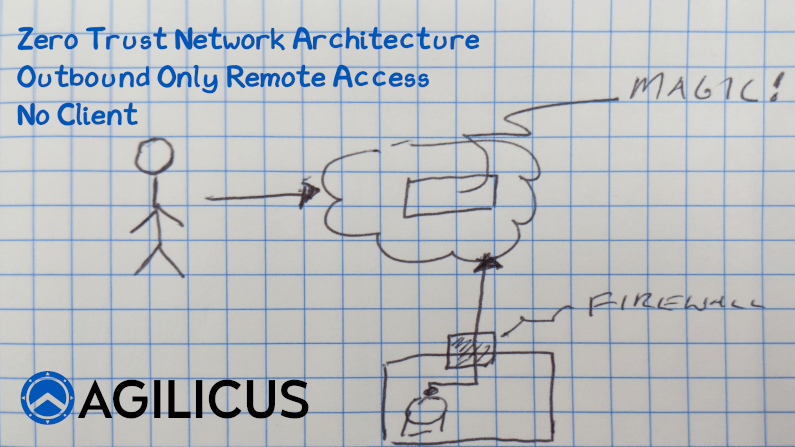
Zero Trust Network Access. The principle of managing security between a user and a resource, rather than a user and a perimeter. By Identifying the user, providing Authorisation in the network, and then remote access to individual resources, we increase security and simplify at the same time. But, did you know you can do this with 0 inbound connections open? Nothing. No ports open to see on a pentest, on nmap, on Shodan. How? In this video I explain. In a nutshell, the resource makes a permanent outbound connection to the cloud. The user makes an outbound connection to the same cloud. Identity is confirmed, Authorisation is confirmed. The connections are stitched together. Simple and secure, no reconfiguration of firewalls. No client VPN software.
Learn More?
Recent Articles
-
Pwned Plans and Porous Perimeters
-
Porous Perimeters and Pro-Russian Pwning: The La Poste Lesson
-
Ransomware Reservoirs: Another Leak in the Critical Infrastructure Dam
-
The Fragility of Interdependence: Securing the Industrial Mesh
-
2026 Pwned by Progress: The Year Your Air Gap Finally Evaporates
-
Same Old Shenanigans: The MITRE 2025 Top 25 List