AnyX Guide Topic: connector
-

WAGO Edge Controller
The WAGO Edge Controller is a flexible and open control platform for many embedded and industrial applications. It provides an excellent vantage point to run the Agilicus Connector.
-

Agilicus Connector – NanoPI R2S
NanoPI R2S Simple Embedded System with Agilicus Connector NanoPi R2S Background The NanoPI R5S has 2 x Gigabit Ethernet, 1GiB of RAM, and 32GB of eMMC storage. With its large passive heatsink it is an ideal platform to use as a small router. It also makes an ideal platform to run the Agilicus Connector. The…
-

Phoenix Contact PLCnext AXC F 2152
Install the Agilicus connector directly on the Phoenix Contact PLCnext for highest security and simplest deployment.
-

Agilicus Connector – Container/Docker
Install an Agilicus Connector in a container (e.g. Docker)
-

Agilicus Connector Sign-In
The Agilicus Connector creates a service account on installation, bootstrapped via a browser from the Administrator who is installing it.
-

Agilicus Connector – Microsoft Windows
Install and diagnose the Agilicus Connector on Microsoft Windows
-
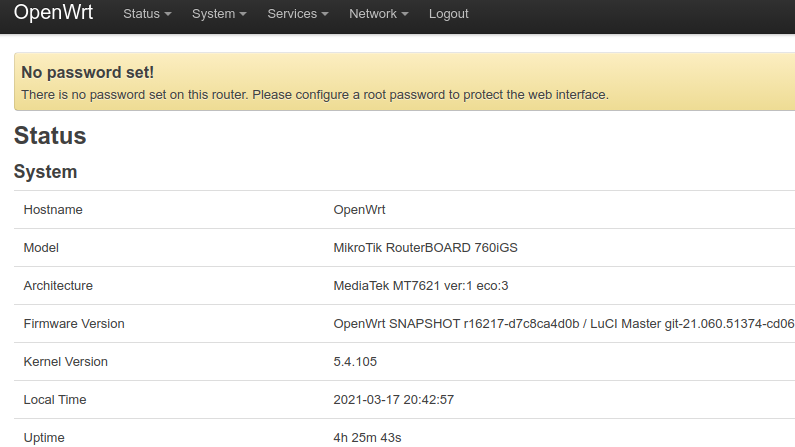
OpenWRT Connector Install
Configure an OpenWRT Router with the Agilicus Agent Connector.
-

Agilicus Connector Mikrotik Router
The MikroTik RB5009UG+S+IN is a small-form factor router. it is a good vantage point to run the Agilicus Connector. Agilicus Connector Mikrotik Router
-
Agilicus Connector Kubernetes
The Agilicus Connector includes a standard container-runtime and automatic installation for Kubernetes. This allows exposing internal Kubernetes services with an OpenID Conect Identity Proxy. Agilicus Connector Kubernetes
-

Connector Install: Ubiquiti EdgeRouter X
The Ubiquiti EdgeRouter X (ER-X/ER-X SFP) is a small-form factor router. it is a good vantage point to run the Agilicus Agent Connector.
-
Agilicus Connector in Private VPC In AWS EC2
Private IP only in your VPC? Need to ssh or remote desktop or share some files? This example shows a setup.
-
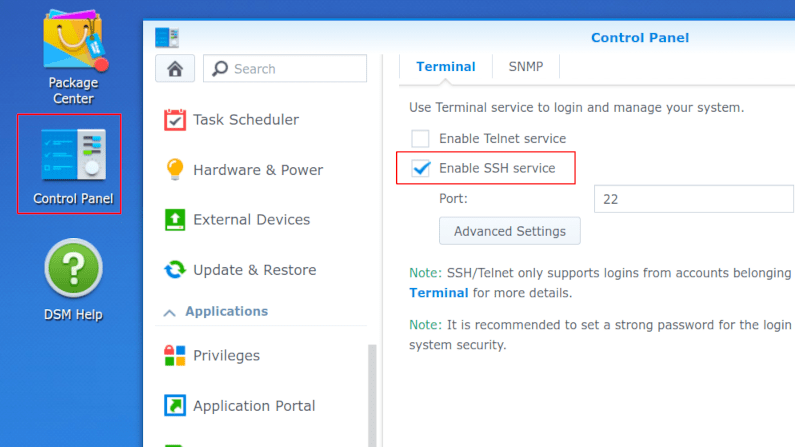
Synology Connector Install
Configure a Synology NAS with the Agilicus Agent Connector.
-

Agilicus Connector Windows Cluster
Install the Agilicus Connector to be high-availability in a Microsoft environment.
-

Linux, FreeBSD, Embedded Connector Install
The instructions to install the Agilicus Agent Connector are nearly identical on various Unix operating systems. This includes desktops, servers, and embedded devices.
-
Sample Ubiquiti EdgeRouter-X EdgeMax Web Interface
Sample Ubiquiti EdgeRouter-X EdgeMax Web Interface
-
Connector Install: Raspberry Pi
The Raspberry Pi makes an excellent platform to install the Agilicus Agent Connector. See the general instructions here.
-

Connector Install: Netgate SG-1100 pfSense
The Netgate SG-1100 pfSense is a small-form factor router. it is a good vantage point to run the Agilicus Agent Connector.
-

Agilicus Connector – NanoPI R5S
Install an Agilicus Connector on an OpenWRT-based NanoPi R5S.
-
Agilicus Connector
The Agilicus Connector facilitates connectivity from a private site to external users.
-

Moxa UC-8200 Zero-Trust Connector Install
Moxa UC-8200 Zero-Trust. Configure a Moxa UC-8200 Industrial PC with the Agilicus Agent Connector.
-

Agilicus Connector – Export Certificate
Have a local resource that should be properly TLS encrypted and publicly trusted certificate? The Agilicus Connector can facilitate this.
-
Sample: Synology Local SSL
No more snake-oil self-signed certificates, even on local lan. Let Agilicus AnyX connector automate the task.
-

Cisco IOx Zero Trust Connector Install
Cisco IOx Zero Trust . Configure a Cisco IR1101 IOx with Agilicus Connector. Zero Trust Remote Access to it, to IoT beyond it.
-

Agilicus Connector – Snap
Install an Agilicus Connector on a Snap-based Ubuntu Core system. Agilicus Connector – Snap
-

Agilicus Connector – GL-MT3000 (Beryl AX)
Install an Agilicus Connector on an OpenWRT-based GL-MT3000 Beryl AX
-

Agilicus Connector High Availability
Install and Operate the Agilicus Connector in a high-availability, high-resilience mode.
-

Agilicus Connector Air Gap Machine With Containers
Setup a host firewall to create a virtual airgap on a Linux machine running containers with the Agilicus connector.