Zero Trust
Overview
Zero-Trust security. Switch from a perimeter-based (firewall and VPN) model of access to a user to resource model.
Implement strong, simple identity. Identity for both a person, but also a system. Decouple the identity from the corporation: make it affinitive to the user, a single identity.
Enforce entitlements and authorisation in the network.
This micro-segmentation is simpler to use, more accessible, and, more secure. It reduces the lateral-traversal, it empowers the users, it increases the audit capability. And, its more economical, more scalable. Everybody wins.
Articles
-
10 Billion Reasons Shared Passwords Are Bad: RockYou2024
Shared password bad. 10 billion passwords leaked. Your team installed some shadow IT remote access solution with a shared password.
-
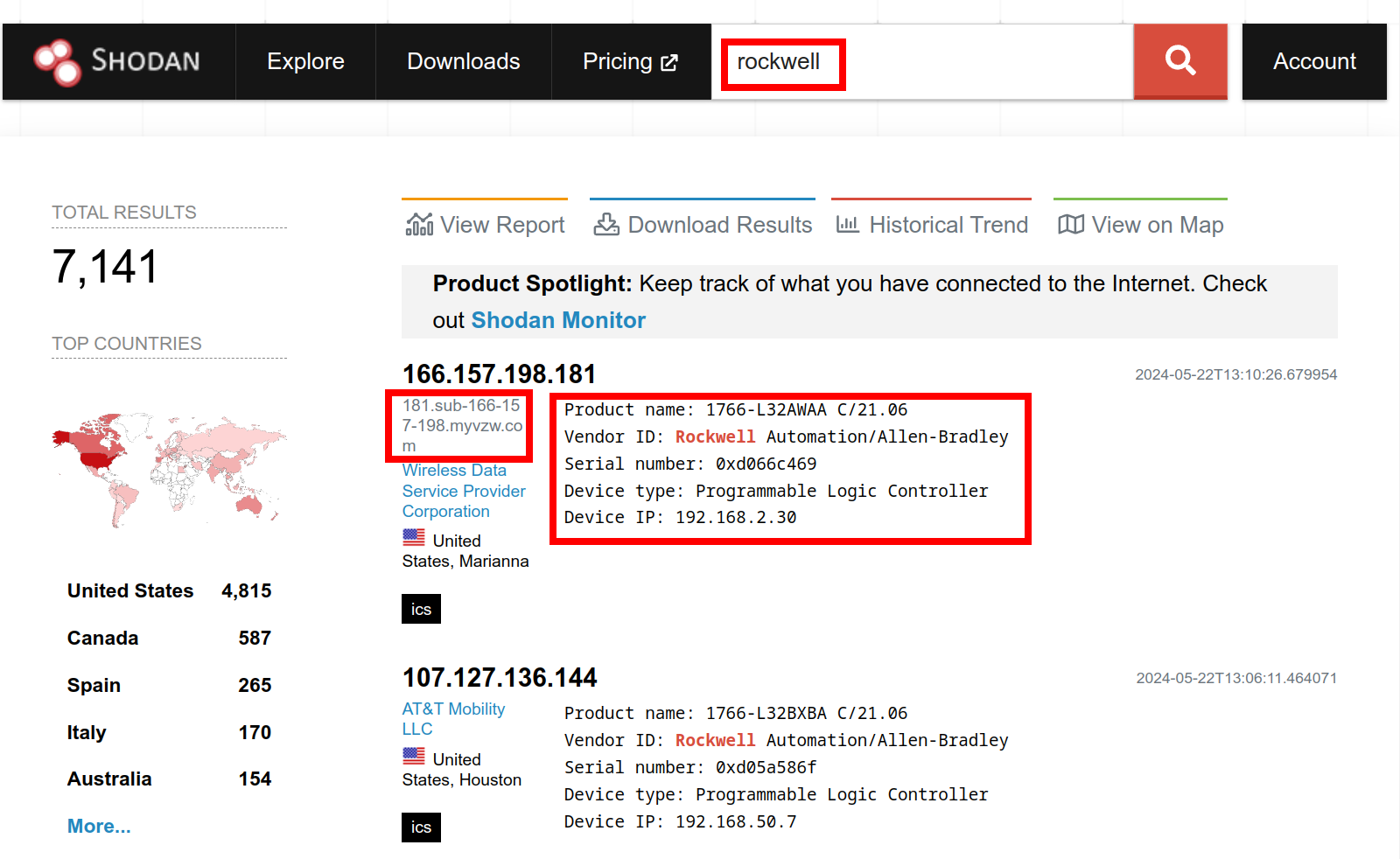
Get Thee From BGP Rockwell: Ethernet/IP Is not Internet
You wouldn’t download a PLC, would you? Rockwell Automation alert on public access to PLC, and a Shodan search to fact check it.
-

Begone Ivanti Industrial VPN Sayeth CISA
ED 24-01 directs agencies to instantly remove Ivanti Industrial VPN from industrial operations. Defence In Depth, Zero Trust give you more time to react.
-

Using Zero Trust to Enable Secure Remote Access to SCADA for Water Systems
This blog post explores the challenges of securing remote access to SCADA systems and how Zero Trust can act as a solution.
-

Zero Trust vs. VPN: A Comprehensive Comparison for Secure Remote Access
In this blog post, we’ll dive into the Zero Trust vs. VPN security model differences and why the former is ultimately the far superior choice for secure, seamless remote access.
-

SSH for Remote Access: Every User, Every Device, Every Application
In this blog post, we’ll delve into the challenges of enabling SSH for remote access and how you can do so without compromising security through Zero Trust.
-
Simplifying Secure Access: Enabling Rockwell Automation Remote PLC Access Without a VPN
In this post, we’ll explore the limitations of VPNs and delve into how to enable VPN-less Rockwell Automation remote PLC access.
-
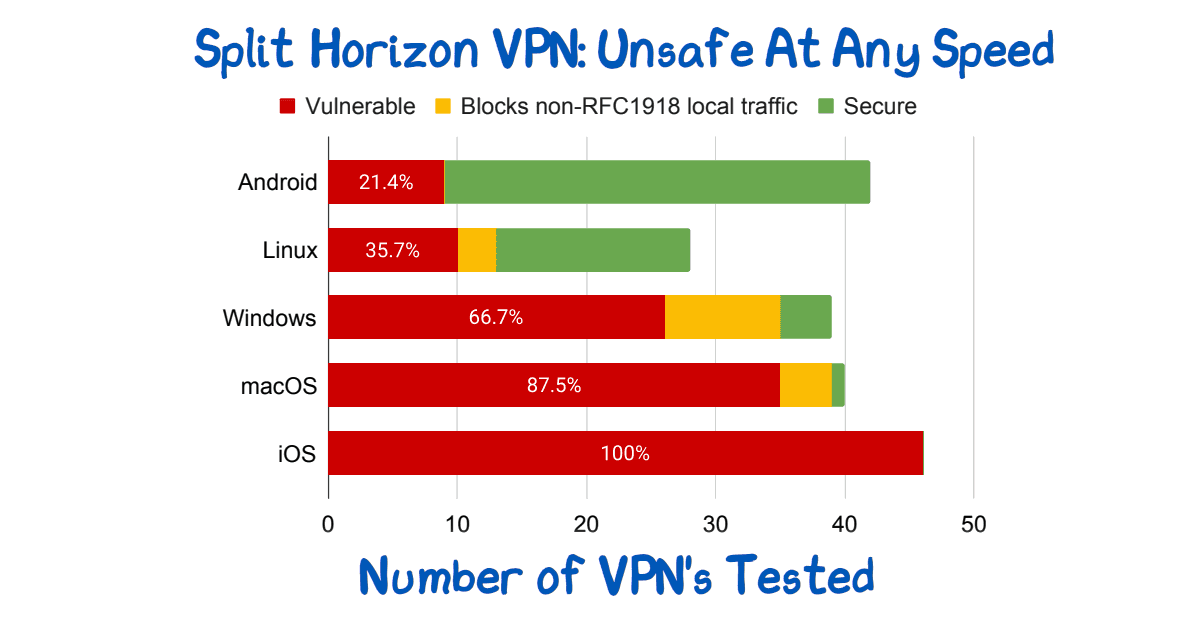
Split Horizon VPN: Unsafe At Any Speed
Split Horizon VPN’s are used to avoid breaking video conferencing. They are unsafe. See paper for route injection issues.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-

The Security Risks of Using VPNs in Water and Wastewater Facilities
What are the risks of using VPNs in water and wastewater facilities? We’ll help you answer that question and understand what to do instead.
-

The Security Risks of Using Shared Credentials in Water and Wastewater Facilities
There are many security risks of using shared credentials in water and wastewater facilities. Here’s why you should eliminate them and how to do it.
-
Zero Trust Troika: The Who, The What, The How
Perimeter security approaches are no longer effective. A Zero Trust Network Architecture is a powerful, modern way to protect your network from cyber attacks.
-

Strengthen Your Industrial Network Cybersecurity with Vendor Access Management
Securing your third-party vendors can help reduce the cyber risk to your control systems and improve overall industrial network cybersecurity.
-

Understanding the CISA Zero Trust Maturity Model: A Framework to Improve Your Security Posture
This article will give you an overview of the CISA Zero Trust Maturity Model, the changes made in Version 2.0, and how it can benefit your organization.
-

The Zero Trust Roadmap: Understanding NIST 800-207 and How to Align With It
This article will give you an overview of NIST 800-207 and the different ways your organization can implement Zero Trust to meet the guidelines.
-
Best Practices In Vendor Privileged Access Management
Vendor privileged access management best practices: Access control, strong, unified authentication, fine-audit, secure access.
-

Identity Provider Versus Single-Sign-On
Single-Sign-On and Identity Providers are often treated as the same. But, the IdP facilitates the SSO. You can have multiple IdP if desired.
-

Who Are You? Prove It! Identity Versus Authentication
Identity vs Authentication. Who are you. Prove it. Related but different concepts. Ensure your IdP does not give identity when it realy means authentication.
-
Another Day, Another Exploit – Protecting Against the ProxyNotShell Exchange Server Zero-Day Vulnerability
Learn how zero trust protects against the new Microsoft Exchange Server zero-day exploit affecting Outlook Web Access (OWA), ProxyNotShell. With Agilicus, you’ll block lateral traversal and prevent unauthorised traffic from arriving at your resources while ensuring they are still accessible to legitimate users.
-

Well Timed or Coincidental, Cue the Phishing Attacks as 2.5M Students Affected by Data Breach
Days after announcing student loan forgiveness in the United States, 2.5 million student borrowers had their personal information exposed in a data breach and are at an increased risk of being targeted in a phishing attack.
-

Protecting Against the OWASP Top 10 Web Application Vulnerabilities
The OWASP Top 10 is a standard awareness document that outlines the most critical web application security risks and vulnerabilities. Learn how Agilicus AnyX is designed to eliminate an attacker’s visibility into the potential OWASP Top 10 web application vulnerabilities.
-

Industrial Air Gap – A Tale Of 2 Users
Industrial devices are hard to secure. Commonly done only via direct local access. Teams, however, wish remote access to improve efficiency. A solution to this battle is Zero Trust.
-

Top 5 Cybersecurity Resolutions to Cross off Your List in 2022
Cybercriminals had a record year, the cost of a breach reached new highs in 2021. With clear cybersecurity goals, businesses avoid becoming a news headline.
-

NIST sp 800-63A: Introduce Yourself
Who are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-
NIST sp 800-63B: How Well Do I Know You?
Zero-Trust Network Architecture has 3 steps: Authenticate (Who), Authorise(What), Access(How). 3 Levels of strength of the who are defined in NIST sp 800-63B. Does the goldilocks principle apply to you? Read on!
-
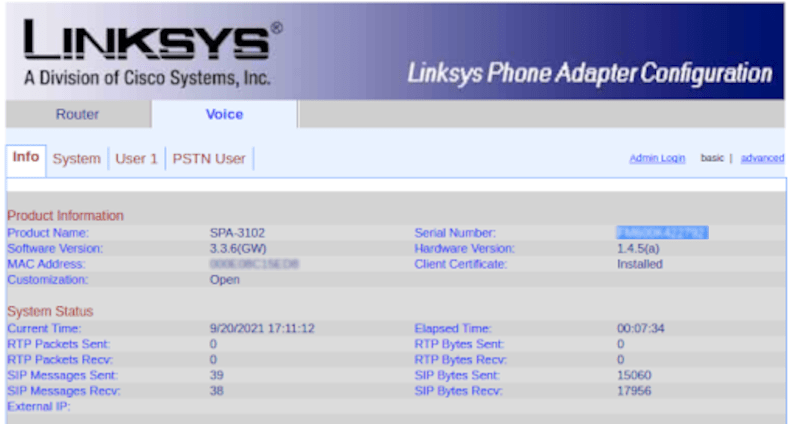
Zero-Trust Remote Access to Fix VoIP DDoS
Reconfigure a VoIP PSTN gateway remotely via Zero Trust with Multi-Factor Authentication and single-sign-on to avoid a DDoS.
-

Authentication, Authorisation, and API Keys
e encouraged to create API keys by many SaaS tools, and, these present real authorisation challenges.
-
Mind the gap between the web app and the desktop
We want a web app. We have a desktop. Use zero-trust to make any desktop available to any device without a VPN.
-

A ’round tuit’ to get your internal web apps available
You have an internal tool. Grafana, Prometheus, …. You get an alert, its via Slack, Chat, etc. You click. The link goes nowhere. You curse. We fix!
-
The Pipeline Ransomware Came Via The VPN
A criminal group takes over a nations energy via a VPN. Its time to treat the VPN as a risk, not a security solution. Zero Trust is better.