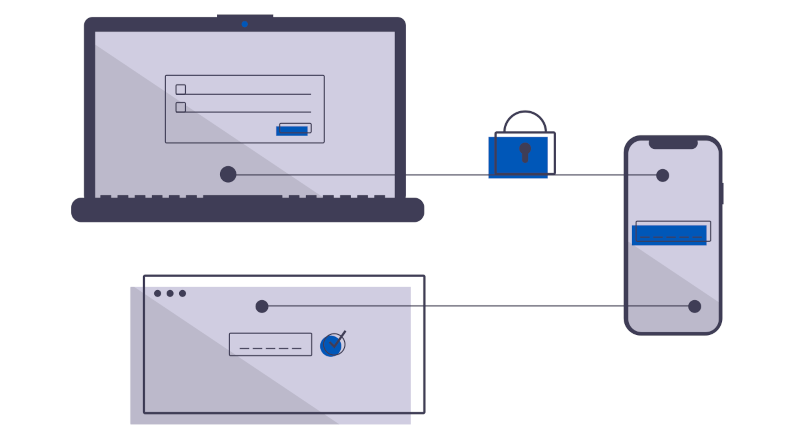
Your cyber insurance is up for review. If you can get all applications authenticated with multi-factor, you can afford it. But, you have only managed to get the new ones done, leaving the miscellaneous. Let’s talk about how an authenticating proxy can get the rest done, with no work, no fuss. Become compliant right quick.
Learn More?
Recent Articles
-
Pwned Plans and Porous Perimeters
-
Porous Perimeters and Pro-Russian Pwning: The La Poste Lesson
-
Ransomware Reservoirs: Another Leak in the Critical Infrastructure Dam
-
The Fragility of Interdependence: Securing the Industrial Mesh
-
2026 Pwned by Progress: The Year Your Air Gap Finally Evaporates
-
Same Old Shenanigans: The MITRE 2025 Top 25 List