Learn. Do. Teach.
Agilicus’ unnoficial motto. We learn something, we do it, we teach others. Our blog contains updates on our progress.
-
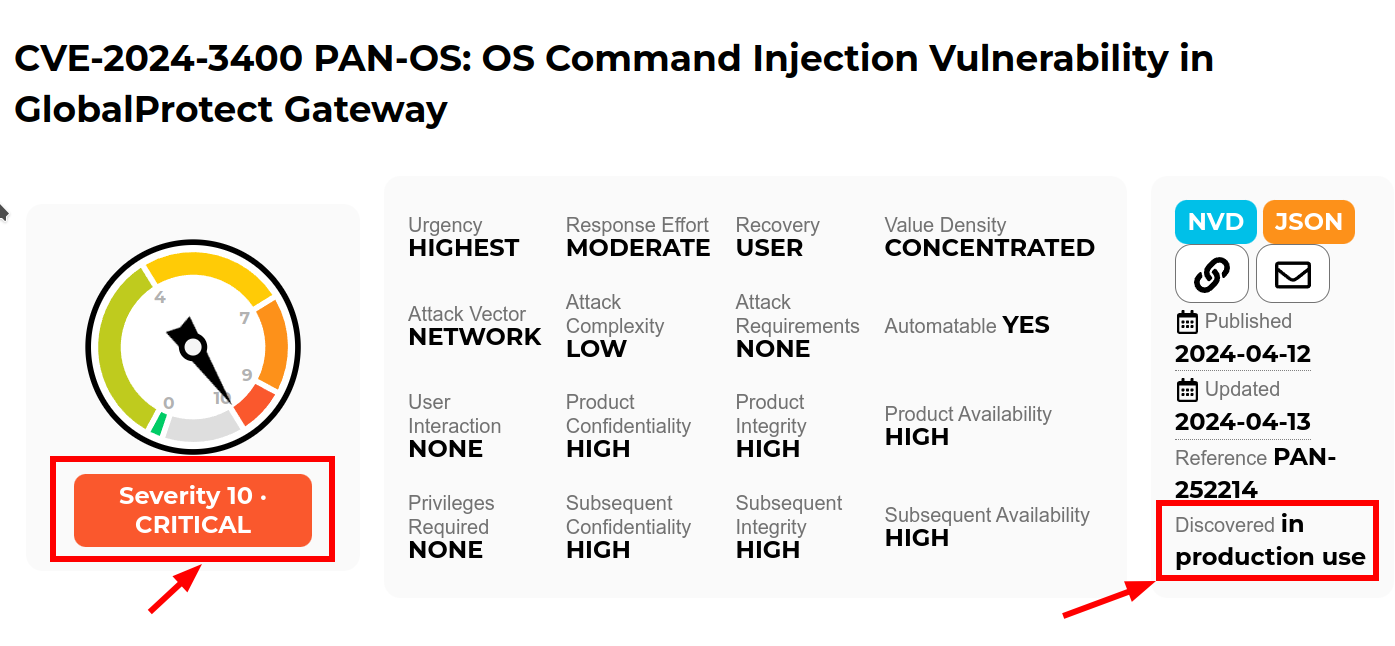
Quis custodiet ipsos custodes: When Good Firewalls Go Bad
Read more: Quis custodiet ipsos custodes: When Good Firewalls Go BadRecently Palo Alto announced a 10.0 CVE in the Global Protect feature of their PAN-OS firewall. “Unauthenticated attacker [can] execute arbitrary code with root privileges on the firewall”. Well, that is not good. But, how “not good” is it? It’s terrifyingly bad ungood in fact.
-

CISA: 8 Top Cyber Actions for Securing Water Systems
Read more: CISA: 8 Top Cyber Actions for Securing Water SystemsCISA this week issued a Fact Sheet 8 Top Cyber Actions for Securing Water Systems giving a set of “do it now” practical actions for securing water and wastewater systems. Let’s talk about ‘Exposure’ to the Public-Facing Internet
-
Three Strategies To Help: Cisco ASA AnyConnect and WebVPN added to CISA Known Exploits
Read more: Three Strategies To Help: Cisco ASA AnyConnect and WebVPN added to CISA Known ExploitsCisco ASA AnyConnect and WebVPN added to CISA Known Exploits. Do you have one running on autopilot in your plant somewhere? Maybe between the IT and OT network? Maybe running the DMZ?
-

Multiple Connections Inbound Access Challenge
Read more: Multiple Connections Inbound Access ChallengeMultiple Internet connections can create inbound connectivity issues for remote industrial connectivity. The Multiple Connections Inbound Access Challenge.
-

Ground Hog Day: Fortinet VPN Edition
Read more: Ground Hog Day: Fortinet VPN EditionAnother day, another VPN letting the world in to snoop around and fondle your crown jewels: Fortinet edition.
-

Dutch Defence Detail Dastardly Dirty Deed
Read more: Dutch Defence Detail Dastardly Dirty DeedThe Netherlands ministry of defence just published the cliff-hanger document TLP:CLEAR MIVD AIVD Advisory COATHANGER regarding a remote access attack of their Fortinet FortiGate VPN by “a state-sponsored actor from the People’s Republic of China”. CVE-2022-42475 was the weakness. One thing that is unusual about the report is the direct attribution: this is rare.
-

Howto: Open Source Intelligence and your Digital Footprint
Read more: Howto: Open Source Intelligence and your Digital FootprintLet me show you a very simple means of Open Source Intelligence (OSINT) on yourself. If I can do this, anyone can do this, and if anyone can do this, someone bad can do this.
-

US sanctions Iranian officials for cyber-attacks on water plants
Read more: US sanctions Iranian officials for cyber-attacks on water plantsA group named Cyber Av3ngers affiliated with the IRGC targetting, modifying the HMI of publuc water systems. Today the individuals are sanctioned under anti-terrorism executive order.
-

VPNs in Industrial Environments: Old Yeller
Read more: VPNs in Industrial Environments: Old YellerVPNs in Industrial Environments: Old Yeller. It was a faithful friend for years, and now its time to shoot it before it bites you.
-

Begone Ivanti Industrial VPN Sayeth CISA
Read more: Begone Ivanti Industrial VPN Sayeth CISAED 24-01 directs agencies to instantly remove Ivanti Industrial VPN from industrial operations. Defence In Depth, Zero Trust give you more time to react.
-

Inbound HMI: Cyber Army of Russia Targeting US water facilities
Read more: Inbound HMI: Cyber Army of Russia Targeting US water facilitiesCyber Army of Russia Targeting US water facilities. Zero Trust Cybersecurity for VNC to prevent.
-

From Smoke Stacks to Smartscapes: Evolving Industrial Operations in the Digital Age
Read more: From Smoke Stacks to Smartscapes: Evolving Industrial Operations in the Digital AgeSmoke Stacks to Smartscapes. Past, Present, Future, the evolution in-place of the industrial control system, and the airgrap that once protected it.
-

Off-Grid Agricultural Cyber Physical Systems
Read more: Off-Grid Agricultural Cyber Physical SystemsThe “John Deere Business Model” of taking something traditional and making it subscription. Starlink and its complex remote access needs due to CGNAT. And, cybersecurity, notably Cyber Physical Systems with their scary downsides of being able to move and cause damage.
-
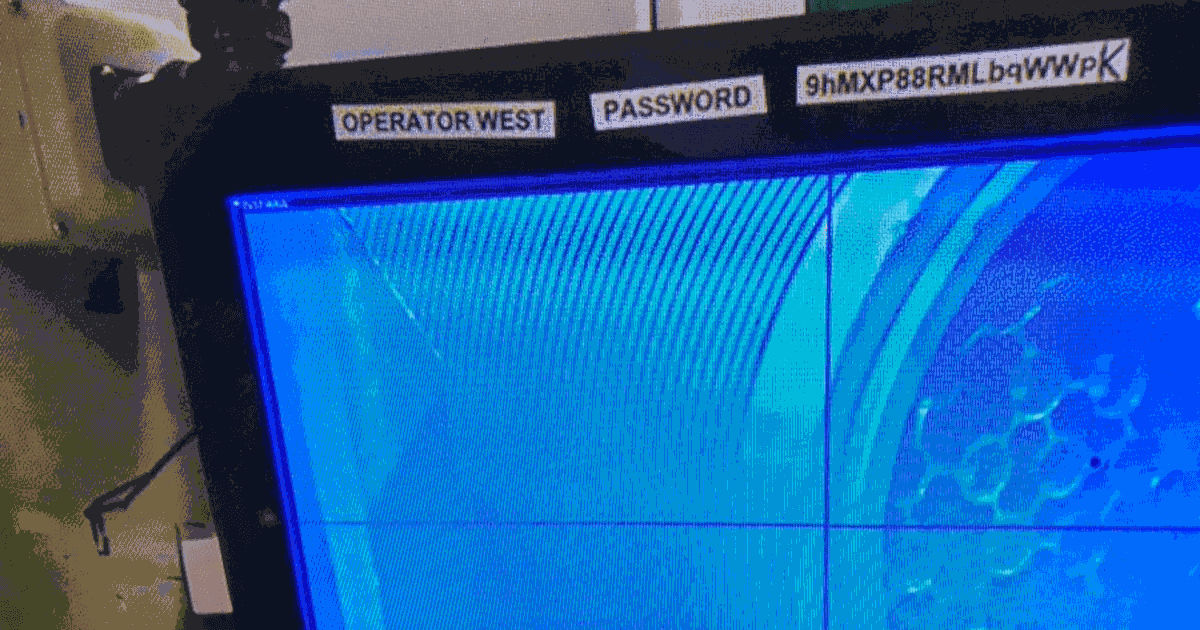
Hard Industrial Cybersecurity is hardly secure, nuclear waste edition
Read more: Hard Industrial Cybersecurity is hardly secure, nuclear waste editionOne thing all industrial control installations have in common, they straddle the complexity of modern information technology with the dangers of operational technology and its inherent control of things which can go bump and boom. Hard Industrial Cybersecurity
-
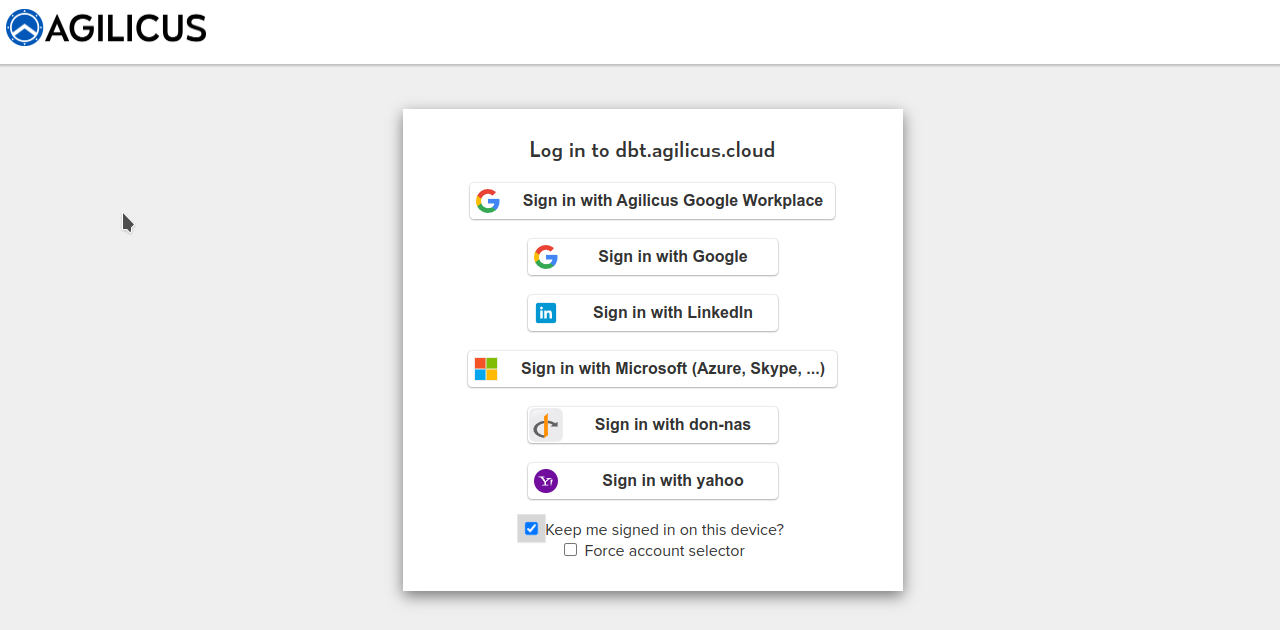
Your Logo: Theming Agilicus AnyX
Read more: Your Logo: Theming Agilicus AnyXAgilicus AnyX supports personalising the sign-in and usage environment to match your corporate brand. This is more than just asthethic: a consistent look and feel helps train users to reduce the likelihood of a successful spear-phishing attack.
-
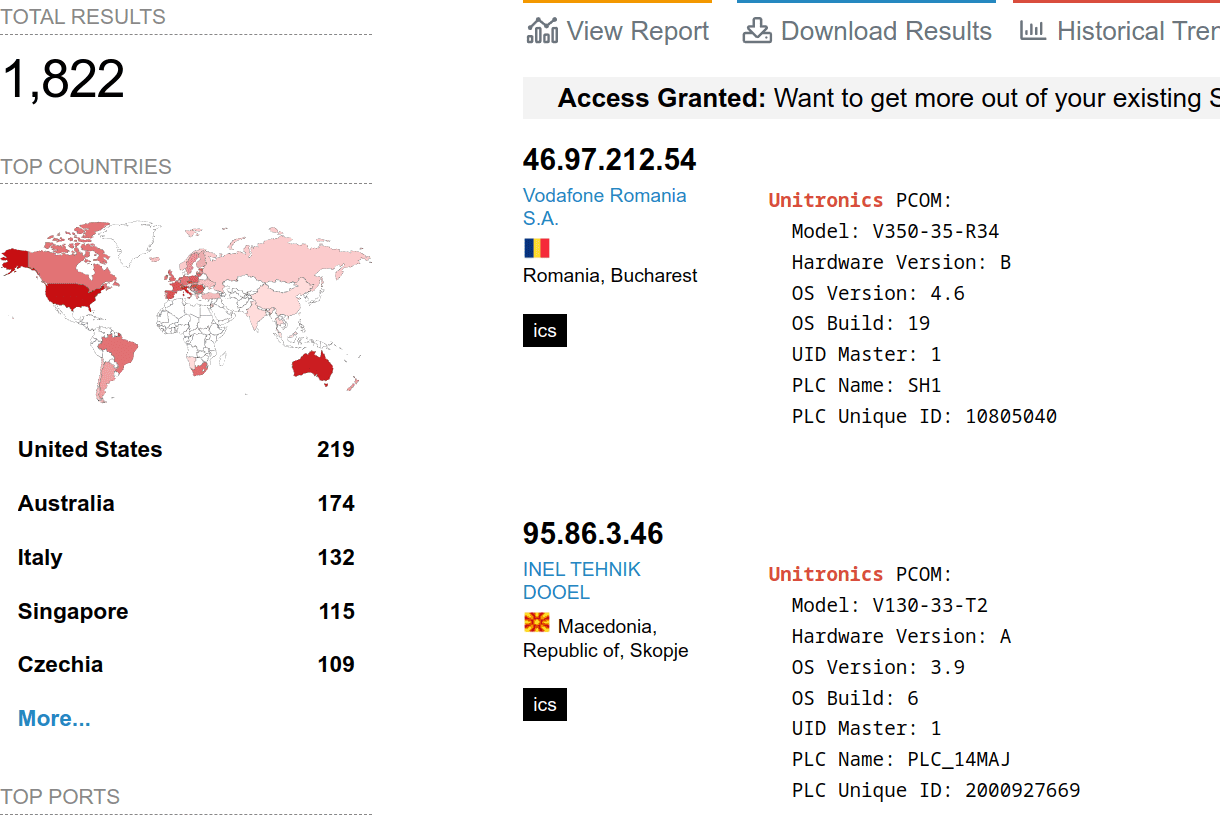
Avoid Exploitation of Unitronics PLCs used in Public Water Systems
Read more: Avoid Exploitation of Unitronics PLCs used in Public Water SystemsExploitation of Unitronics PLCs used in Public Water Systems for political purposes. Recommendations.
-

Attainable Municipal Zero Trust
Read more: Attainable Municipal Zero TrustAttainable Municipal Zero Trust: Key insights from recent Zero Trust implementations by Municipalities. Why, How, What ROI, Lead use cases.
-

Using Zero Trust to Enable Secure Remote Access to SCADA for Water Systems
Read more: Using Zero Trust to Enable Secure Remote Access to SCADA for Water SystemsThis blog post explores the challenges of securing remote access to SCADA systems and how Zero Trust can act as a solution.
-

Zero Trust vs. VPN: A Comprehensive Comparison for Secure Remote Access
Read more: Zero Trust vs. VPN: A Comprehensive Comparison for Secure Remote AccessIn this blog post, we’ll dive into the Zero Trust vs. VPN security model differences and why the former is ultimately the far superior choice for secure, seamless remote access.
-

SSH for Remote Access: Every User, Every Device, Every Application
Read more: SSH for Remote Access: Every User, Every Device, Every ApplicationIn this blog post, we’ll delve into the challenges of enabling SSH for remote access and how you can do so without compromising security through Zero Trust.
-
Simplifying Secure Access: Enabling Rockwell Automation Remote PLC Access Without a VPN
Read more: Simplifying Secure Access: Enabling Rockwell Automation Remote PLC Access Without a VPNIn this post, we’ll explore the limitations of VPNs and delve into how to enable VPN-less Rockwell Automation remote PLC access.
-
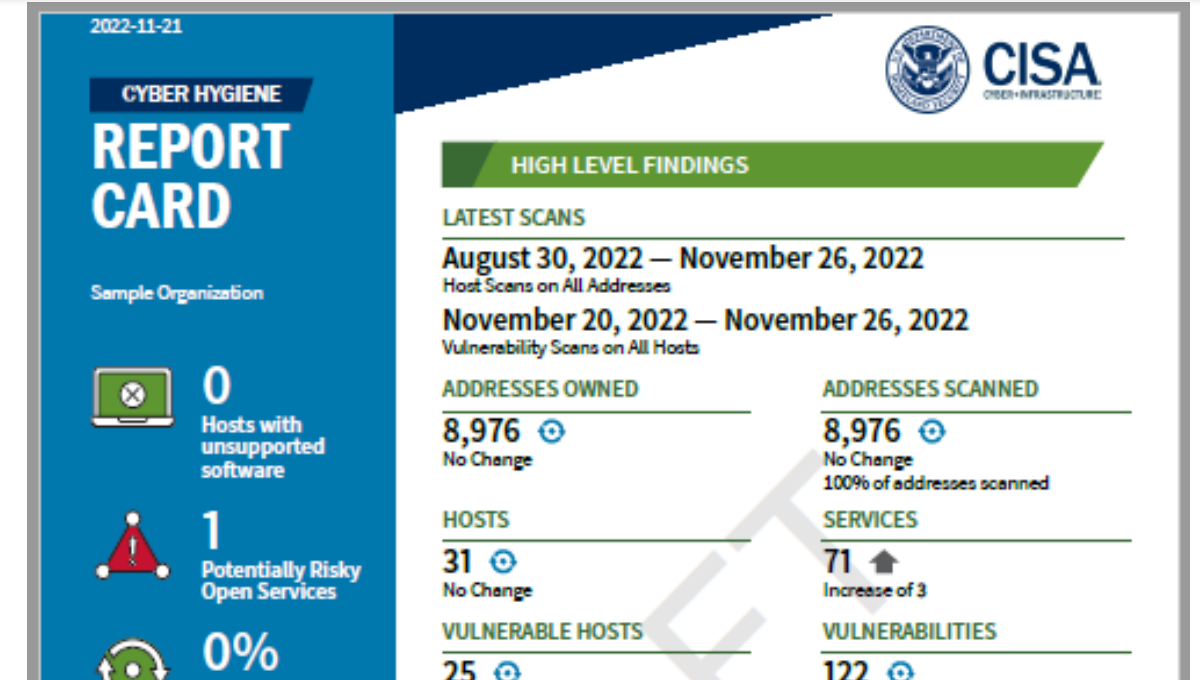
CISA Cyber Scan Water
Read more: CISA Cyber Scan WaterCISA has announced a free (as in beer) service to scan water systems for vulnerabilities. Agilicus has used this scan for a year, receiving weekly reports.
-

Terminator Becomes National Standard
Read more: Terminator Becomes National StandardI’ll be back. Iconic line foreshadows rise of cyber-physical-systems. Terminator trifecta of physical machines, artificial intelligence, cyber-security awry.
-
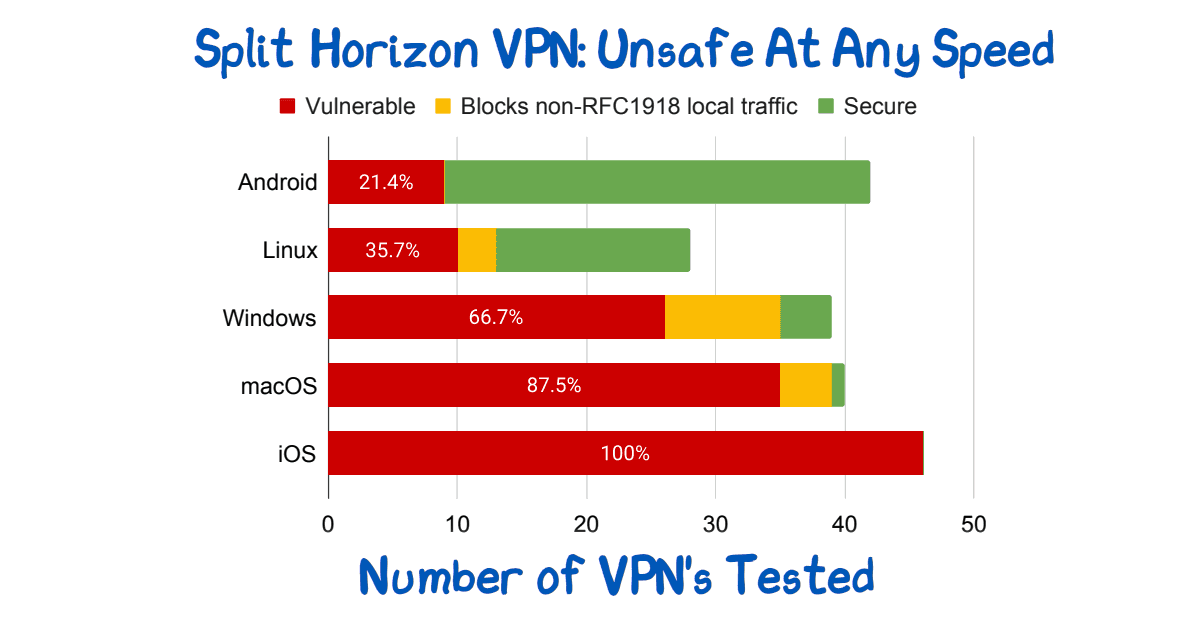
Split Horizon VPN: Unsafe At Any Speed
Read more: Split Horizon VPN: Unsafe At Any SpeedSplit Horizon VPN’s are used to avoid breaking video conferencing. They are unsafe. See paper for route injection issues.
-

NIST sp 800-63A: Introduce Yourself
Read more: NIST sp 800-63A: Introduce YourselfWho are you? Identity involves knowing who you are, and then later proving it. NIST sp 800-63A enrollment is the first step, let’s talk about that!
-
Bring Your Own Device in Agilicus AnyX
Read more: Bring Your Own Device in Agilicus AnyXWe’ll help you understand the benefits of BYOD and the robust, secure support Agilicus AnyX offers so you are equipped with everything you need to allow it.
-
Auto-Creating Users in Agilicus AnyX
Read more: Auto-Creating Users in Agilicus AnyXAgilicus AnyX allows for auto-creating users that simplifies the process and enhances efficiency. We’ll help you understand the benefits & use cases.
-

Using Groups for Assigning Role-Based Permissions
Read more: Using Groups for Assigning Role-Based PermissionsWe’ll help you understand the benefits of assigning role-based permissions using groups in Agilicus AnyX and the advantages of this approach.
-

Diagnosing User Issues with Audits
Read more: Diagnosing User Issues with AuditsWe’ll help you explore the importance of audits in diagnosing user issues and how using them in Agilicus AnyX empowers admins to resolve problems efficiently.
-
VNC and RDP in Agilicus AnyX: Which is Right for Me?
Read more: VNC and RDP in Agilicus AnyX: Which is Right for Me?You have two different choices for how to enable a Desktop resource for your users: VNC and RDP. We’ll help you determine which one is right for you.