The Frictionless Factory: Solving the Connectivity Crisis in Hyper-Specialised
Executive Summary
The era of the vertical factory where raw ore went in one end and a finished car came out the other is dead. The modern manufacturing floor is a triumph of hyper-specialisation. Your efficiency now relies on a global orchestra of 50 or more distinct partners, from headlight suppliers to robotics integrators, all working in concert.

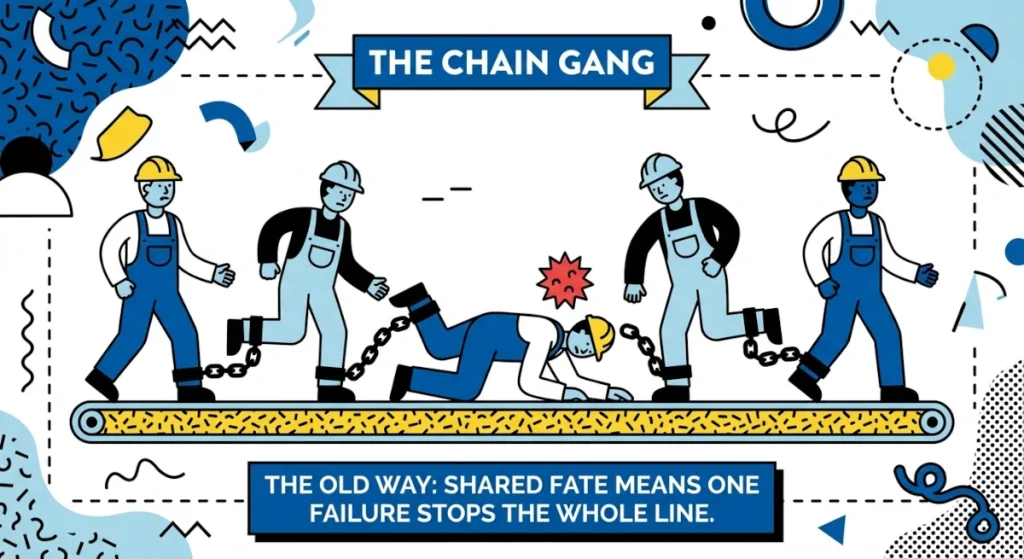
However, our connectivity architecture has not kept pace with this economic reality. To make specialisation work, we chained our systems together with a “Web of VPNs.” While this connected our partners, it created a dangerous “Shared Fate” architecture. As the automotive industry witnessed during the Jaguar Land Rover incident in the Fall of 2025, a malware infection in a single supplier’s network can traverse these Layer-3 tunnels, bypass firewalls, and halt production across an entire multi-national corporation.
But the risk isn’t just security: it is friction. The legacy VPN model is an operational drag. It forces third-party vendors to install software, navigate IT ticket queues, and wrestle with complex provisioning before they can fix a downed machine. This bloats Mean Time To Repair (MTTR) and kills throughput.
There is a better way. Agilicus AnyX introduces the “Island Architecture.” By moving from Network Trust to Identity Trust, we decouple access from the network. We allow vendors to access specific applications (like SAP or HMI screens) via a browser, without their device ever touching your internal network. The result is instant, clientless onboarding for your experts and total immunity from lateral malware movement. It is how you secure the supply chain without slowing down the line.
The Problem: The High Cost of the “Web of VPNs”
The Economic Shift: From Rouge River to Hyper-Specialisation
In the 1920s, Henry Ford’s Rouge River plant was the gold standard of manufacturing. It was a fortress of vertical integration: steel was forged on-site, glass was poured on-site, and vehicles were assembled in a single continuous flow. The factory was an island, self-contained and self-reliant.
Fast forward to 2025. That model is economically obsolete. The modern automotive or manufacturing giant is not a builder, but an assembler. We rely on Just-In-Time (JIT) delivery and hyper-specialised partners. We don’t make the seatbelts; a specialist does. We don’t program the robotic arm; a system integrator does.
This specialisation drives quality and cost-efficiency, but it introduces a critical dependency: Access. The headlight vendor needs real-time access to your SAP system to manage inventory. The robotics vendor needs remote access to your SCADA Human-Machine Interface (HMI) to recalibrate a drifting arm.
The Operational Drag
Historically, IT departments solved this access problem with the Virtual Private Network (VPN). They built a “mesh” of encrypted tunnels connecting every vendor’s network to the factory floor.
For the VP of Operations, this solution has become a bottleneck.
- The Friction: Onboarding a new vendor via VPN is slow. It involves installing software clients, managing certificates, and waiting on IT helpdesk tickets.
- The MTTR Hit: When a line goes down at 2:00 AM, and the expert is a third-party contractor in a different time zone, every minute spent fighting with VPN connectivity is a minute of lost production. If it takes 4 hours to provision access, that is 4 hours of downtime.
The “Shared Fate” Failure
The operational friction is annoying; the security reality is catastrophic. VPNs function at Layer 3 of the network model. They connect networks, not people. Once a tunnel is established, it allows “pinging across sites.”
We saw the devastating consequence of this in the Fall 2025 Jaguar Land Rover incident. A ransomware event originated at a smaller supplier, a classic “Headlight Vendor.” Because of the flat, bridged nature of the VPN mesh, the malware traversed the tunnel, moved laterally into the main production network, and locked up operations across the UK.
You built a distributed network of multiple sites to ensure resilience. But the VPN architecture chained them all together, creating fragility. When one ship sank, it pulled the whole fleet down with it.
The Solution: The Island Architecture with Agilicus AnyX
We cannot return to the Rouge River days; specialisation is the engine of the future. We must simply change how we connect. We need an architecture that respects the “Island” nature of modern business entities.
Agilicus AnyX delivers this through a Zero Trust, Identity-Centric approach.
The Concept: Islands, Not Bridges
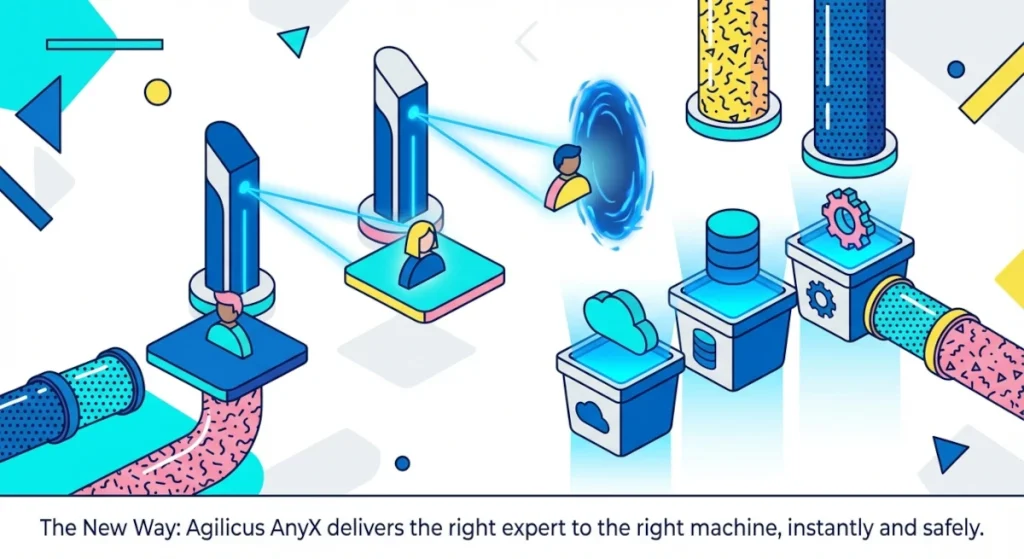
Imagine your factory sites and your vendors as separate islands floating in an ocean. In the old model, we built permanent bridges (VPNs) between them. If an enemy crossed a bridge, they could march anywhere.
With Agilicus AnyX, we burn the bridges. There is no physical network route between the vendor’s laptop and your Programmable Logic Controller (PLC). Instead, we use a “ferry” system of an Identity-Aware Proxy. We transport the user to the application, verify their ID, and drop them off exactly where they need to be, and nowhere else.
Frictionless Operations (The “Why” for Ops)
For the Operations Director, the primary benefit is speed.
- Clientless Access: Agilicus AnyX is browser-based (HTML5). The vendor does not need to install a VPN client, manage keys, or call IT.
- Instant MTTR Response: If a machine breaks, the vendor logs into a web portal using their own native credentials (SSO/OIDC). They are authenticated instantly and looking at the HMI screen in seconds.
- Simplified Onboarding: Granting access is as easy as sending an email invitation. Revoking it is just as fast.
Screens, Not Packets
Technically, this works by decoupling the user from the network. When a vendor accesses your HMI or SAP system via Agilicus AnyX, they are viewing a stream of the data. Their laptop never sends a single network packet to your internal grid.
This creates an effective “Air Gap.” If the vendor’s laptop is crawling with ransomware, the malware cannot jump the gap. It is trapped in their browser session. Your factory keeps running, immune to the hygiene issues of your supply chain.
Compliance and Simplicity
This approach replaces thousands of complex firewall rules with a simple identity policy: “Allow John from Vendor A to see the Stamping Press HMI.” This simplicity drastically lowers the complexity of managing Joint Ventures, divestitures, or mergers, and satisfies the strict segmentation requirements of NIS2 and IEC 62443 (see Industrial Zero-Trust Micro-Segmentation: Leverage Identity To Simplify IEC-62443 Zones)
Conclusion
Complexity is the price of specialisation. In the 21st century, we accept this complexity because it allows us to build better products faster. But we should not pay a “tax” on that complexity in the form of downtime or cyber risk.
The VPN is a relic of a different era, a tool designed to connect static offices, not dynamic, hyper-specialised supply chains. As long as you rely on Layer-3 tunnels, you are choosing between Agility (letting vendors in) and Security (keeping malware out).
Agilicus AnyX eliminates that trade-off. By adopting the Island Architecture, you ensure that:
- Throughput is protected from the ripple effects of supply chain attacks.
- MTTR is minimised by removing IT friction from the repair process.
- Risk is controlled, lowering insurance premiums and ensuring compliance
Get In Touch
Ready To Learn More?
Agilicus AnyX Zero Trust enables any user, on any device, secure connectivity to any resource they need—without a client or VPN. Whether that resource is a web application, a programmable logic controller, or a building management system, Agilicus can secure it with multi-factor authentication while keeping the user experience simple with single sign-on.