Agilicus Connector Kubernetes Install
The Kubernetes install is intended for advanced usage only. It is for users who are integrating with a larger system. As a pre-requisite, you will need kubectl installed on the machine you will do the installation from.
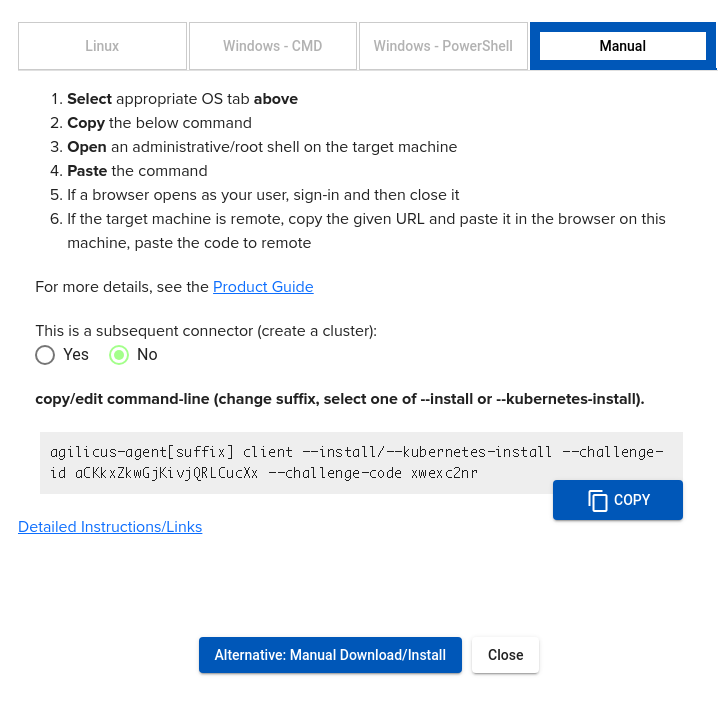
The steps initially are similar:
- Create a new Connector in admin
- Select “Install’
- Download the binary (using the alternative manual install, see link for all binaries etc)
- Select ‘Manual’. Change –install/–kubernetes-install to –kubernetes-install. Adjust other parameters as needed
- The command will output as below.
- Inspect the generated YAML, adjust if necessary
- Installl with kubectl apply
$ agilicus-agent client --kubernetes-install --challenge-id XXXXXX --challenge-code XXXXXX
INFO[2023-05-30T18:26:47-04:00] Starting connector - version v0.200.6
INFO[2023-05-30T18:27:00-04:00] creating connector instance
INFO[2023-05-30T18:27:01-04:00] Join a connector cluster
INFO[2023-05-30T18:27:01-04:00] Output Kubernetes YAML
INFO[2023-05-30T18:27:01-04:00] Now run:
kubectl apply -f /tmp/agilicus-agent-921551629/agilicus-agent.yaml && rm -rf /tmp/agilicus-agent-921551629
INFO[2023-05-30T18:27:01-04:00]
INFO[2023-05-30T18:27:01-04:00] Installation Complete
INFO[2023-05-30T18:27:01-04:00]Theory of Operation
A small (1G) PVC will be created. This will hold the small amount of configuration (service account updates)
When creating network services, use the same name service resolution you would normally use in Kubernetes (e.g. SERVICE.NAMESPACE)
A Deployment will be created with replicas=1