reachable by the Connector inside the network where it is deployed.
Option 2. By dedicated hostname
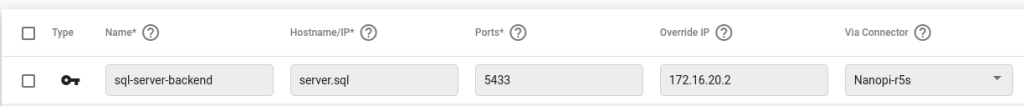
In this case, we are creating a fictitious hostname to resolve ‘server.sql’ entirely within the Agilicus AnyX platform. This hostname does not need to be resolvable on the public DNS infrastructure, conform to a real TLD requirement, or even be resolvable inside your corporate network. The Agilicus Launcher functionality will allow the local desktop application to resolve this hostname uniquely and route the TCP connection data to the ‘Override IP’ field IP address, which is still defined as ‘172.16.20.2’. Using a hostname based resource definition has the added benefit of not sharing the Internal IP addressing scheme of your secure network, allows for routing to the same IP address (IP space overlap) at different sites (via unique Connector), and does not reveal the IP address of the internal resources to the user.
Creating the Power BI launcher
Next, inside the Resources – Launchers menu, we will define the installation and runtime parameters of Power BI. We will assign a unique name that will be deployed on the local user Desktop icon under the Agilicus start menu folder. Using the default installation parameters for PowerBI, the following launcher configuration is made:
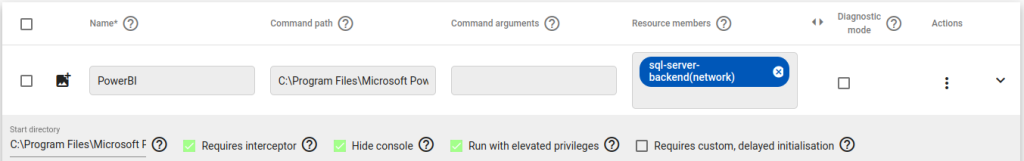
Name: Here we choose ‘PowerBI’
Command Path: This is the direct path to and including the executable.
C:\Program Files\Microsoft Power BI Desktop\bin\PBIDesktop.exe
Resource members: This will be the Network Resource(s), or Resource Group we wish to make available to the application. Here we assigned the ‘sql-server-backend’ network created in the previous step.
Start Directory: We can obtain the working directory from the native application properties.
C:\Program Files\Microsoft Power BI Desktop\bin\
Requires Interceptor: We will enable the DNS based and IP interception to allow Power BI to transparently access the network resources.
Hide Console: We can choose to hide the Agilicus Launcher console if no troubleshooting or debugging needs to be visualized.
Run with Elevated Privileges: The Power BI desktop application communicates with multiple Microsoft desktop components in order to operate and access network resources. We will permit the Agilicus Launcher to inspect process threads and other desktop elements executing network calls on behalf of Power BI. In order to do so, we must grant the Agilicus Launcher elevated privileges at runtime.
Using the Power BI Launcher
After deploying the Power BI application on the desktop and enabling the Agilicus Desktop Integration, the desktop user will have access to the set of Launchers under the Agilicus start menu.
Note that the name of the Launcher is the one we defined in the previous step ‘PowerBI’ and can be distinct from the default local Power BI desktop icon ‘Power BI Desktop’.
Once launched we can test the SQL Server database connectivity by doing a direct query to it:
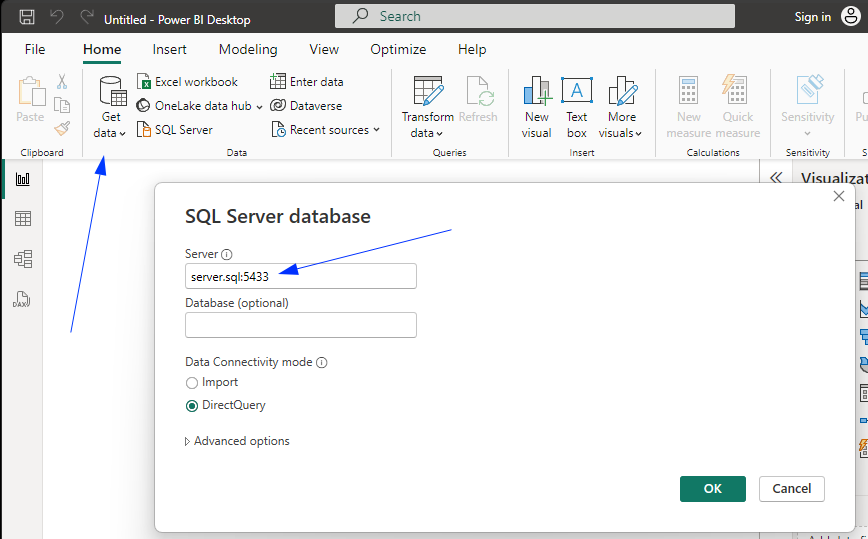
The SQL server information will be the same as the Network Resource configured in the previous step.
For example, if the network resource was defined as an IP address, then the SQL server field should bear that IP address: 172.16.20.2 and the TCP port. If the resource was defined as a Hostname, as illustrated, the hostname created in the network resource can be used with the TCP port eg: server.sql:5433 . Note that if the IP address is known by the user, it is also possible to use it weven if the resource is defined as a hostname.