Concepts
A Network Resource is an arbitrary network IP address and port. This might be a Remote Desktop, a Database, an ERP system. Typical access control is done via network access control lists. To expand this via cryptographic-based zero-trust networking, the Agilicus system can expose the Network Resource via a Connector and then provide authentication and authorisation based security on it onwards to other users or systems.
A common use case for Forwarding is a need to have a Network Resource available from one site to another. As an example, consider a small company. It has two offices. Each office has a typical small business router and a few staff. One of the sites runs a database which is used by a desktop application.
In this case, consider the following approach:
- Install Connector on site with database (on the database server or another)
- Install Connector on site needing access (on the desktop running the application, or another)
- Create a Network Resource for the database. Attach it to the proper Connector
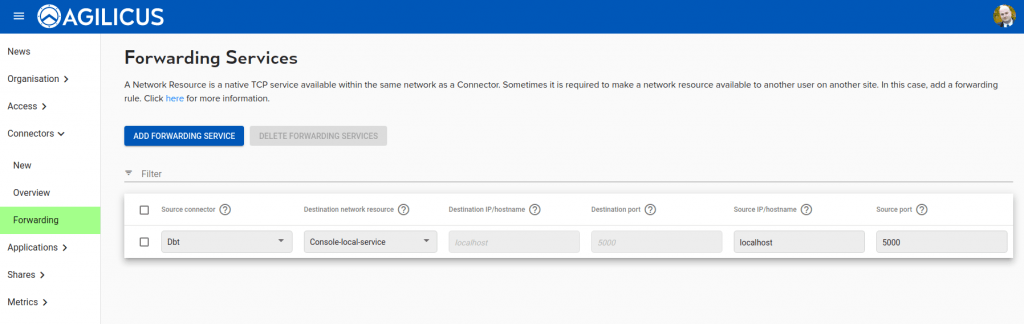
- Create a Forwarding Resource on the site needing access. Join the two.
You will be asked a few questions:
- destination IP/hostname. This is the hostname or IP as resolvable by the connector installed on the site with the database. It will typically be the same as you would enter in your desktop application.
- destination Port. Same as 1
- Source IP/hostname. This is typically left blank(all), meaning the host with the connector will allow any local network host to use it. If you wish to lock it down to the local desktop consider entering ‘localhost’ here. By default this is ‘localhost’ (meaning the application wishing to connect must run on the same host as the Connector). You may change this to ‘0.0.0.0’ (meaning any host in the same network may connect.
- Source Port. This is typically left blank (meaning same as destination). In some environments you may wish to use a different port here (for example, if the destination port is privileged, <1024, since the Connector runs unprivileged, you may e.g. use 80 for the destination port and 8080 for the source port)
Want Assistance?
The Agilicus team is here for you. The ‘Chat‘ icon in the lower left, here, or in the administrative web page, goes to our team.
Or, feel free to email support@agilicus.com
Not yet a customer? The TRY NOW button will walk you through the process.