
Securing the Distributed Supply Chain: Why Identity is the New Air Gap
As Industry 4.0 dissolves the traditional network perimeter, discover why a Zero Trust Architecture makes identity the essential new air gap for securing the distributed global supply chain.
Executive Summary
The manufacturing industry has evolved from vertically integrated giants into a complex, distributed ecosystem defined by specialisation and Just-In-Time principles. This shift to Industry 4.0 brings unprecedented interconnectedness but exposes critical security vulnerabilities. As distinct corporations share digital and physical spaces, legacy access models like VPNs and Jump Boxes have become dangerous liabilities, acting as single points of failure that can cascade into system-wide crises — as evidenced by major incidents at Jaguar Land Rover and Colonial Pipeline.
This whitepaper argues that the traditional “air gap” is obsolete. To secure this fragile, interdependent supply chain, organizations must adopt a Zero Trust Architecture where security is decoupled from network location and anchored in identity.
Key Strategic Insights
- The Identity Imperative: In a world where physical isolation is a myth, identity is the new perimeter. Security must shift to a “never trust, always verify” model, utilising unified Single Sign-On to authenticate every user — employee or third-party vendor — individually.
- Surgical Authorisation: Replace “all-or-nothing” network access with granular, task-specific permissions. Zero Trust ensures users access only the specific resources they need (e.g., reading a sensor vs. programming a PLC), strictly containing potential breaches.
- Operational & Business Impact: Implementing an identity-centric model requires no changes to existing network topology and simplifies firewall management. Beyond security, it delivers quantifiable business value:
- Risk Reduction: Enables qualification for cyber insurance and compliance with new regulatory standards (e.g., SEC rules).
- Efficiency: Reduces Mean Time To Repair by streamlining secure remote access for third-party experts, directly protecting revenue and uptime.
Conclusion
As manufacturing embraces AI and IIoT, the reliance on system-to-system and cloud connectivity will only grow. Clinging to outdated perimeter defenses is a strategic risk. The future of industrial security lies in accepting that identity is the new air gap, ensuring resilience in a hyper-connected automated world.
Introduction
The manufacturing landscape is undergoing a profound transformation. Gone are the days of vertically integrated giants like the Ford Rouge River plant, a monolithic entity consuming raw materials at one end and extruding finished goods at the other. Today, economic specialisation has fragmented production into a complex web of sub-assemblies and components, sourced from a multitude of specialised companies. This intricate dance of distinct corporations, often sharing physical space but always distinct in staff and systems, is the new reality. Fuelled by Just-In-Time (JIT) manufacturing, this shift demands minimal inventory, turning any hiccup in one part of the chain into a system-wide crisis.
This new paradigm, often referred to as Industry 4.0, introduces unprecedented technical complexities. Industrial control systems are becoming more sophisticated, and the integration of MES and ERP systems is tighter than ever. Yet, the security models underpinning this interconnected ecosystem are dangerously outdated. Remote access, a critical enabler for specialised support in this distributed world, often relies on practices that are fundamentally insecure, creating vulnerabilities that compromise the entire supply chain.This white paper will dissect these challenges, exposing the critical friction points in a distributed manufacturing environment. We will examine how legacy access models, such as broad VPNs and archaic JumpBoxes, create unacceptable risk. Drawing lessons from real-world incidents like the Jaguar Land Rover cyberattack and the Colonial Pipeline ransomware attack, we will illustrate the catastrophic consequences of these flawed approaches. Finally, we will present a compelling case for a Zero Trust Architecture, demonstrating how an identity-centric security model is not just a best practice, but an absolute imperative. In an age where physical isolation is a myth, identity is the new air gap.
The Friction of Industry 4.0
The era of the self-contained industrial behemoth, best exemplified by the Ford Rouge River plant, is firmly in the past. This historical model, where raw materials entered one end and finished automobiles emerged from the other under a single corporate roof, defined a period of vertical integration and centralised control. It was simple, if inflexible.
Today’s manufacturing landscape tells a different story, driven by the economic theory of specialisation. Instead of monolithic production, we see a global network of companies, each excelling in a specific sub-assembly or component. This shift has fragmented the supply chain into an intricate web of distinct corporations, often collaborating closely – sometimes even under the same physical roof – yet always operating with separate staff, systems, and distinct corporate identities.Layered onto this specialisation is the relentless pressure of Just-In-Time (Lean) manufacturing. These principles, designed to maximise efficiency and minimise warehousing costs, demand extremely lean inventories. This means any disruption, no matter how minor, in one specialised node of the supply chain immediately cascades. A single component delay, a minor operational glitch, or a localised shutdown can bring an entire production line to a grinding halt, turning localised friction into widespread operational fragility.
The Evolution of Manufacturing Economics
The rise of Industry 4.0, while promising unprecedented efficiencies through automation and data exchange, also introduces critical friction points into this increasingly distributed manufacturing ecosystem. The very technologies designed to optimise production often create new vectors for vulnerability if not secured with a forward-thinking approach.
At its core, Industry 4.0 drives the increased use and complexity of industrial control systems. These are the operational backbone of modern factories, but their sophistication often outpaces the security models protecting them. Concurrently, shared systems like Manufacturing Execution Systems (MES) and Enterprise Resource Planning (ERP) are becoming more tightly integrated across disparate corporate entities. This tight coupling creates a fundamental challenge: separate companies, often operating from separate physical sites, need seamless access to shared data and controls. The result is an identity crisis where user authentication, originating from distinct systems, often devolves into insecure practices. This manifests as either a cybersecurity nightmare of “shared” accounts – a single point of failure and untraceable actions – or VPNs that grant overly broad access, effectively sharing far too much risk.
The tight inventory control inherent in Just-In-Time manufacturing means that any downtime at one node sends ripples throughout the entire supply chain. This amplifies the need for rapid incident response and specialised support. However, the increased complexity of industrial control systems demands highly specialised skills– expertise that smaller, individual players in the fragmented supply chain often cannot afford to retain directly or have on-site. The solution, invariably, is secure remote access for a wider array of third-party system integrators, control system vendors, and specialised consultants. Their ability to quickly diagnose and repair issues remotely becomes paramount, directly impacting Mean Time To Repair and, by extension, the continuity of the entire manufacturing operation.
The Failure of Legacy Access Models
The critical need for remote access, coupled with the inherent complexities of distributed manufacturing, has exposed the dangerous inadequacies of legacy security practices. These outdated approaches, often born from a simpler era, are now creating gaping vulnerabilities that can cripple entire enterprises.
Two classic examples of insecure remote access methods continue to plague industrial environments: the Jump Box and the broad-stroke VPN. A Jump Box, frequently implemented via remote desktop solutions like TeamViewer, acts as a dual-homed device that bridges networks. Its fundamental flaw lies in its “all or nothing” access model: if an attacker gains control of the JumpBox, they effectively gain full, unfettered access to everything it can reach. There is no fine-grained authorisation; simply put, access to the box means access to the kingdom. Similarly, a traditional VPN operates as a Layer-3 device, merely joining two networks. Once a user (or an attacker with compromised credentials) is “on” the VPN, they are inside the network perimeter, free to access anything within that segment. Both methods create an enormous attack surface, offering lateral movement to adversaries and making granular control an impossibility.The consequences of these flawed models are not theoretical; they are costly and disruptive realities for modern manufacturers. Consider the Jaguar Land Rover cyberattack, which brought down the entire enterprise, idling not only their core production but also their loosely affiliated dealer networks and extended supply chain. The ripple effect of a single breach demonstrates the extreme fragility of interconnected systems protected by inadequate security. Even more stark was the Colonial Pipeline ransomware attack. In this case, a compromised vendor VPN credential provided the entry point into critical operational technology networks. The vendor, in sharing risk through an overly permissive VPN, inadvertently caused a full outage of a vital national energy infrastructure – a clear illustration of how a seemingly isolated third-party access point can cascade into a crisis of national scope. These incidents underscore the perilous truth about Industrial Control Systems like PLCs: they are often “infinitely insecure things with an infinitely important role in uptime,” a combination that represents a catastrophic risk when exposed through legacy access methods.
The Zero Trust Architecture Solution
In the face of cascading cyber risks and the inherent fragility of legacy access models, a fundamental paradigm shift is not merely advisable – it is imperative. The solution lies in adopting a Zero Trust Architecture, a security model that fundamentally rejects the implicit trust once granted to devices or users within a network perimeter. Instead, Zero Trust operates on the principle of “never trust, always verify,” treating every access request as if it originates from an untrusted network.
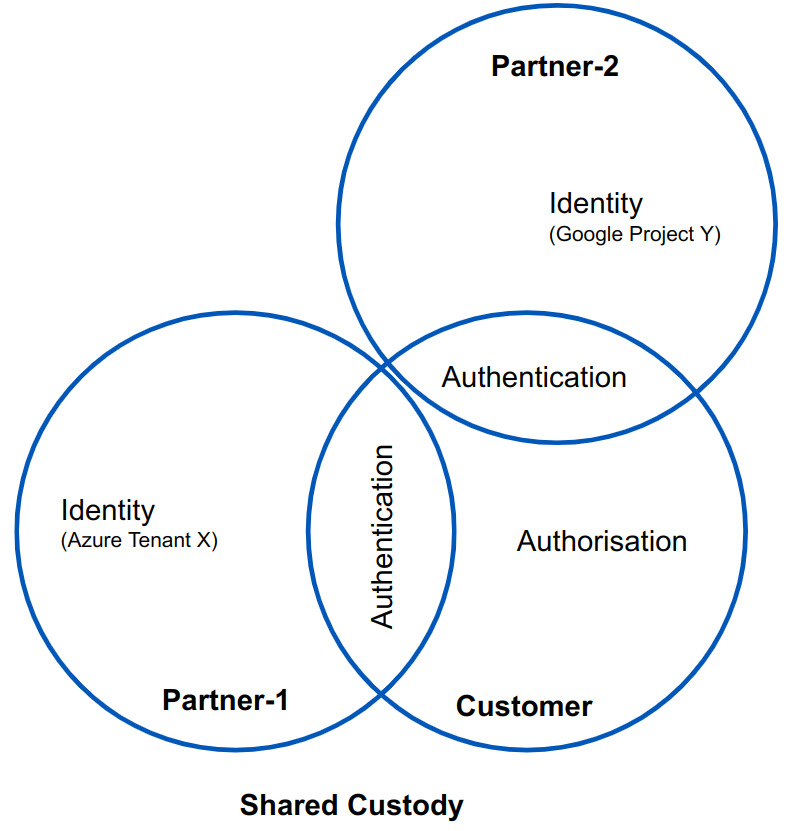
At the core of a robust Zero Trust solution are principles designed for the intricate, multi-party reality of distributed manufacturing. First, identity is paramount. This means moving beyond shared accounts and broad network access to unified authentication, where each user – regardless of their corporate affiliation – signs in as an individual with single-sign-on. This not only reduces the risk profile by eliminating anonymous access but also streamlines management; as teams churn within collaborating companies, there’s no need for complex notification protocols across the web of interconnection.
Second, authorisation must be surgical. The blunt instruments of VPNs and JumpBoxes are replaced with precise, granular permissions. A user, for instance, might be granted read-only access to a specific Human-Machine Interface at Site 3, but explicitly denied any access to the underlying PLC programming interface. This level of control ensures that access is strictly limited to the necessary resources for a specific task, effectively containing any potential breach. Furthermore, a truly Zero Trust model provides fine-grained auditing, creating an immutable log of who performed what action, when, and from where – a stark contrast to the opaque logging of shared accounts or broad VPN sessions.
Beyond its formidable security posture, a well-implemented Zero Trust solution, such as Agilicus AnyX, delivers significant operational simplicity. Critically, it demands no changes to existing network infrastructure or topology. Its identity-aware proxy integrates seamlessly without requiring costly and disruptive re-architecting. The adoption of outbound-only connections simplifies firewall management dramatically, enabling organisations to delete complex inbound rules in favor of a straightforward “block all inbound” policy. Finally, from an end-user perspective, the solution is clientless, requiring only a standard web browser. This is particularly transformative for engaging third-party vendors, as it eliminates the need to enforce software installations on their devices, reducing friction and accelerating support turnaround.
Business Impact and ROI
The shift to Zero Trust is not merely a technical upgrade; it is a strategic business enabler with quantifiable returns. The benefits extend far beyond the IT department, delivering value to the boardroom, the factory floor, and the compliance office.
A compelling illustration of this impact is seen in the case of ACME Manufacturing. Facing challenges similar to many in the industry – a distributed multi-site footprint and reliance on third-party support – ACME implemented Agilicus AnyX to transform its security posture. The results were immediate and strategic. Previously, the company was unable to secure cyber insurance coverage for its critical SAP business system due to the risks associated with third-party VPN access lacking multi-factor authentication. By implementing a Zero Trust model with enforced multi-factor authentication for all users, regardless of origin, ACME not only qualified for coverage but also satisfied a key Board of Directors mandate for improved risk governance. This shift freed up valuable management time previously consumed by manual compliance checks and anxious risk assessments.Furthermore, the operational gains were tangible. In an industry where minutes of downtime translate to substantial revenue loss, speed is currency. ACME reported a 17% reduction in Mean Time To Repair following the implementation. This efficiency gain was directly attributed to the streamlined access provided to third-party vendors. By removing the friction of VPN clients and complex login hurdles, support staff could diagnose and resolve issues faster. Additionally, by mitigating the risk of ransomware through strict, identity-based access controls, ACME aligned itself with new SEC cybersecurity reporting rules, turning a regulatory burden into a proof point of operational resilience. In this context, security is no longer a cost center; it is a competitive advantage that protects uptime and ensures business continuity.
Conclusion: The Future of Industrial Security
As we look toward the horizon, the trajectory of manufacturing is clear: the air gap is dead. The convergence of Artificial Intelligence, Big Data, and cloud computing is dissolving the physical isolation that once protected industrial networks. We are moving rapidly from a world of human-to-system interaction to one of system-to-system, machine-to-machine, and IIoT communication. In this hyper-connected future, increasingly complex software systems on the factory floor will demand constant, automated cloud connectivity for license management, predictive maintenance, and real-time optimisation.
Manufacturing companies that attempt to cling to the “air gap mentality” of the 1990s will find themselves defending a perimeter that no longer exists. They will be left with a network resembling Swiss cheese – full of ad-hoc holes punched through by well-meaning engineers and desperate vendors needing access. This is unsustainable and inherently insecure.The only viable path forward is to accept that the network perimeter has dissolved. Security can no longer depend on where you are or which cable you are plugged into. It must depend entirely on who or what you are. In this distributed, specialised, and automated world, identity is the new air gap.
Get In Touch
Ready To Learn More?
Agilicus AnyX Zero Trust enables any user, on any device, secure connectivity to any resource they need—without a client or VPN. Whether that resource is a web application, a programmable logic controller, or a building management system, Agilicus can secure it with multi-factor authentication while keeping the user experience simple with single sign-on.