
Secure Connectivity for Multi-Site Manufacturing
The transition to multi-site manufacturing and industry 4.0 requires a remote access solution that delivers seamless, identity-based access for every site and contractor.
Executive Summary
Manufacturing organizations are going through a change in their manufacturing floor – Industry 4.0 along with just-in-time delivery/production models are creating organization and technical changes in manufacturing. Formerly, a single company would process raw materials into finished goods in a single large facility (e.g. see Rouge River plant), through specialized production lines and facilities in the compound. Today, a set of contract manufacturers, both co-located and non-collocated produce finished sub-assemblies. For example, a vehicle transmission is sent back-and-forth across the Canada/US/Mexico border seven times in the manufacturing process. The current manufacturing process interoperates in technical systems such as inventory management, management execution systems, as well as industrial control systems. With the small on-hand inventory associated with just-in-time inventory means that any outage on the manufacturing floor is magnified, blocking all other companies in the delivery chain.
In this white paper we outline some of the organizational challenges associated with having multiple teams at multiple sites working for multiple companies, and the technical challenges associated with increasingly complex industrial control systems located in a larger number of small sites. We propose how Agilicus AnyX with its unified authentication zero trust architecture resolves these issues in a safe, secure, efficient fashion. A Zero Trust platform addresses every critical constraint, and provides a secure access solution for the manufacturing industry.
Introduction
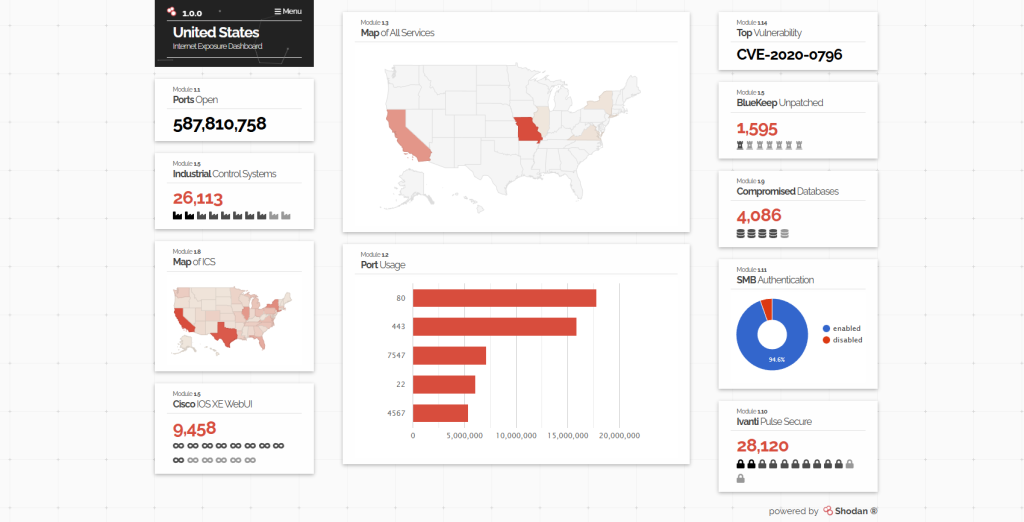
Manufacturing organizations naturally grow to multi-site operations through organic growth, mergers and acquisitions, or expansion to other geographies. With multi-site operations, the requirement to access shared resources including on-premise self hosted software and industrial control systems remotely is critical for day-to-day operations. Organizations will require that these remote access tools seamlessly layer on to their existing network configuration, are simple to deploy, meet their budget requirements, and comply with strict government, best practice, and organizational security requirements. Over the past decades, technologies such as VPN, Remote Desktop, Jumpboxes, etc., have been common practice to remotely access shared resources. With manufacturing moving towards industry 4.0, network connected devices and remote access are becoming the reality, and with it, the cyber threat landscape is evolving, with AI scanning for publicly accessible network vulnerabilities, and arming threat actors to do more with less – allowing small-scale threat actors to become serious risks. According to Shodan.io there are close to 600 million open ports connected to the public network in the United States alone, with over 12,000 HMI, PLC, SCADA units exposed through open ports on public IP addresses. This publicly accessible information along with powerful LLMs enables threat actors of all skill levels to become more effective in carrying out attacks. Each and every open port on a network is an entry point into a network, giving threat actors the ability to use lateral traversal and scan the network for resources to breach. Technologies such as a VPN require a publicly accessible IP address in order to connect, making it impossible to use a VPN while protecting yourself from the public internet.
With the growing requirements of remote access for industrial control systems, operating in a true air-gapped environment is not feasible. Contractors, third party organizations, Vendors and OEM Manufacturers all require remote access to shared resources to carry out their tasks.
Agilicus – a Zero Trust platform – is no longer just an option for remote access: it is the only effective solution to keep your shared resources protected for multi-site connectivity, across multiple corporate identities and cross-user support within sites, while eliminating the need of publicly accessible IP addresses and ports.
Constraints
When evaluating a secure remote access solution connecting users from multiple locations to access shared resources, there are common requirements that are considered when comparing solutions
Must Work Across Different Companies
For a remote access solution to be effective in a multi-site manufacturing environment, it must work across different companies and organizations. Users from all sites must be able to access resources seamlessly with their existing identity provider, and users from third party organizations must be able to access shared resources without the need of shared credentials. Enabling users from different organizations to log in with their existing credentials is a key constraint to ensuring security.
Must Work With Existing Network Schema
When evaluating a remote access solution, a critical element is how it layers on to the existing network of an organization. Within a corporate network, there are often specific networking configurations that need to be upheld for operations and stakeholders mandating no public IP addresses or publicly accessible ports for their network. Created in the 1990s, the Purdue Enterprise Reference Architecture catered primarily to manufacturing and process control enterprises. Industrial networks are often deployed with the Purdue model in mind, and creates a complex existing network to layer on to. Having a remote access platform that integrates into the existing network without requiring configuration is important not only for stability, but also for security of the overall network.
Must be Simple to Deploy
When evaluating a remote access solution, you must consider the deployment of the platform across your network and organization. In a manufacturing environment, there are many resources that are mission critical and can’t afford downtown such as the HMI, PLC, SCADA interfaces on industrial control systems. Deploying a remote access solution must be both lightweight, with no additional footprint, and no long-term project timeline to deploy, reducing overhead and costs.
Must be User Friendly for the IT Team to Deploy and OT Team to Use
A remote access solution must respect IT security requirements while being efficient and easy to use for Operations management. The solution must be a “hands off” approach for the IT team, eliminating the need for constant support tickets, network configurations, or installing/configuring clients/launchers on user laptops. The OT team must have agency to provision, provide access, and use the platform day-to-day without needing IT support.
Must Meet Budgetary Requirements
Evaluating a remote access platform often requires budgetary requirements to ensure the solution either fits to the budget, or vice versa. When looking at budget, it is important to consider the additional costs of not moving forward with a solution such as additional license costs for identity providers, overhead for network / client configurations, managing complex remote access solutions across multiple networks, The ideal solution must be able to meet all remote access requirements while reducing operational costs for IT/OT support
Must Meet Insurance/Regulatory/Industry Requirements
When evaluating a remote access solution, it is critical to take into consideration requirements set out by regulatory/industry requirements. For example, The SEC announced a requirement in 2023 (2023-139) requiring the disclosure of cybersecurity incidents they experience including operational disruption, brand defamation, and legal liabilities from the breach. The remote access solution must also meet requirements outlined in your cyber insurance policy such as Single Sign-On, Multi-Factor Authentication, Granular access, and ability to mitigate travel within an organization’s network.
Site-To-Site Network Connectivity
When manufacturing organizations have multiple locations that need to be connected to one another, such as corporate headquarters connecting to production plants, a VPN is a common solution. VPNs were once the go-to remote access solution but prove to be an insufficient foundation for secure remote access in today’s landscape.
Hub and Spoke
A VPN architecture where all remote locations connect directly to a main hub/office through their own VPN connection. Data from one location to another would flow through the main hub or head office and then to the other location.
Peer-to-Peer
A VPN architecture where all devices, resources and control systems are connected to one another, creating a large interconnected network with no centralized hub, allowing all devices to create a direct connection.
Shared-Nothing
In a shared-nothing approach, each site operates independently with no shared teams, resources. Each site connects directly to the internet, and would be acceptable If an organization exclusively uses SaaS where everything lives in the cloud.
In some circumstances, the network may not allow for a VPN to be used. In order to use a VPN, a publicly accessible IP address must be in place, and that is not always available. Use of satellite/cellular internet is a limiting factor as a VPN requires both inbound and outbound traffic to encrypt data packets bi-directionally, meaning they cannot support a VPN. insurance, industry, or stakeholders may also require inbound traffic to the organization to be disabled for additional security. And in some regions of the world, the use of VPNs are inhibited. For example, In China, the use of VPNs are banned without government approval, which creates remote access issues for manufacturers with a site located in regions of the world where a VPN connection is banned.
With productivity being tied to network connectivity, any downtime in your network impacts your production floor output. Dual WAN redundant connectivity keeps your manufacturing floor operating, and keeps Mean-Time-To-Repair low in the event of network outage. With dual WAN redundancy, separate challenges arise. Learn more below:
Perimiter Level Security
A VPN is designed to create an encrypted connection between two networks for site-to-site connectivity, giving bilateral access to all resources on the shared network creating mutual risk between the two sites. This bilateral access was the root cause of the Colonial Pipeline breach. An inherent flaw with VPN technology is that it does not allow for granular access to resources or permission level access, creating an all-or-nothing environment. Once a user has provided their credentials and the VPN is turned on, they are authorized to access the network in its entirety with no segmentation, access levels or concept of who can access what. Granular access embodies the principle of least privilege – precisely defining and limiting what each user can access – down to specific resources and actions. In 2023, The “CyberAv3ngers” group engaged in targeting Unitronics PLC controllers which were often found in the water and wastewater industries. With no resource segmentation in place, the attackers were able to access the PLC/HMI, which still used the default password of ‘1111’. The attacks caused organizations to halt operations due to loss of availability of the HMI/PLC. Resource segmentation could have directly prevented these attackers from accessing resources.
While VPNs provide encryption at the tunnel level, their inherent architectural limitations leave organizations vulnerable to modern threats that are mitigated by essential security features including multi-factor authentication, single sign-on, password stuffing, and granular access control, reinforcing the need for a comprehensive security strategy for remote access.
Multiple Identities / Corporations
Multi-site manufacturing locations often use different identity providers across multiple sites.For example, a user at site 1 would have credentials user@site1.com and a user at site 2 would have user@site2.com. Another example is when corporate employees may have a user@corp.site1.com account to separate divisions, or job functions. Not only are the domains different across sites, but they could also be using different identity providers altogether (Microsoft, Google, Azure, etc). Managing multiple domains and identity providers becomes increasing complex over time as an organization grows, especially when access is required to shared resources.
Who has multiple identities?
Mergers and Acquisitions
Carrying existing identity providers through mergers and acquisitions. E.g. ABC1 mergers with ABC2, both companies keep existing identities going forward
Multiple Corporate Identities
Having identities across multiple domains, and even unlike providers. E.g. john@abc1.com (google) and John@abc2.com (Microsoft)
Divisional Identities
Organization may utilize different identities to differentiate divisions within their organization. E.g. john@corp.abc.com and jane@support.abc1.com
Contract Manufacturers
Contract manufacturers you are working with need access to your shared resources to carry out their tasks. They use their own corporate identities..
Joint Venters and Partnerships
Joint ventures require both organizations to have access to resources they need during the course of the venture. They will use their own corporate identities.
Supporting Organizations
External support organizations that provide troubleshooting, maintenance, service contracts will need to access your resources to carry out their tasks.
When accessing shared resources across sites, users are not able to utilize their existing identity provider for single sign-on, even on systems where it is natively supported as the login credentials are spread over multiple domains / identity providers. A common workaround for this is to create new identities for all users. This creates:
- Increased support tickets: Multiple accounts per user creates complexity resulting in unnecessary support tickets for password resets, account authorization, or using the incorrect account for login.
- Additional cost: Creating new users results in additional licensing costs, and depending on your organization, provisioning a new user may require a complete user license.
- User management: Creating new user accounts results in additional management of credentials. Provisioning, and deactivating users now needs to be done in multiple locations.
In some cases, organizations will opt to create shared team accounts to access resources, such as marketing@site1.com or Tier2support@site1.com. Creating shared accounts to log in to resources that need to be accessed remotely by other sites creates risk for cyber breaches through:
- Leaked passwords: Shared accounts often have the user credentials shared in a way that is easily accessible by users (post-it notes, shared docs, shared via messaging app).
- Lack of granular access: All users who have access to the login credentials can access at the highest level of authorization that needs to be granted
- No Multi-Factor Authentication: Utilizing shared credentials often results in disabling MFA or using refractor services to send codes to multiple devices, defeating the purpose of utilizing MFA as a security measure
Single Sign-on enables organizations to provision users, vendors, contractors, third-party support, etc with their existing credentials, regardless of their identity provider (Microsoft, Google, Azure, etc), eliminating the need to create new users on the active directory and burdening the cost of additional licenses. When creating user credentials on the active directory for third-party access, organizations often create a single account for a vendor to use. The credentials for this account are then shared with the team to have remote access to the resources they need. However, there is a lack of control for how passwords are stored (printed out, shared sheets, post-it notes, etc), no insight into when certain employees should no longer have access – resulting in the password staying the same, and not having insight to who is actually accessing critical systems. Single Sign-On is a security feature that eliminates the use of shared passwords while reducing licensing costs on the active directory, a key security feature missing from VPNs
Cross-Site Support
The manufacturing industry is changing. Industrial control systems which were once made up of switches and buttons, are now network connected, requiring a specialized workforce to program, operate, maintain, and repair. Organizations often turn to contract based third party employees, or a specialized user that manages multiple sites. Having specialized users as a part of a workforce with remote access to all sites, allows organizations to handle these tasks efficiently. Accessing multiple sites with a VPN comes with inherent limitations:
One Active Connection at a Time
A VPN only supports one client or connection per device. Connecting to multiple sites would require frequent connecting / disconnecting.
Constant Need for Network Configurations
A device can only run one VPN client. Needing to connect to multiple sites would require frequent network configurations.
Unable to Access from Anywhere
Public internet connections from common locations (hotel, cafe, airports, etc.) do not allow for VPN configuration, increasing mean time to repair and reducing efficiency
All-or-Nothing Access
A VPN provides all-or-nothing access, which could result in unauthorized access and control of industrial control systems or misuse of shared resources
Solution – Agilicus AnyX
Utilizing a Zero Trust Architecture enables your organization to establish secure remote access to remotely support shared resources across multiple manufacturing locations. With AnyX, your users located across multiple locations can log in to resources with Single Sign-On and Multi-Factor Authentication using their existing identity, even when not natively supported. Where a VPN allows full access to a network, AnyX enables organizations to implement a least-privilege access approach to shared resources. Least-privilege access ensures that shared resources and industrial control systems can only be accessed by the users that need it, with read write access, and for what required time frame.
Agilicus AnyX is an identity aware proxy, ensuring only authorized users (by validating with identity provider and multi-factor authentication) have access to the resources they should and at what permission level. The Agilicus connector is hosted on-site with no additional footprint, enabling a seamless connection to the shared resource, regardless of network configuration.
Overcoming Constraints
When evaluating a secure remote access solution connecting users from multiple locations to access shared resources, there are common requirements that are considered when comparing solutions. Agilicus AnyX overcomes these common constraints for simple deployment of a Zero Trust platform in your multi-site manufacturing company.
Must Work Across Different Companies / Sites
AnyX is an Identity aware proxy, authenticating users before providing access to resources in a Zero Trust model. AnyX is able to work with multiple identity providers across multiple companies, providing a unified Single Sign-On experience, where any authorized user can access any shared resource, regardless of which location / site they are accessing from.
Must be Simple to Deploy Across Sites
AnyX does not rely on deploying new hardware to be deployed. with no additional footprint on your network, AnyX is simple to deploy across all sites. No long-term project planning or roll-out. In most scenarios, sites can have their first connector live and user connected within an hour, enabling organizations to benefit from Zero Trust in a short amount of time.
Must be User Friendly for the OT Team to Use
AnyX utilizes a web-based launcher for both the administrative panel, as well as launcher for end users. Operations team leaders can provision remote access for users in seconds, and users can access resources from anywhere, on any device with a web browser using their existing identity provider.
Must Meet Budgetary Requirements
Operational teams often do not carry a budget for remote operations, therefore the solution must be one that does not require a budget approval process, or falls in-line with their existing budget. AnyX is able to work with your existing budgets, often washing out with the cost of legacy tools that are already in place. ROI is simple, AnyX improves effeciency in your support workflow, and the cost savings of saving a single trip on-site for a vendor, third party support organization, or internal employee adds directly to the ROI of AnyX.
Must Meet Insurance / Regulatory Requirements
Insurance, Regulatory and Legislative requirements often require Zero Trust remote access of critical elements of Zero Trust including Multi-Factor Authentication, Precise Authorization, and Granular Audit Reports. AnyX enables your organization to meet insurance, legislative and regulatory requirements through best practices for remote access.
Must Work With Existing Network Schema
AnyX is network agnostic, layering on to your existing network schema without requiring firewall reconfigurations, port forwarding, or DNS changes to deploy, securing your manufacturing sites without long-term project planning eliminating production downtime on your manufacturing floor.
Solving Site-To-Site Network Connectivity
AnyX enables your organization to adapt a Zero Trust architecture for remote support of industrial control systems located in other sites. Being able to remotely access resources securely from any device with a web browser reduces mean time to repair, and improves operational efficiency.
Allowing access through a web browser eliminates the need for clients to be installed/configured on devices and eliminates the process of connecting/disconnecting from one site to another for access to multiple resources across multiple sites simultaneously, from anywhere they are.
AnyX is a Zero Trust platform that layers on your existing network, regardless of its schema, without requiring any network configurations such as port changes, IP configurations, or subnet changes to deploy. With a web-based launcher, AnyX is simple to deploy for IT teams and seamlessly integrate into OT workflow. Administrators of the platform gain agency by provisioning users with their existing login credentials – and what they can access, at a read vs. write level, in seconds. A simple deployment with no additional footprint required makes AnyX a solution that fits organizations of all sizes, providing a significant reduction in cost and time of deploying a remote access solution with lower overhead and reduced license costs (VPN, Remote Desktop, Multiple user licenses in existing identity providers).
Beyond Perimeter Level Security
Where VPN technology is a moat & castle approach where a user verifies at the external gates and has access to all resources within, Zero Trust resembles a high-security building where identity and access are continuously checked at every point – from the front door and elevators to individual rooms and resources within. Each access attempt, no matter the location, requires separate verification. AnyX enables your organization to implement a Zero Trust architecture to increase overall security posture while being convenient to use and operate, and stay compliant with cyber insurance and mandates. Unlike a VPN, Zero Trust:
- Blocks lateral traversal, preventing threat actors from moving around your network by segmenting each resource
- Moves away from an all-or-nothing access approach with granular permissions to only the users that need them
- Supports Multi-factor authentication and single sign-on for any device, even if it doesn’t natively participate
Unifying Multiple Identities
Agilicus AnyX is the only platform that enables organizations to utilize single sign-on for all shared resources, regardless of identity provider, eliminating the need for new accounts being created in active directories. Credential management and provisioning access for users is simple through the AnyX dashboard, enabling administrators to provision users in seconds.
Enabling Cross-Site Support
With industry 4.0 changing how users interact with HMI, PLC, SCADA systems, and how those systems are connected to networks for big data, AI analysis, and EO support, the requirement for highly skilled workforce comes into play. It may not be feasible to hire users with specialized skillsets at each manufacturing site, requiring users to support multiple sites, or aa third party organization to provide additional support. AnyX enables users to support industrial control systems cross-site, logging in with their existing identity provider for a unified single sign-on experience. Users are only granted access to the systems/resources they need to complete their job – eliminating the ability to crawl the network, or work on other resources that are unauthorized. Users can now support systems across multiple sites, as if they were there, all with a Zero Trust platform.
Conclusion
As manufacturing companies grow and expand their operations across multiple facilities, the need to access shared resources increases. Industrial control systems that were once manually operated with switches, buttons, and levers are now operated through HMI, PLC, SCADA interfaces which are network connected. With the growing requirements of remote access for industrial control systems, and the increasing risks of today’s threat landscape, Agilicus AnyX, a Zero Trust platform is no longer just an option for remote access; it is the only effective solution to keep your shared resources protected for multi-site connectivity, across multiple corporate identities and cross-user support within sites.
When multiple manufacturing sites differ in identity provider, teams, and/or geographical location VPNs and other traditional access methods are no longer able to provide simple and secure remote access to your internal teams and third-party contractors. Lateral traversal, shared accounts, connecting/disconnecting between sites, and client installs create security and operational efficiency gaps that are remedied by adopting a Zero Trust platform.
AnyX solves these gaps by segmenting resources with least-privilege access, enabling multi-factor authentication and every resource – even if not natively supported, facilitating access directly through a web browser, requiring zero hardware or network configurations, and being the only platform to allow single sign-on across unlike identities.
Get In Touch
Ready To Learn More?
Agilicus AnyX Zero Trust enables any user, on any device, secure connectivity to any resource they need—without a client or VPN. Whether that resource is a web application, a programmable logic controller, or a building management system, Agilicus can secure it with multi-factor authentication while keeping the user experience simple with single sign-on.