The Internet and its tools started out fully trusting. Protocols like SMTP (email) have no authentication built in. HTTP later added basic-authentication, which i seffectively a username+password on each transaction. The Secure Sockets Layer (SSL, later standardised as Transport Layer Security, TLS) came along and gave us privacy, but still not authentication.
Initially we viewed the problem as a User logging in, as session setup: a one-time activity. But later, API’s came along, progressive web applications blurred the lines between a web page and an always-on application. We needed a safe means of acting as a user, without the user being involved in each transaction.
Enter the humble JSON Web Token (JWT). The JWT allows an application to embed assertions (claims) and identity into a cryptographically secure, transportable object. An application can present the JWT to act on behalf of the user.
Today you will find JWT present in nearly everything you do. Your banking, your email, your mobile applications. You can see one by looking in the web console of your browser (usually by hitting ctrl-shift-I) and looking for a cookie or local storage item with the word “token” in the name. It will be a long gibberish-looking string. You can paste it into https://jwt.io/ to see what it has inside. Now, is this safe? Should you paste your security token into a random web page on the Internet? (hint: no, not really). If you need to do this frequently, you might try:
npm install -g jwt-cliAnd now you have a command called jwt you can use to see the same info, locally, without sharing the security credentials.
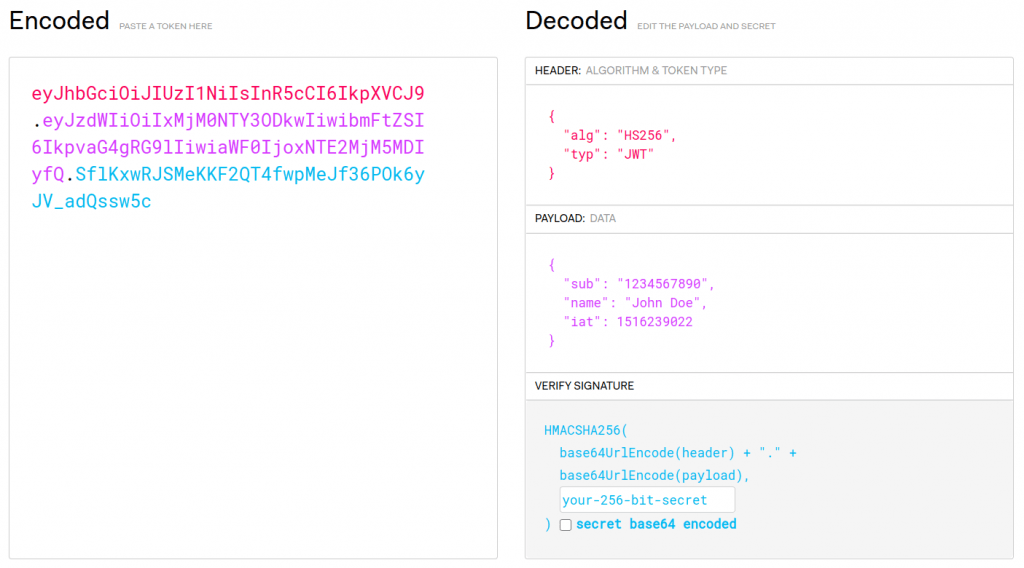
Inside your JWT you will see a set of fields like iat, nbf, etc. These are all defined in RFC 7519 JSON Web Token (JWT). (iat means issued-at, nbf means not-before, two of the time-fields).
If you are building a new application today, whether web-based or not, or building API today, you must look at JWT. It is a far better standard and method than propogating username+password around, and far better than arbitrary secrets (called API keys). Its the core of Zero Trust, and can dramatically simplify your firewall configuration and security.
