Authentication Audit
Who Authenticated When, Where
The Authentication audit provides a trail of all attempts by users (or service accounts) to prove their identity. This authentication process can have multiple steps, depending on authentication rules and upstream identity providers.
Authentication Audit
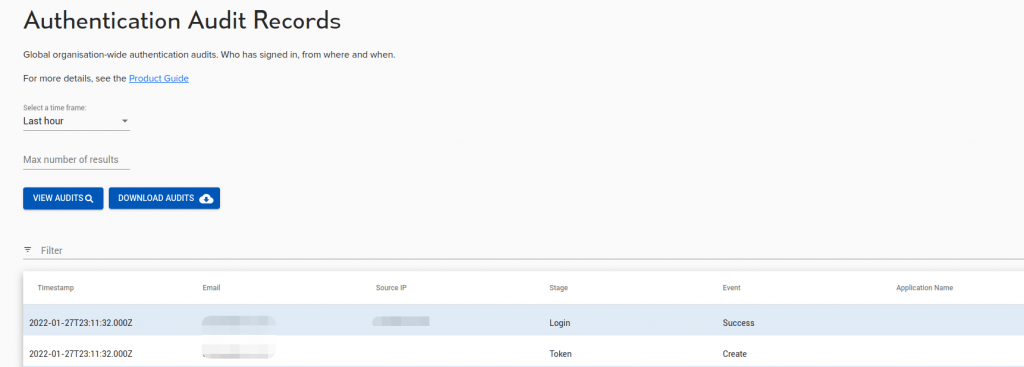
The Authentication audit provides a trail of all attempts by users (or service accounts) to prove their identity. This authentication process can have multiple steps, depending on authentication rules and upstream identity providers.
Not all stages will have all fields available. Each step has a timestamp (in UTC), an ‘Email’ (user), ‘Source IP’, Stage, Event, and Application Name (authentication client).
Authentication audits are also available via the API where additional columns may be extracted.
| user_id: string | The system-local id of the user performing the action. |
| upstream_user_id: string | The id of the user in the upstream system, if available. |
| org_id: string | The id of the organisation of the issuer against which the user is authenticating. |
| org_name: string | The name of the organisation of the issuer against which the user is authenticating. |
| time: date-time | the time at which the record was generated. |
| event: string | The event which generated the record. The meaning of the event depends on the stage where it occured. |
| source_ip: string | The IP address of the host initiating the action |
| token_id: string | The id of the token issued or reissued as part of the authentication. |
| trace_id: string | A correlation ID associated with requests related to this event |
| session: string | The session associated with tokens related to this event. This can be used to tie the actions undertaking by requests bearing tokens with the same session back to the authentication events which created the tokens. |
| issuer: string | The issuer the user logged in to. |
| client_id: string | The client id of the web application, client, etc. that the user is logging in with. Note that this is not the id of the IssuerClient, but rather the id presented to the authentication system to identify that client. This corresponds to name in the IssuerClient. |
| application_name: string | The name of the application within the system the user is logging in to. |
| login_org_id: string | The id of the organisation that the user is logging in to. Note that this is disctinct from the org_id field, which is tied to the issuer. This id is tied to the application. |
| login_org_name: string | The name of the organisation that the user is logging in to. This corresponds to login_org_id. |
| upstream_idp: string | The name of the identity provider proving the identity of the user. |
| stage: string | The stage of the login process. This identifies where in the pipeline the event was generated. |
| user_agent: string | The user agent of the client used to perform the login. |
Want Assistance?
The Agilicus team is here for you. The ‘Chat‘ icon in the lower left, here, or in the administrative web page, goes to our team.
Or, feel free to email support@agilicus.com
Not yet a customer? The TRY NOW button will walk you through the process.