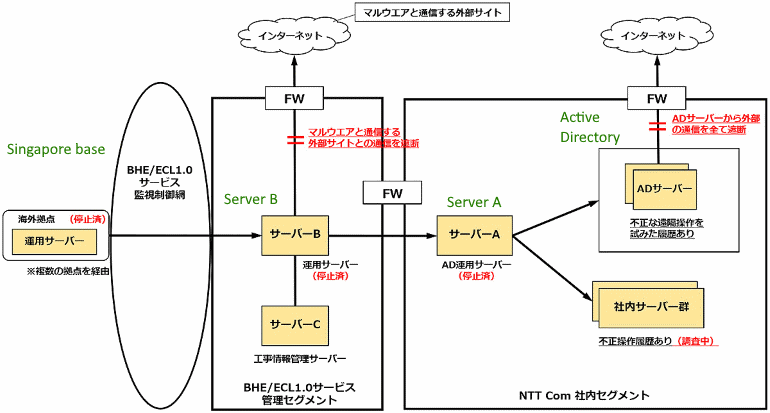
The Japanese communications giant NTT disclosed they had been breached. I’ve taken the liberty of translating their diagram (above), with their original below.
You can see what happened, some malware wiggled in to a development server on a remote network. It then wandered into the production Active Directory server in the main network. It was able to do this because firewalls are actually very trusting, typically just allowing all internal traffic.
If we operated a Zero-Trust model, we would treat all of these servers as if they were on the public Internet. We would have re-thought the use of a firewall, and, instead, used identity-based connection management. It is not a panacea, it doesn’t fix everything. But it really helps lower collateral damage through east-west traversal.