CNAME + DOMAIN
Theory of Operation
Use your own domain name with Agilicus AnyX.
Setup Planning: Domain Name (CNAME) Setup
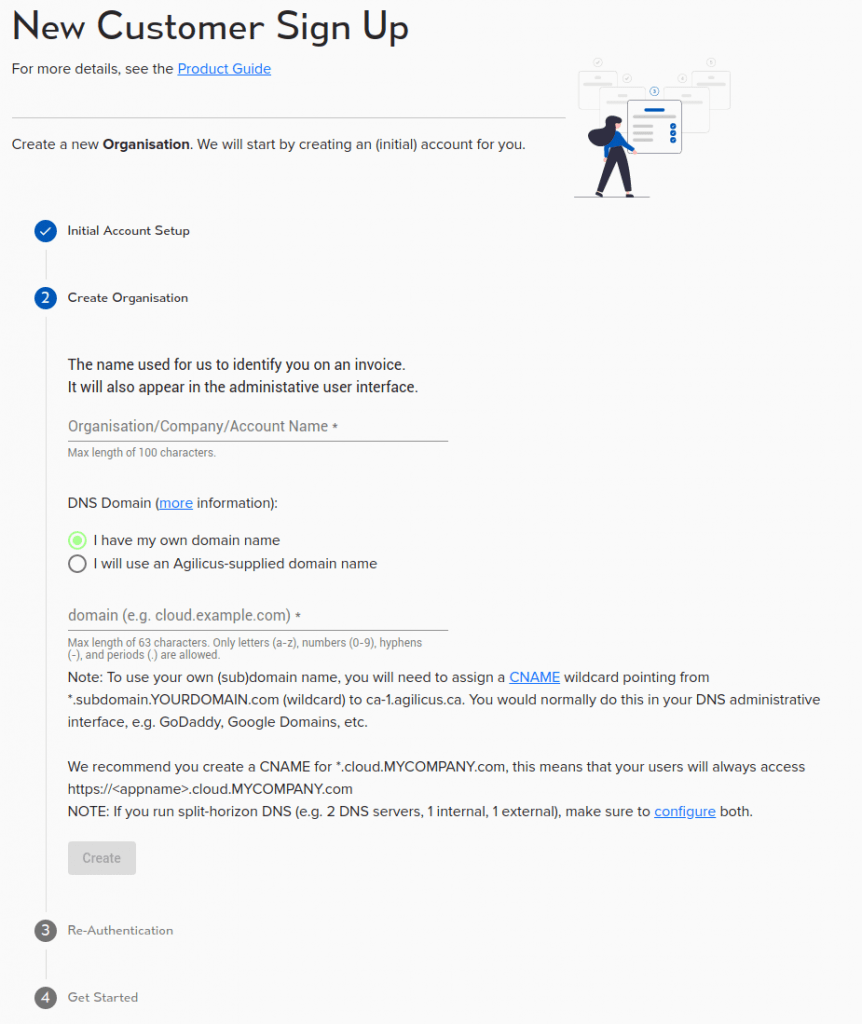
When creating a new Organisation through the Signup process, you are asked 2 questions:
- “Organisation/Company/Account Name”
- “DNS Domain”
On the “DNS Domain” you have 2 choices:
- “I have my own domain name”
- “I will use an Agilicus-supplied domain name”
The “Organisation/Company/Account Name” is used for billing purposes, and for metrics. It does not appear to the end-users of your company.
The ‘DNS Domain’ is used by all users (administrative and end-user). Notably,
- https://admin.DOMAIN 🠒 the administrator will sign-in here to configure and update the system
- https://auth.DOMAIN 🠒 for any sign-in activity, the user will be redirected here during the sign-in process according to the OpenID Connect specification
- https://profile.DOMAIN 🠒 end-users can see a ‘launcher’ of all applications in the organisation, and adjust their multi-factor authentication preferences
- https://APPNAME.DOMAIN 🠒 for each application you configure, a public URL will be created via its name and the domain you choose.
If you choose to use an Agilicus-supplied domain name, we will attempt to use your organisation name in conjunction with agilicus.{cloud|net|org}.
If you choose “I have my own domain name”, the administrator and end users will never see our domain. We recommend this option. In this model, you are delegating a sub-domain of your own to our system to manage on your behalf. So for example, you can say “*.cloud.MYDOMAIN” is managed.
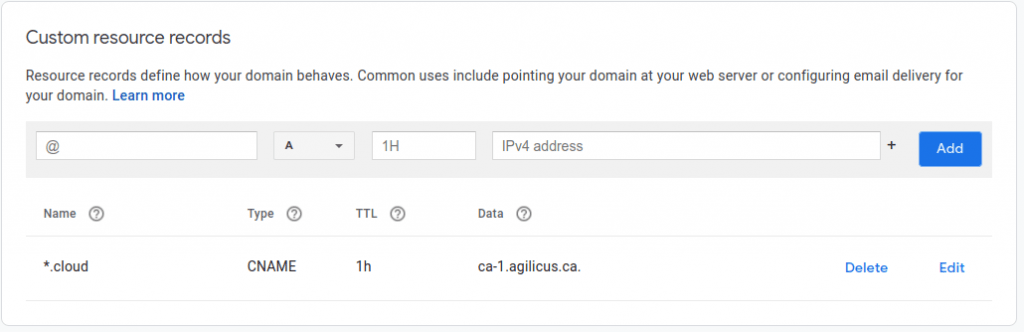
For the domain, if you choose to provide your own sub-domain, you must first put an entry in your Domain Name Server (DNS) to prove you own it, and to allow us to host content on it. This is done by creating a CNAME record with a wildcard. In your DNS, create a CNAME report from *.subdomain.yourdomain to ca-1.agilicus.ca. For more information about the Hows and Whys of a CNAME, see “Internet Redirect & Alias: The CNAME“. NOTE: this is a wildcard.
For example, we recommend using “cloud” as the subdomain. If your company web-page is “www.example.com”, you will create a CNAME of *.cloud.example.com, pointing to ca-1.agilicus.ca. You and your users will now be accessing applications as https://appname.cloud.example.com/.
If you use a domain we supply, this can be very quick for you to get going. If you use your existing domain its simpler for your users, and, can help train them to avoid spearphishing by only using your corporate domain. The choice is yours.
An example setup using Google DNS is shown. This will vary slightly depending on your DNS provider. If you wish to test the setup of your CNAME, we recommend using dig, as below. You may also use a web-based service such as dnslookup.online. Lookup anyname.subdomain.yourdomain.
$ dig -t cname foo.cloud.zero-trust.ca ... ;; QUESTION SECTION: ;foo.cloud.zero-trust.ca. IN CNAME ;; ANSWER SECTION: foo.cloud.zero-trust.ca. 3600 IN CNAME ca-1.agilicus.ca.
Once you select CREATE it will take approximately 30-60 seconds to setup an environment. During this time our system is created a Federated Login system (allowing authentication against your Identity Providers), SSL certificates (100% of what we do is encrypted), and some other database setup for Audit Logging etc.
NOTE: Split-Horizon DNS
If you run split-horizon DNS (e.g. a name server internally which serves different answers than externally), you will need to make the same changes in both systems. This can happen e.g. if you use Microsoft Active Directory on premise as a DNS server, and a public DNS server externally.
NOTE: Testing
You may test your newly added CNAME using an Agilicus API. In your browser, navigate to:’https://api.agilicus.com/v1/resolve/?type=CNAME&name=auth.SUBDOMAIN.DOMAIN‘. So, for example, if you chose ‘cloud’ as the subdomain, and your main domain was ‘mycompany.com’, you would openhttps://api.agilicus.com/v1/resolve/?type=CNAME&name=auth.cloud.mycompany.comThis will return some text like:
{“AA”:false,”AD”:false,”Answer”:[],”Authority”:[{“data”:”ns71.domaincontrol.com. dns.jomax.net. 2019051401 28800 7200 604800 600″,”name”:”mycompany.com.”,”type”:6}],”CD”:false,”Flags”:[“QR”,”RD”,”RA”],”QR”:true,”Question”:[{“name”:”auth.cloud.dsai.mycompany.com.”,”type”:5}],”RA”:true,”RD”:true,”Responder”:”8.8.4.4″,”Status”:3,”TC”:false}You may also use a tool such as dig:dig -t cname auth.dbt.agilicus.cloud
; <<>> DiG 9.16.15-Ubuntu <<>> -t cname auth.dbt.agilicus.cloud
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15521
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;auth.dbt.agilicus.cloud. IN CNAME
;; ANSWER SECTION:auth.dbt.agilicus.cloud. 1800 IN CNAME ca-1.agilicus.ca.;; Query time: 168 msec
;; SERVER: 127.0.0.53#53(127.0.0.53)
;; WHEN: Sun Oct 17 18:24:14 EDT 2021
;; MSG SIZE rcvd: 82